Network attack detection method, device and equipment and storage medium
A network attack and detection method technology, applied in the network field, can solve problems such as poor accuracy of network attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
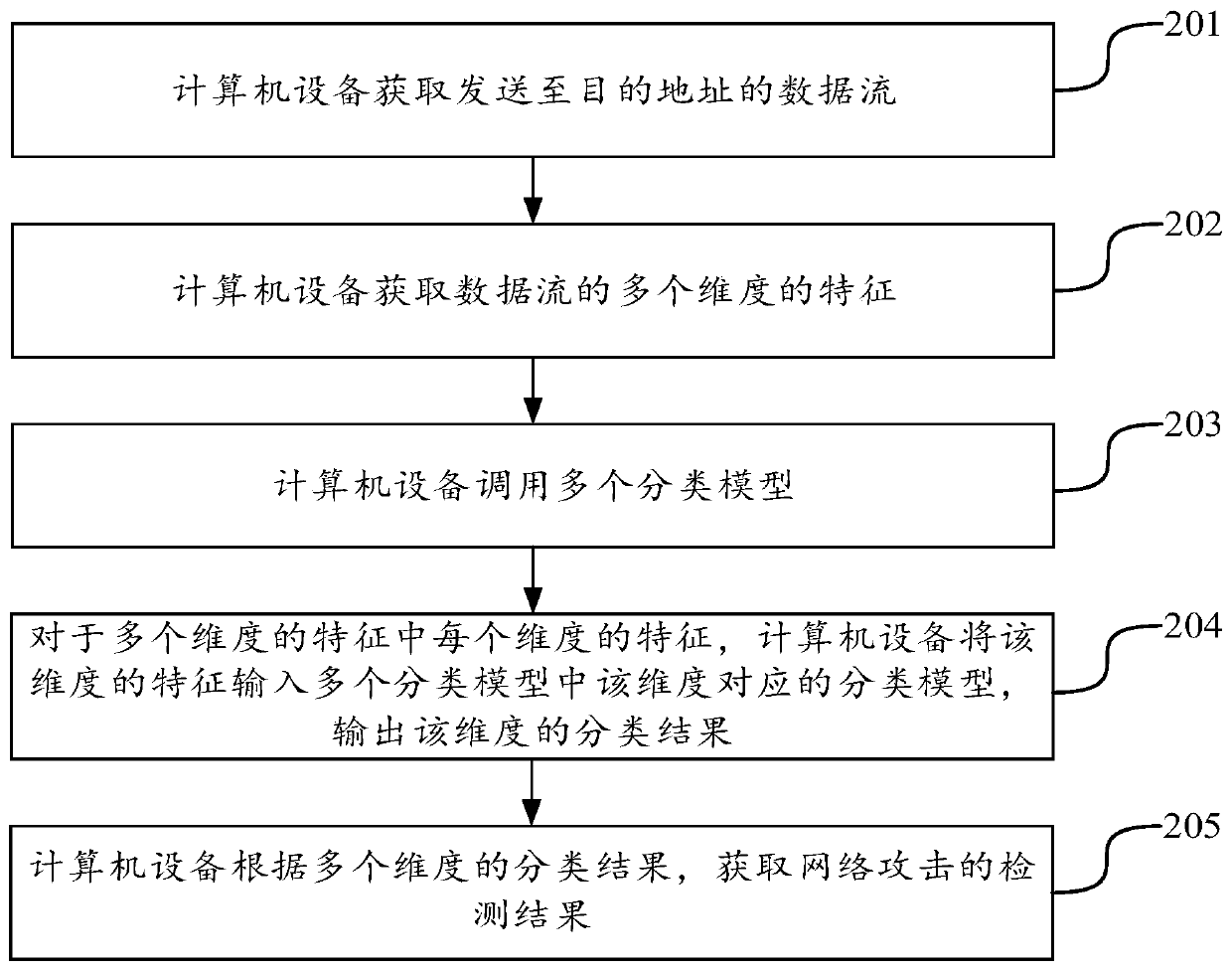
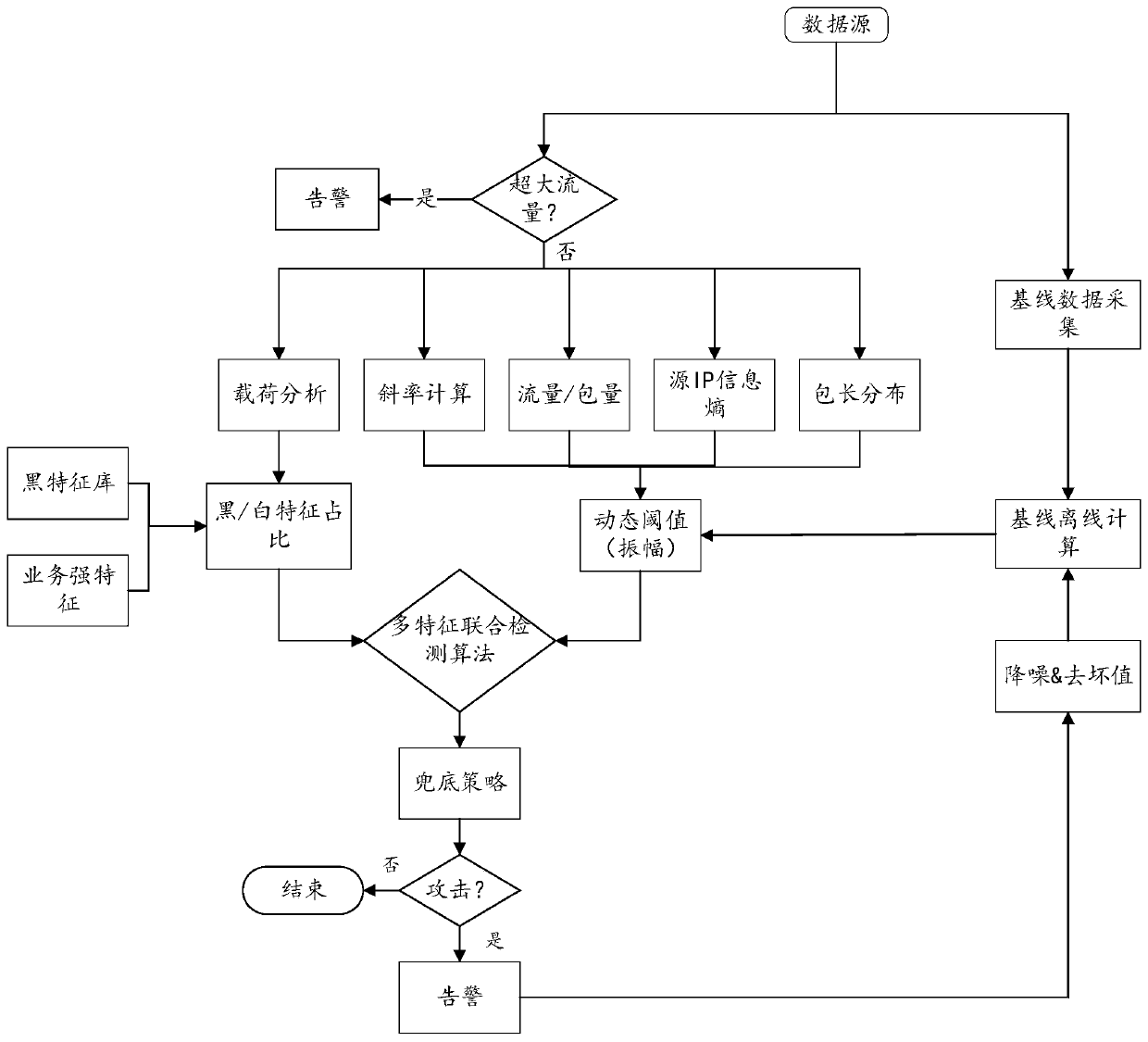
[0069] In order to make the object, technical solution and advantages of the present invention clearer, the implementation manner of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0070] The terminology of this application is briefly introduced as follows:
[0071] Distributed Denial of Service (full name: Distributed Denial of Service, abbreviation: DDoS) attack is a network attack method used to paralyze the server. The essence of a DDoS attack is to use a distributed client to initiate a large number of seemingly legitimate requests to the server, thereby consuming or occupying a large amount of resources of the server for a long time, so that the server refuses to provide services to legitimate users. There are many types of DDoS attacks, which can be mainly divided into two types: resource consumption type and bandwidth congestion type. Resource-consuming DDoS attacks refer to using reasonable service requ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com