Authentication method and device for video stream address
A video streaming and authentication technology, applied in the computer field, can solve the problem of low security and achieve the effect of improving security and increasing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0054] It should be noted that the method provided in this embodiment is applied to a client, and the client and the server are connected through a network to realize communication; in the specific implementation process, the client can be applied to a mobile terminal device ( For example, mobile phones, tablet computers), and can also be applied to fixed terminal devices (such as desktop computers), and there is no limitation here.
[0055] This embodiment provides an authentication method for a video stream address, and the method is applied to a client, such as figure 1 As shown, the method includes:
[0056] Step S101: Send login information to the first server and the second server, so that the first server generates first information for authentication and user authentication information based on the login information, and uses a preset encryption key to encrypt the Encrypt the first information used for authentication to generate second information used for authenticat...
Embodiment 2
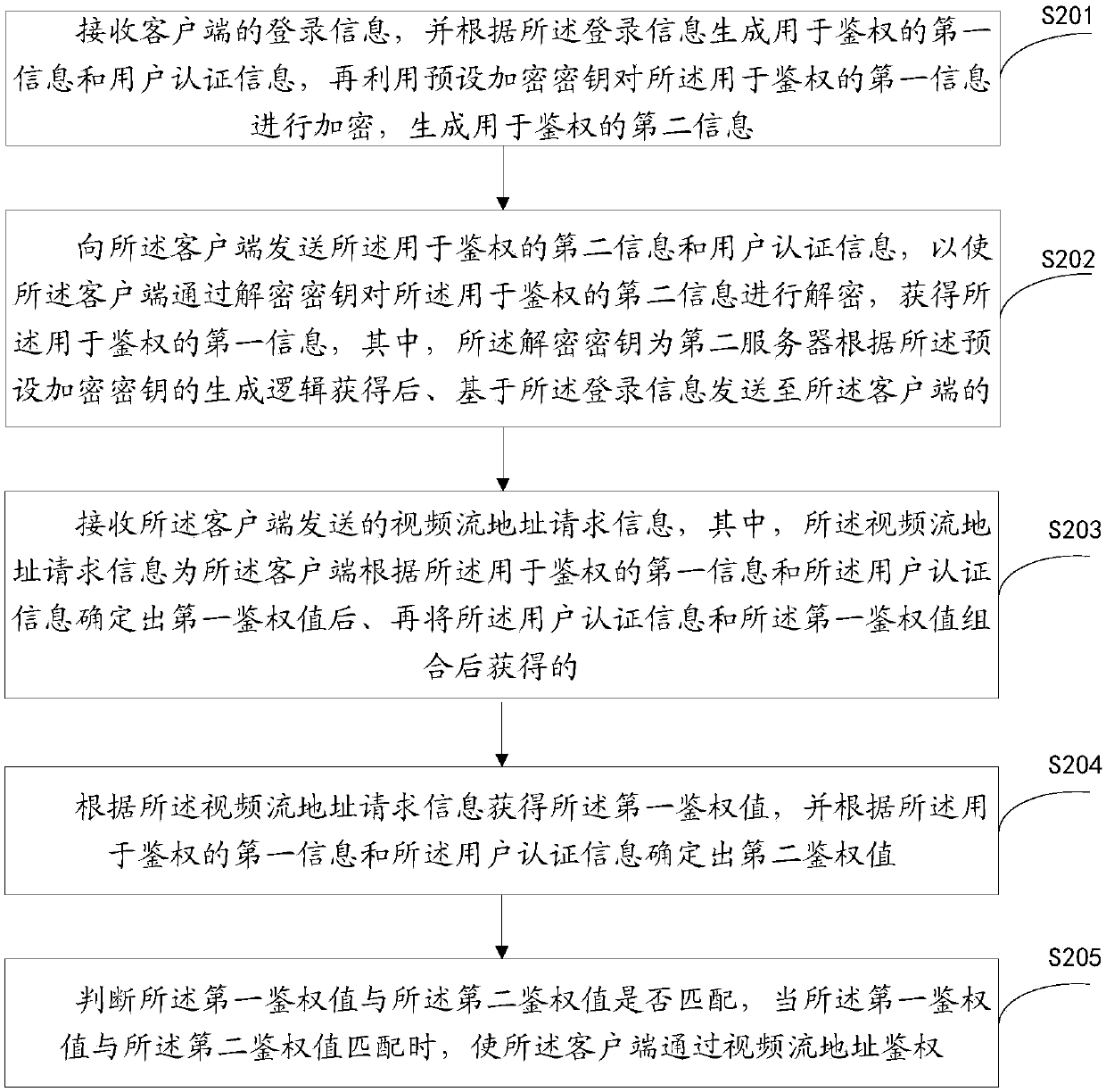
[0101] This embodiment provides an authentication method for a video stream address, which is applied to the first server, such as figure 2 As shown, the method includes:
[0102] Step S201: receiving the login information of the client, and generating first information for authentication and user authentication information according to the login information, and then encrypting the first information for authentication with a preset encryption key, generating second information for authentication;
[0103] In the first embodiment, it has been introduced in detail that the first server generates the first information for authentication and user authentication information according to the login information of the client, and uses the preset encryption key pair to encrypt the first information for authentication. The specific process of encrypting and generating the second information for authentication will not be repeated here.
