Android malicious behavior dynamic detection method based on binary dynamic instrumentation
A dynamic detection and malicious technology, applied in the direction of program control design, program control devices, instruments, etc., can solve the problems of extracting software behavior characteristics, coarse detection granularity of malicious behavior, unable to monitor code insertion and packing, etc., and achieve detailed detection conclusions Granularity, high accuracy, and the effect of improving detection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to better illustrate the purpose and advantages of the present invention, the implementation of the method of the present invention will be further described in detail below in conjunction with examples.
[0030] The specific process is:
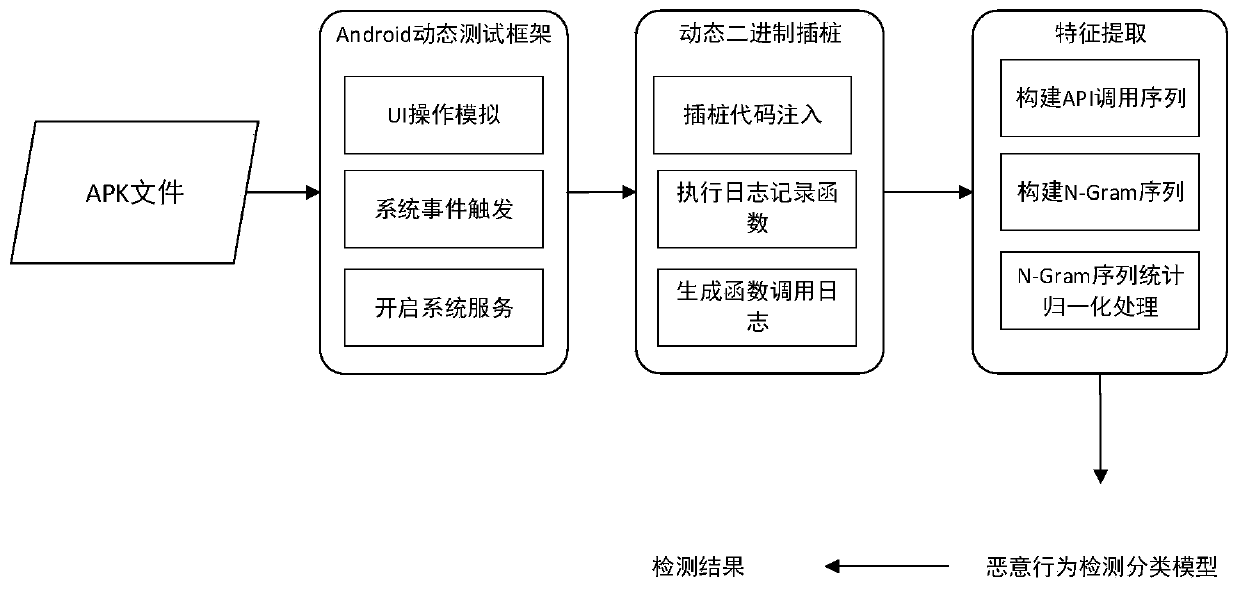
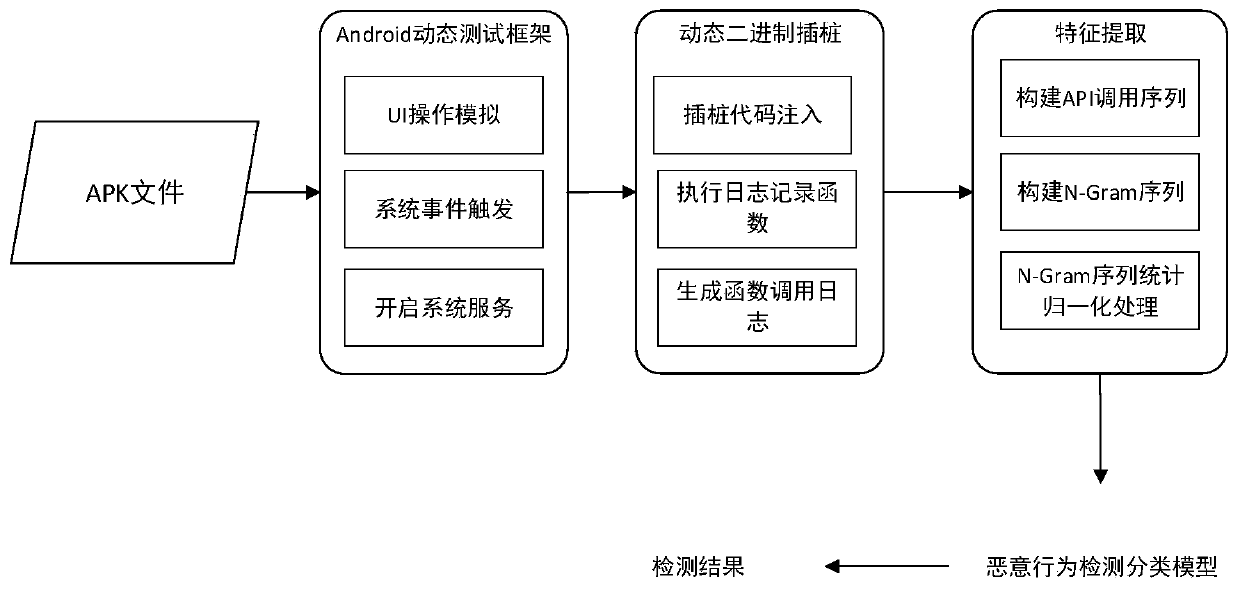
[0031] Step 1, use the Android dynamic detection framework to trigger the behavior of the application software.
