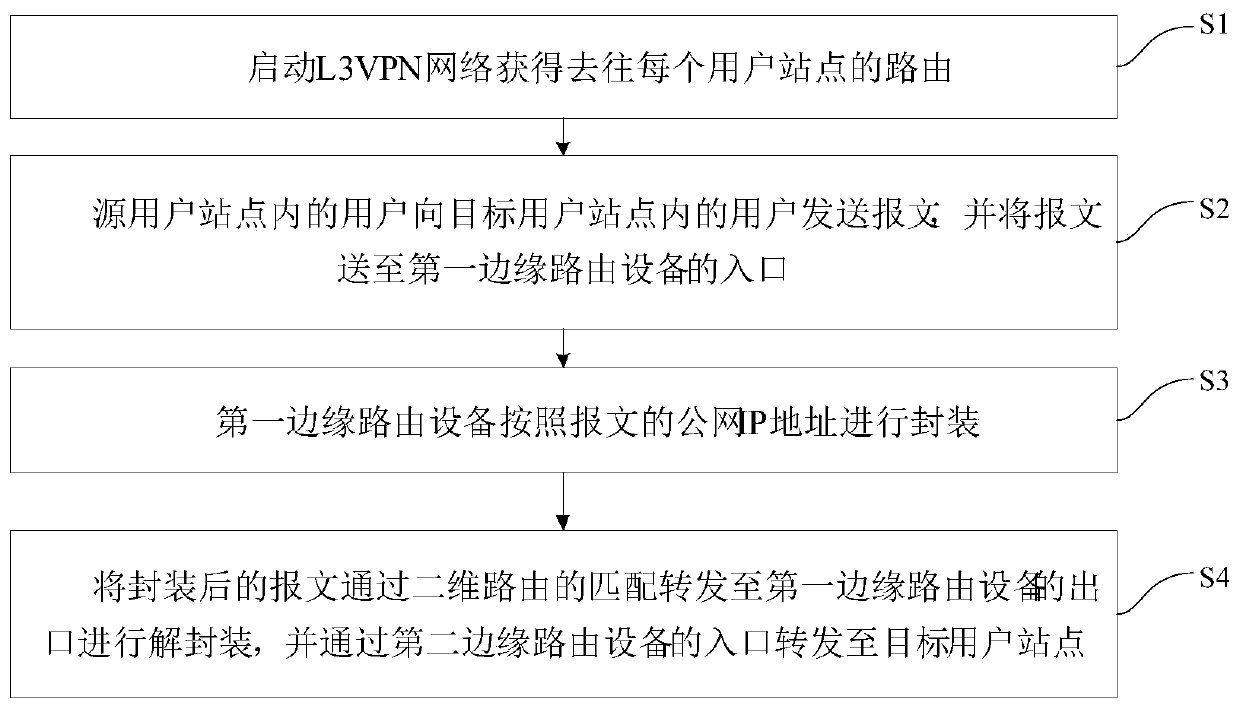
Method and system for realizing L3VPN based on two-dimensional routing protocol
A routing protocol and routing technology, applied in the field of implementing L3VPN based on two-dimensional routing protocol, can solve the problems of limited functions and services, reducing the flexibility of network routing and forwarding, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
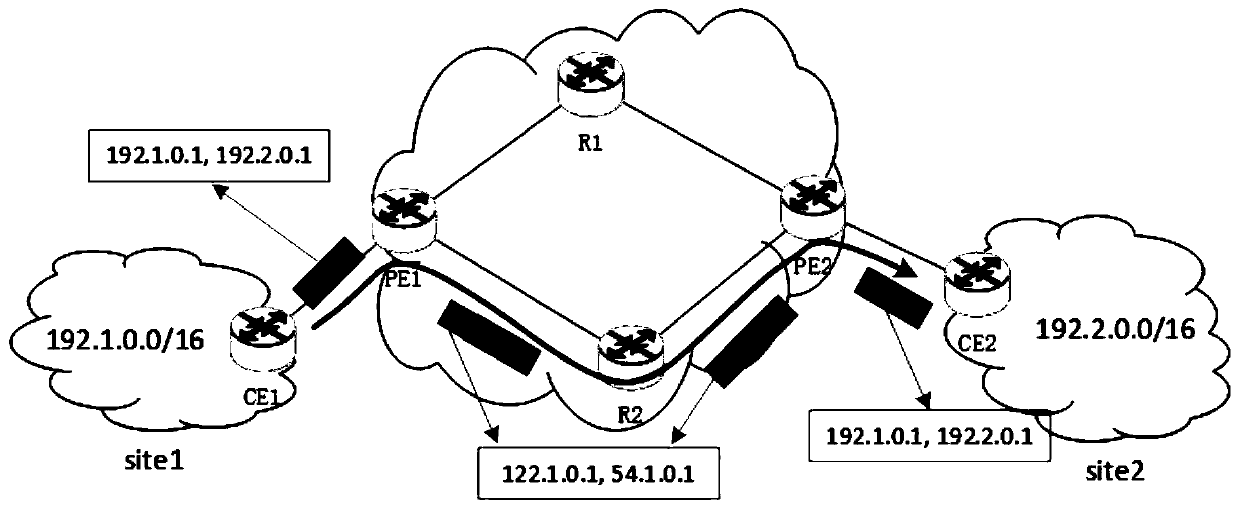
[0055] Example 1, such as image 3 As shown, site1 and site2 are respectively connected to a carrier network and belong to the same VPN service. The intranet IP segment of site1 is 192.1.0.0 / 16, and the intranet IP segment of site2 is 192.2.0.0 / 16. The routers in the carrier's network run two-dimensional routing. Assume that a packet with source address 192.1.0.1 and destination address 192.2.0.1 is sent from site1 to site2. CE1 will send the packet to PE1. PE1 finds out the pair corresponds to the public network pair, and then the message is according to Figure 4 Encapsulate in the IPIP mode shown, that is, insert an IP header carrying a public network address pair into the original. It should be pointed out that the public network address corresponding to the mapping relationship can ensure that the packet is forwarded to the destination egress route PE on the one hand, and on the other hand, it is convenient to ensure the routing policy. For example, in this example, it...
