Network user identity recognition method
A network user and identity recognition technology, which is applied in character and pattern recognition, instruments, computing, etc., can solve the problems of in-depth mining without identity characteristics, insufficient information utilization, and insufficient granularity of user groups, so as to improve efficiency and improve The effect of precision
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The technical solutions in the embodiments of the present invention will be described clearly and in detail below with reference to the drawings in the embodiments of the present invention. The described embodiments are only some of the embodiments of the invention.
[0042] The technical scheme that the present invention solves the problems of the technologies described above is:
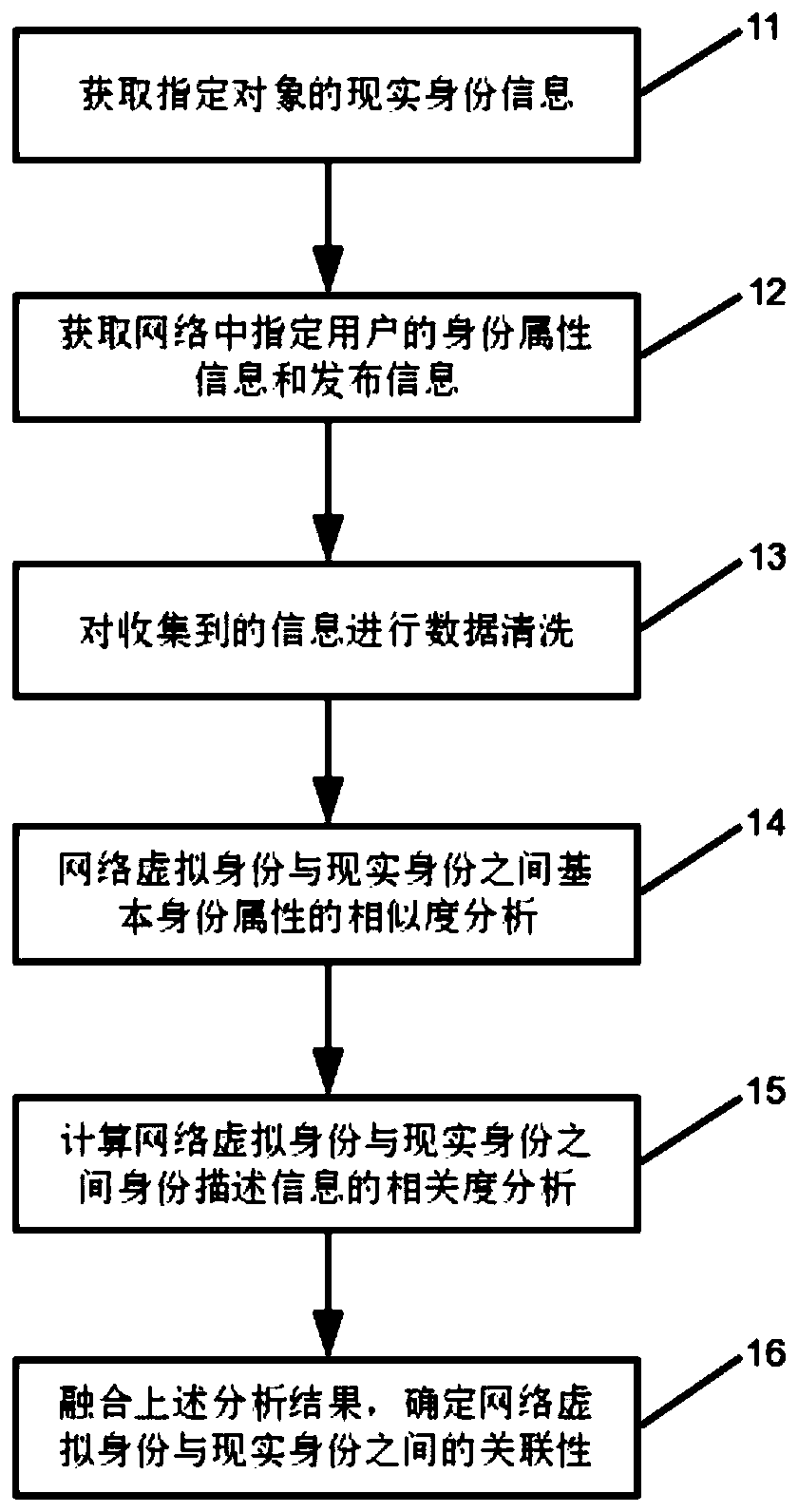
[0043] Such as figure 1 As shown, the specific steps of a network user identification method:
[0044] Step 11: Obtain the real identity information of the specified object.
