Card reader reading permission verification method based on block chain
A verification method and a technology of a card reader, which are applied in the directions of instruments, digital data authentication, and electronic digital data processing, etc., can solve problems such as low security and complex internal modules, and achieve enhanced security, simplified module structure, and enhanced reliability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
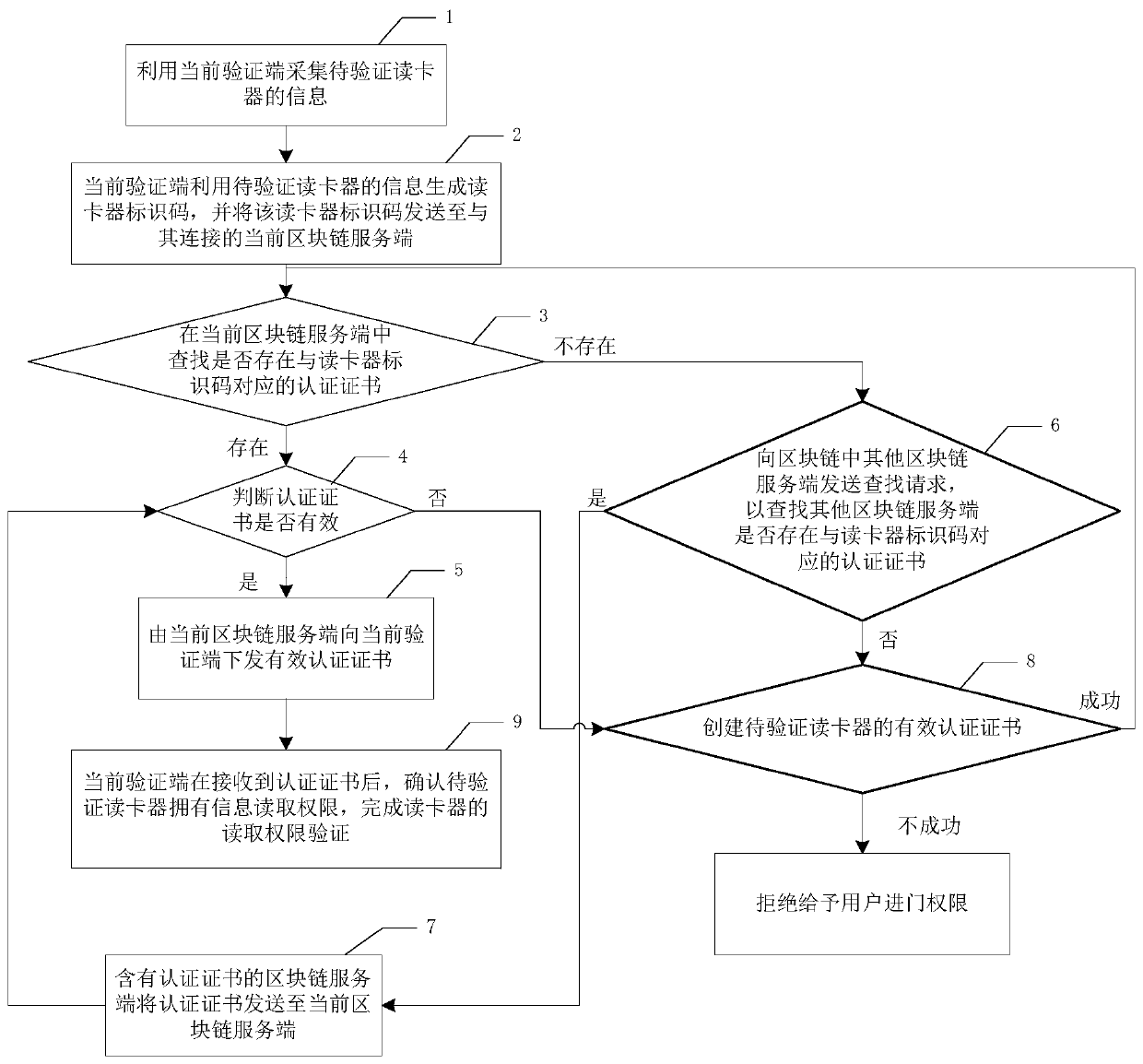
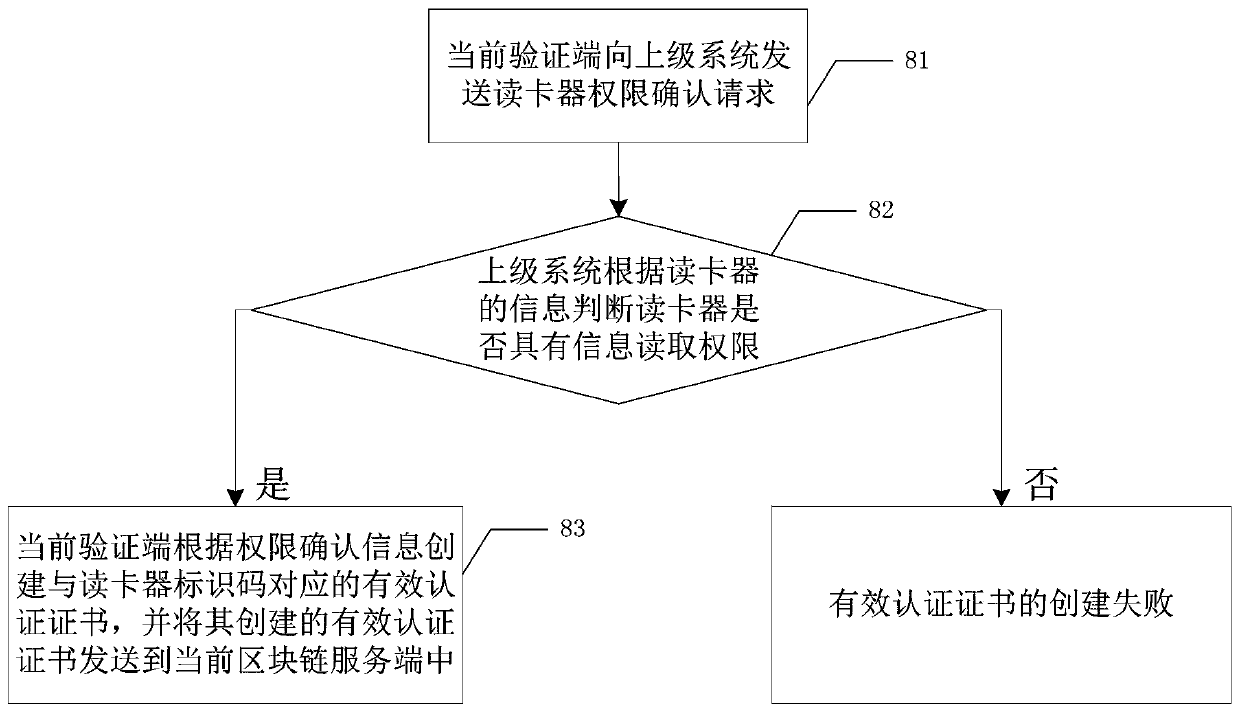
[0029] Specific Embodiment 1: The block chain-based card reader reading permission verification method described in this embodiment requires a verification terminal (ie: a PC connected to the card reader), a card reader, The smart card, the upper-level system, the block chain and the various block chain servers that make up the block chain participate in the completion. As a node that makes up the blockchain, the blockchain server realizes data interaction with the verification terminal. The upper-level system has the authority to approve the card reader information, and can give the card reader permission to read the information in the smart card and complete the data interaction with the verification terminal.
[0030] Specifically, the above method includes the following steps:
[0031] Step 1: Use the current verification terminal to collect the information of the card reader to be verified, the information includes the current card reading time, and the current verificat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com