Internet of Things multi-source cross composite authentication method based on block chain
An authentication method and blockchain technology, applied in the field of multi-source cross-composite authentication of the Internet of Things based on blockchain, can solve problems such as confusion, high cost, data permanence and security cannot be guaranteed, and achieve easy Effects of integration, reliable identification and authentication, protection of integrity and availability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
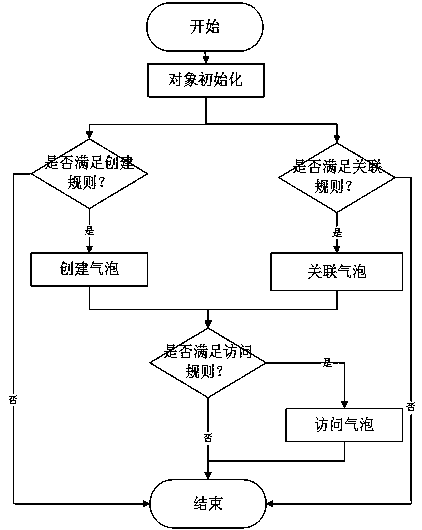
[0036] The following are specific embodiments of the present invention and in conjunction with the accompanying drawings, the technical solutions of the present invention are further described, but the present invention is not limited to these embodiments.
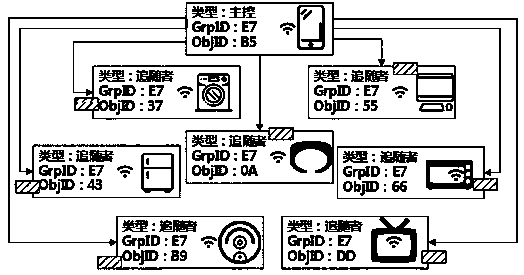
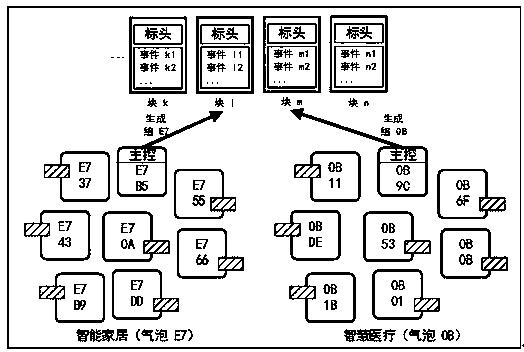
[0037] Each device can only communicate with devices in the same area, and treats other devices outside the area as malicious devices. In these zones, all members can trust each other, while it is protected and inaccessible to non-member devices. In order to realize such a method, the present invention innovatively proposes to use the "bubble" analogy to build a safe virtual area based on the blockchain, relying on the public blockchain rather than the private blockchain that implements the smart contract, so that the IoT ecosystem is open to any User is open. Communications in IoT are considered transactions and must be verified by this blockchain to be considered. For example, if device A sends a message to device B, (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com