[0104] Step S202: Send the second information...
Embodiment 3
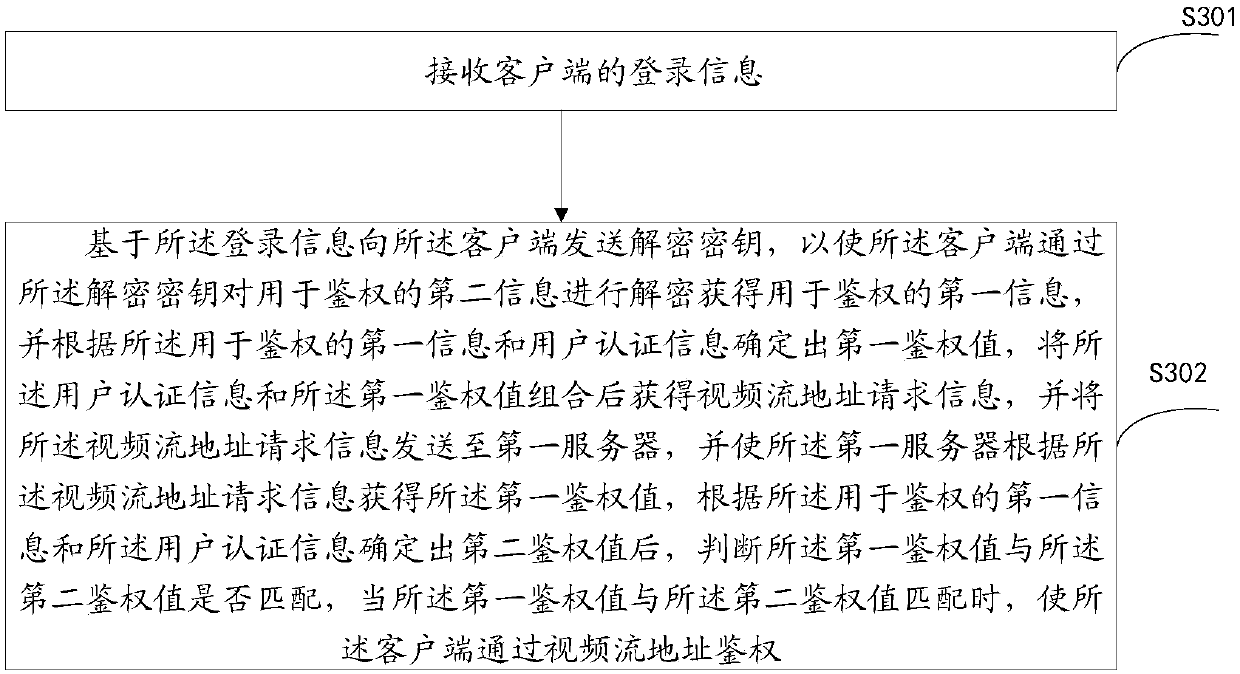
[0121] This embodiment provides an authentication method for a video stream address, such as image 3 As shown, the method includes:
[0122] Step S301: receiving the login information of the client;
[0123] Step S302: Send a decryption key to the client based on the login information, so that the client can decrypt the second information for authentication with the decryption key to obtain the first information for authentication , and determine a first authentication value according to the first information used for authentication and user authentication information, combine the user authentication information and the first authentication value to obtain video stream address request information, and Sending the video stream address request information to the first server, and making the first server obtain the first authentication value according to the video stream address request information, and according to the first information used for authentication and the After t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com