[0032] Step 1.1, install the apk file of the tested software on the Android physical machine or virtual machine.
[0033] Step 1.2, use the Android dynamic monitoring framework to trigger all potential malicious behaviors of the software, the specific method is: use the Monkey automated testing tool to simulate user UI operation behavior; use the adb tool set to simulate the triggering of system events; use the adb tool set to simulate system service broadcasts, Actively enable system services.
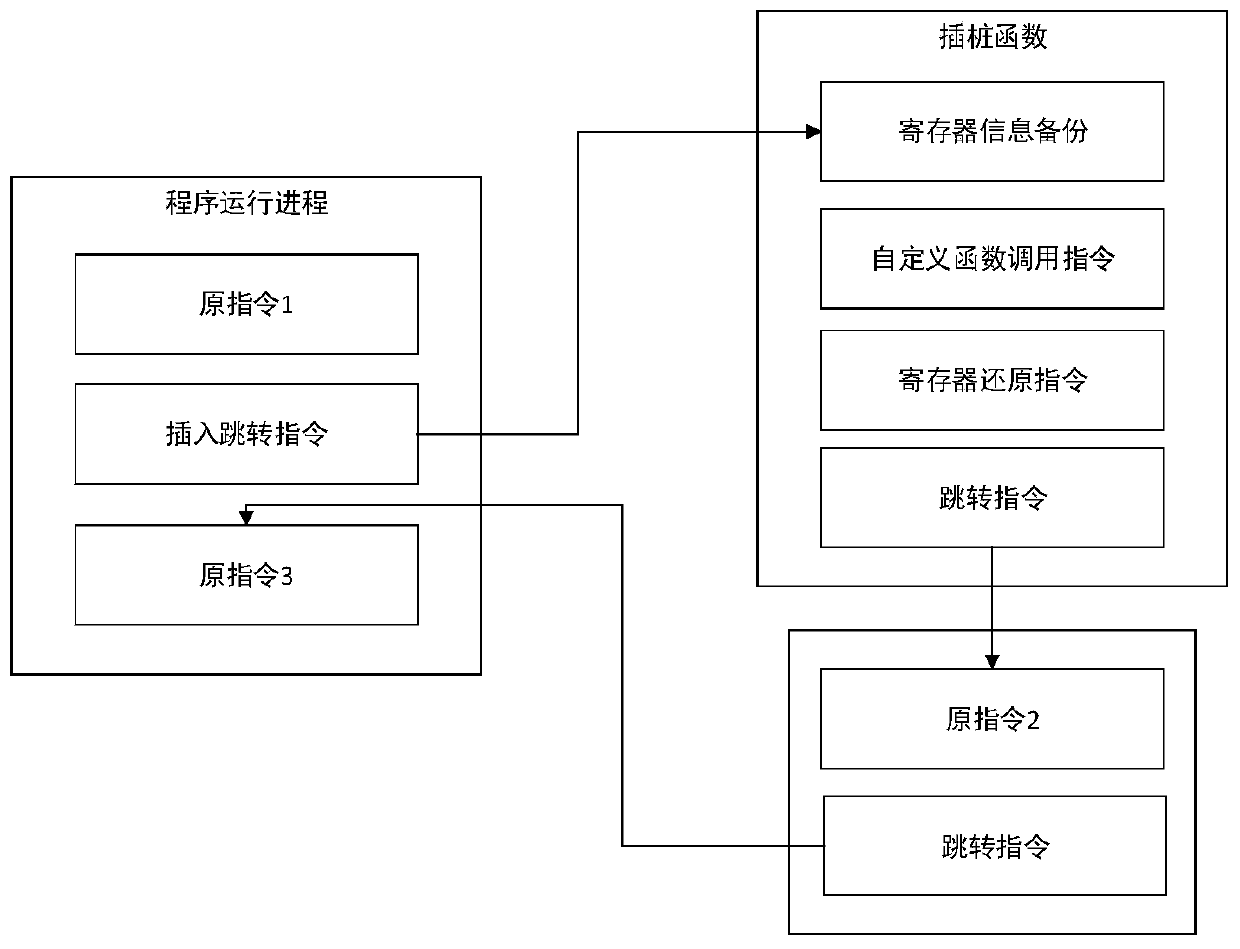
[0034] Step 2, collect the function running logs of the software through binary dynamic instrumentation technology. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com