Testing method and system for attacking machine learning products
A technology of machine learning and testing methods, applied in transmission systems, electrical components, etc., can solve problems such as lack of test results, singleness, and traditional testing methods, and achieve the effects of ensuring information security, improving security, and novel angles
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
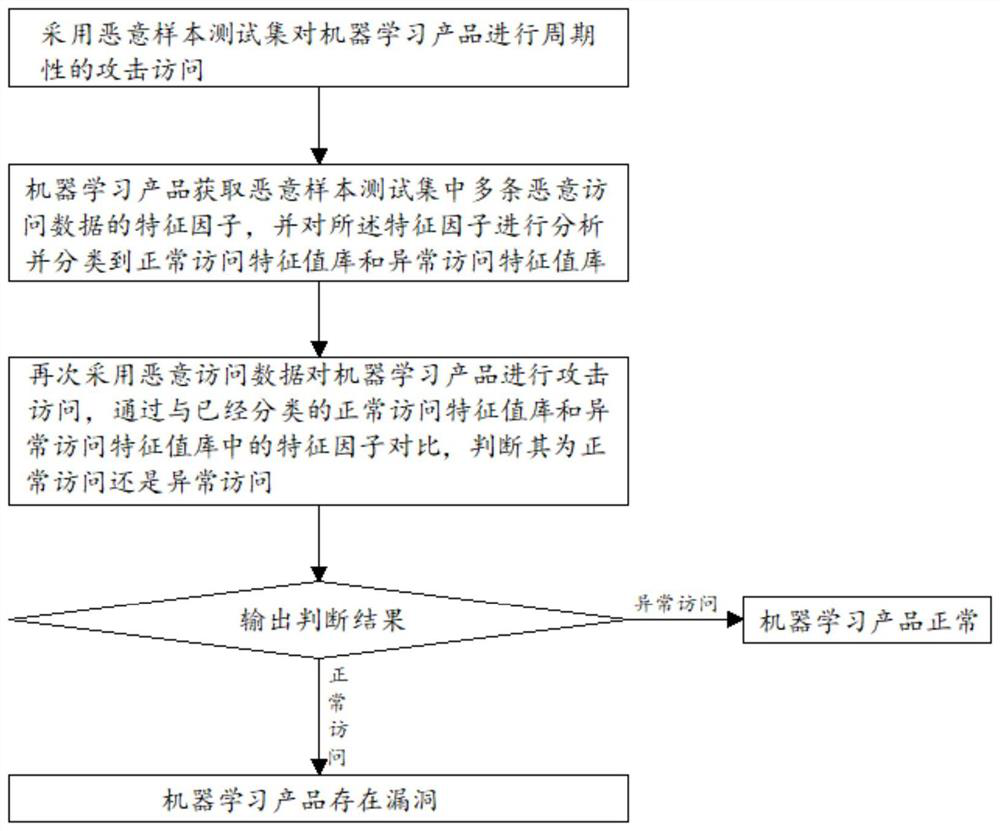
[0025] like figure 1 As shown, a test method for attacking machine learning products includes the following steps:
[0026] Preconditions: the attacked machine learning product server (for example, a firewall), a PC with an operating system of WIN7 or WIN8 or WIN10 or Linux;
[0027] Step 1. Use the malicious sample test set to conduct periodic attack access to the machine learning product. The malicious test sample set includes multiple pieces of malicious access data; wherein, the number of malicious access data for attack access to the machine learning product is greater than that of the same period The normal visit volume of machine learning products, the cycle of malicious sample test set attack access to machine learning products is longer than the cycle of the defense algorithm of the machine learning products;
[0028] Step 2: The machine learning product obtains the characteristic factors of multiple pieces of malicious access data in the malicious sample test set, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com