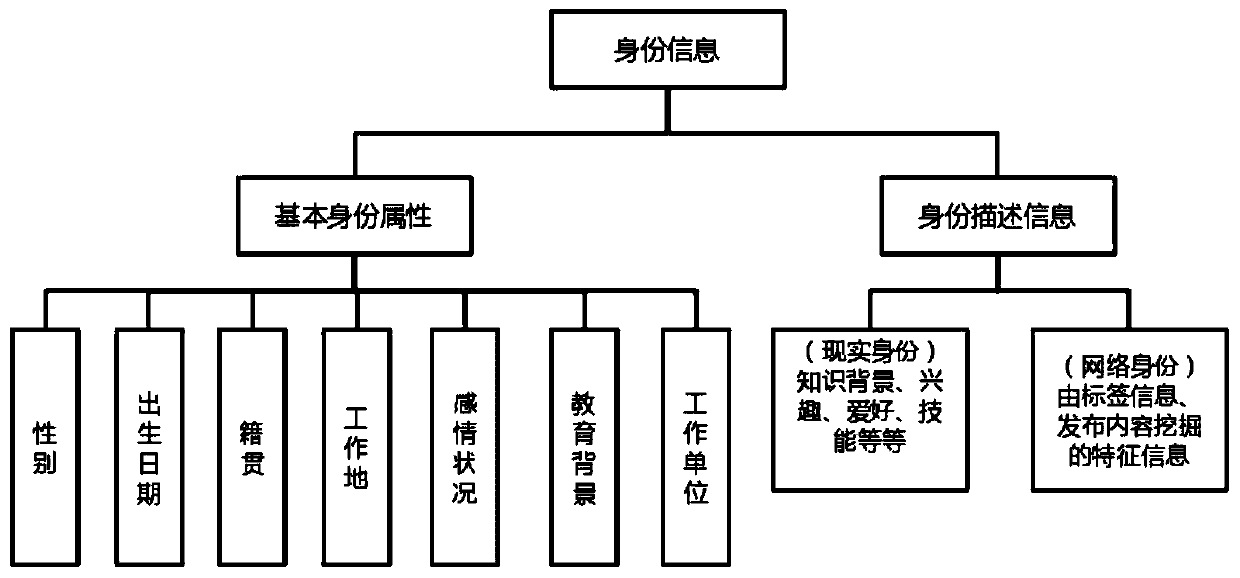
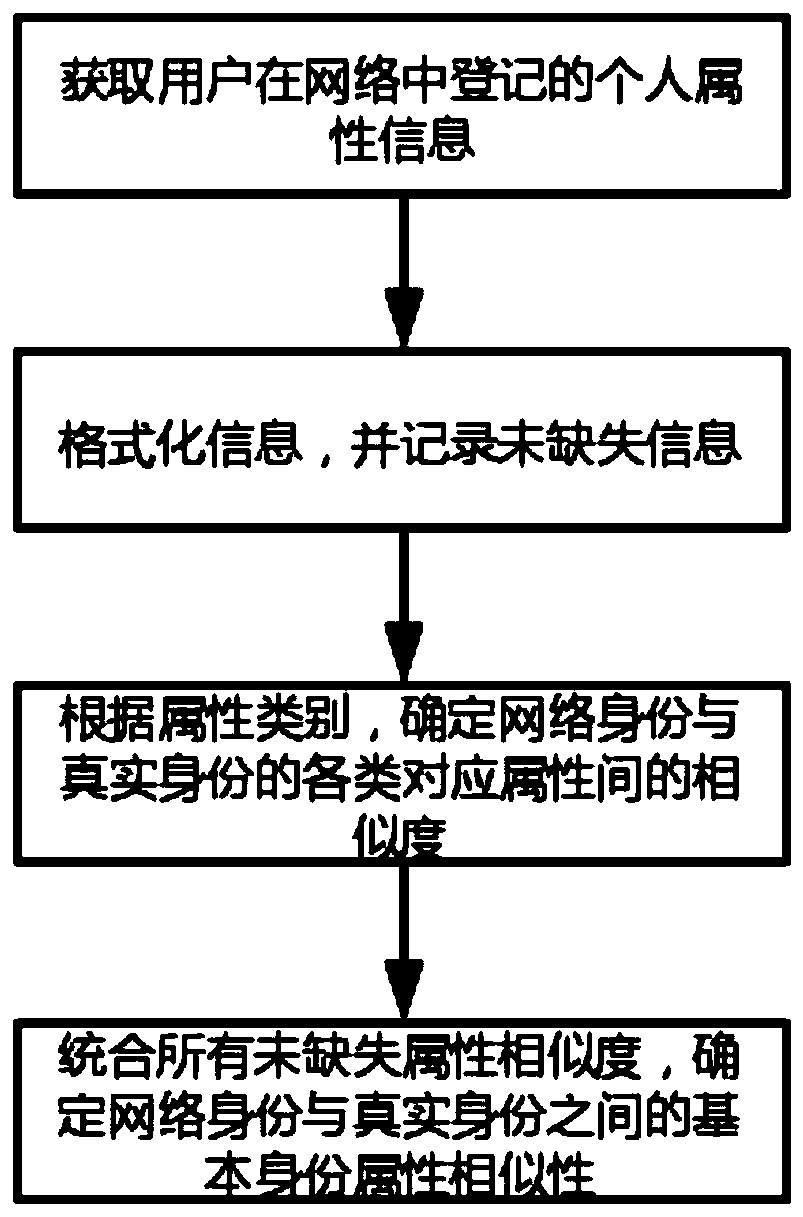
[0045] Such as figure 1 As shown, a person's identity information contains two types of information: one is basic identity information, and the other is identity description information. Basic identity information includes seven attribute information: gender, date of birth, place of origin, place of work, relationship status, educational background, and work unit. The identity description information of real ident...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com