A method and system for detecting intrusion attacks of serial decentralized concealment threats
A technology of intrusion attack and detection method, which is applied in the direction of transmission system, digital transmission system, security communication device, etc., and can solve the problem that defenders cannot obtain attack samples, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The present invention will be further described in detail below in conjunction with specific embodiments and accompanying drawings, but the protection scope of the present invention is not limited to these embodiments, and all changes or equivalent substitutions that do not depart from the concept of the present invention are included within the protection scope of the present invention .
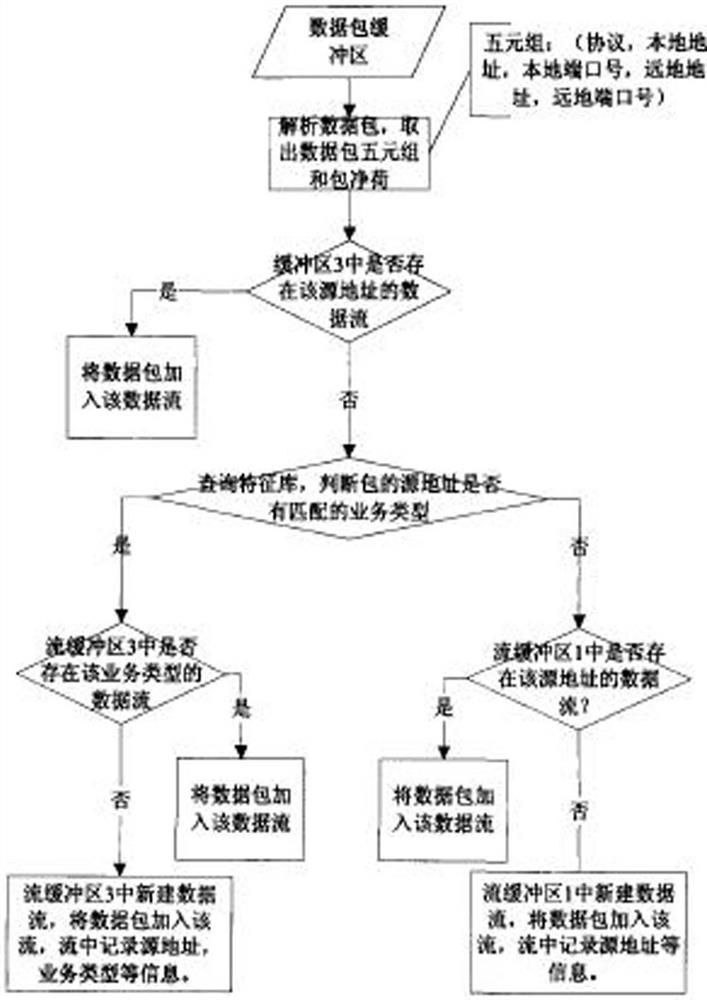
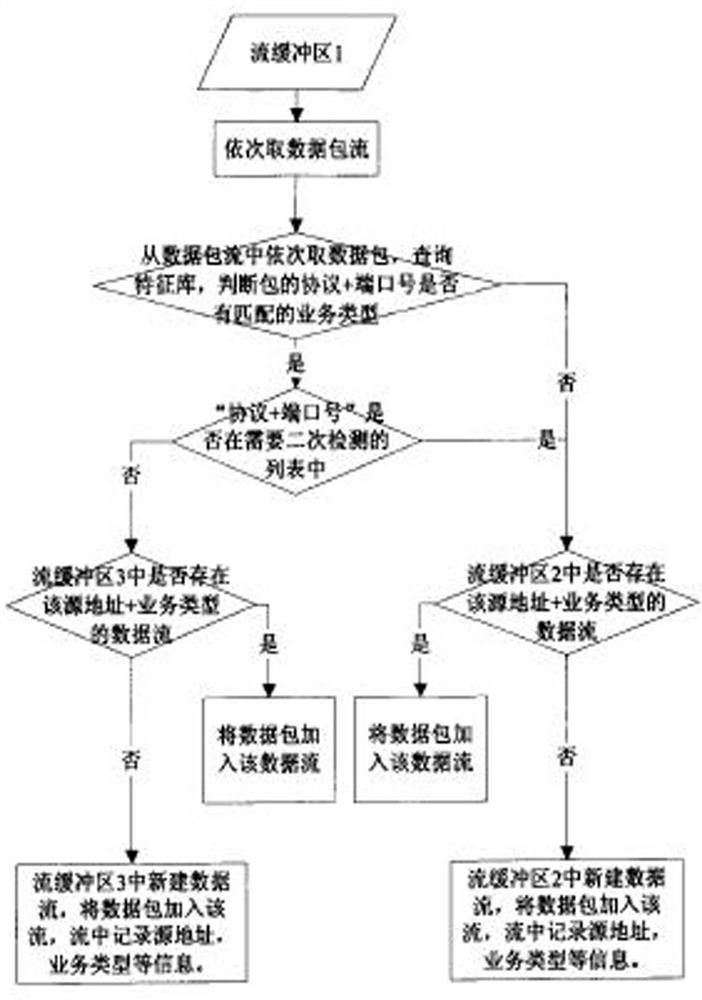
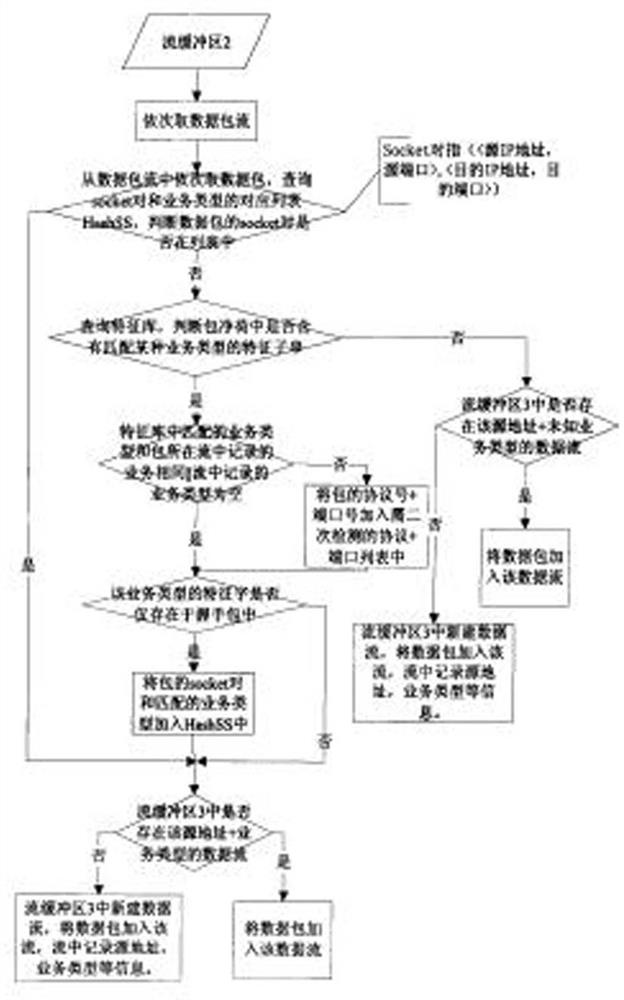
[0056] The invention discloses a method for detecting serial decentralized and hidden threat intrusion attacks. The detection method detects unknown abnormal traffic in network traffic through the research of scalable application identification technology and hidden threat analysis and detection technology.
[0057] The scalable application identification technology is based on the deep packet inspection technology, which expands the scope of application layer identification, evaluates different applications from various dimensions, mines more information in network traffic, and provi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com