example 2
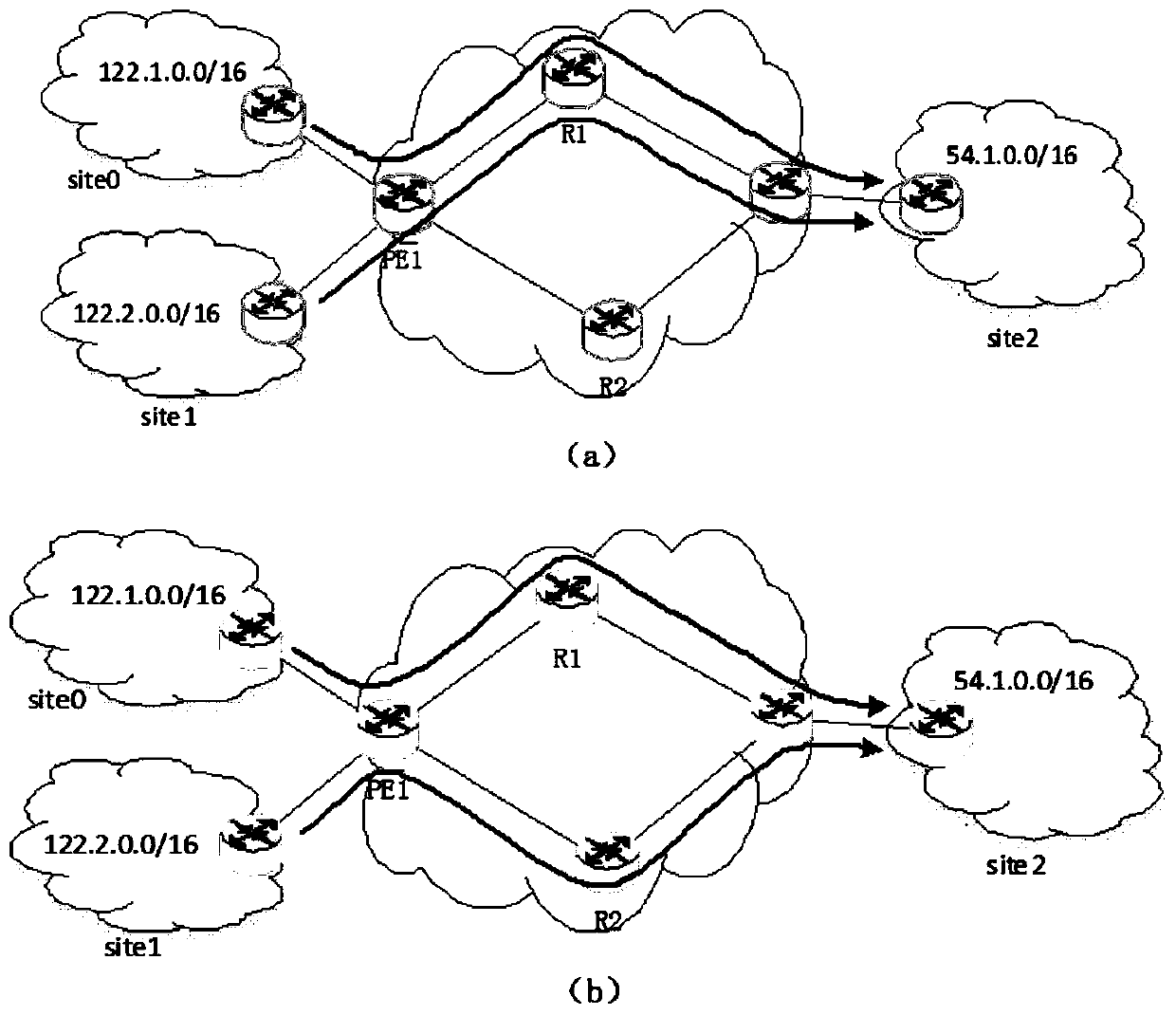
[0056] Example 2, such as Figure 5 As shown, in the embodiment of the present invention, the message sent from site1 to site2 carries the address pair , and is encapsulated at PE1 and then forwarded to the egress route PE2. To achieve network traffic load balancing, PE1 can encapsulate original packets according to a certain proportion of public network address pairs. For example, in this example, for packets carrying , PE1 50% of the packets are encapsulated as packets, these packets will reach PE2 through router R1, and the other 50% of the packets are encapsulated as packets, these The packet will reach PE2 through router R2, thus realizing the effect of load balancing.
example 3
[0057] Example three, such as Figure 6 Shown is a scenario of distinguishing intranet services. For example, in site1, a message with an address of 192.1.1.0 / 24 is common customer information, which can be forwarded to the destination site2 through a regular path (path through R1), while a message with an address of 192.1.1.0 / 24 The message with the address of 192.1.2.0 / 24 is confidential information, and it is necessary to select a highly secure path (the path through R2, such as a security detection device deployed) for separate forwarding, and then reach the destination site2. Therefore, the customer requirement in the embodiment of the present invention is that packets carrying are forwarded to developed PE2 through R1, and packets carrying are forwarded through R2 to developed PE2. PE2. Therefore, when PE1 receives the packet, it needs to match the intranet address pair of the packet, and then encapsulate it into different public network address pairs, so as to reach ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com