Terminal information tracing method and device, terminal and medium
A terminal information and terminal technology, applied in the computer field, can solve the problems of weak security protection capability of confidential information and inability to determine information stealer information, etc., to achieve the effects of improving security protection capability, simple and convenient implementation process, and high generation efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
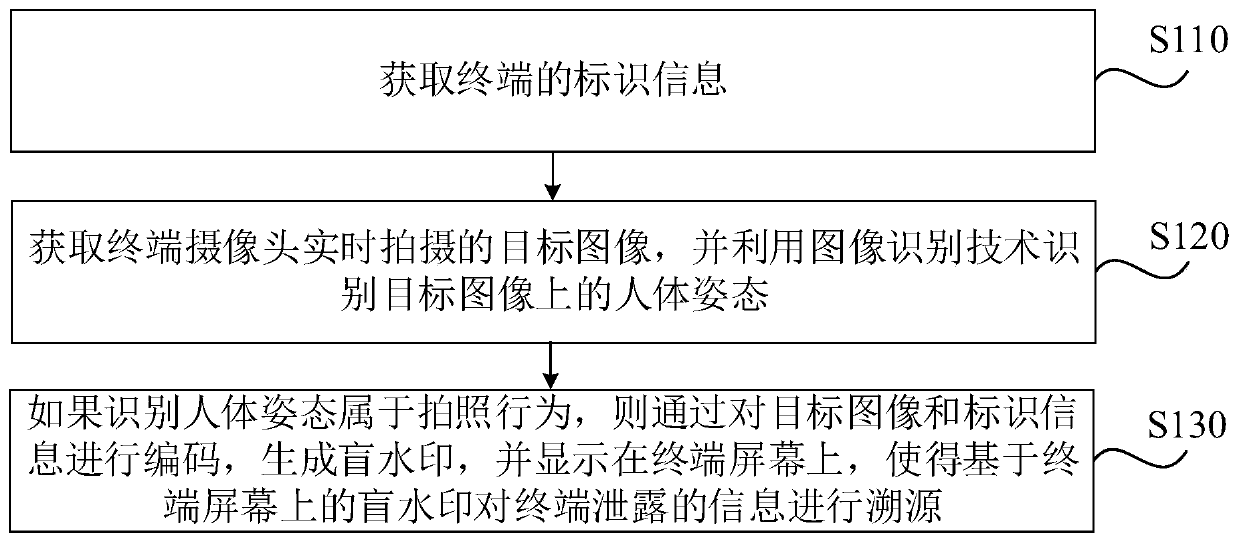
[0026] figure 1 It is a flow chart of the terminal information traceability method provided by Embodiment 1 of the present invention. This embodiment is applicable when someone uses a camera to capture the terminal screen to steal confidential information on the terminal. By analyzing the information image captured by the user, In the case of obtaining a blind watermark to trace the source of information leaked on the terminal, the method can be executed by a terminal information traceability device, which can be implemented in the form of software and / or hardware, and can be integrated on the terminal.
[0027] Such as figure 1 As shown, the terminal information traceability method provided in this embodiment may include:
[0028] S110. Acquire identification information of the terminal.
[0029] In this embodiment, before generating the blind watermark, there is no specific limitation on the acquisition timing of the terminal identification information. For example, the a...
Embodiment 2
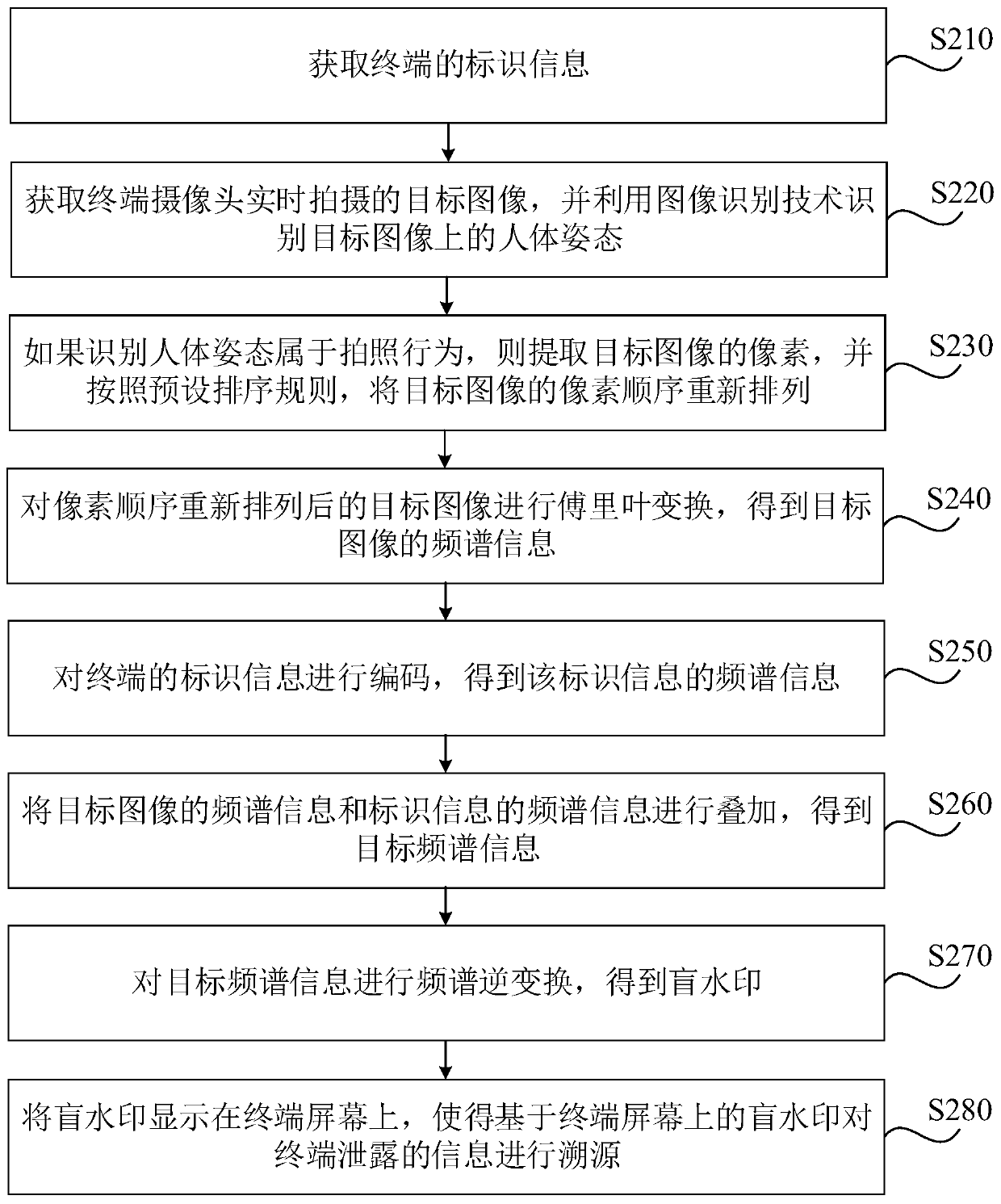
[0048] image 3 It is a flow chart of the terminal information traceability method provided in Embodiment 2 of the present invention, and this embodiment is further optimized on the basis of the foregoing embodiments. Such as image 3 As shown, the method may include:
[0049] S210. Acquire identification information of the terminal.
[0050] S220. Acquire the target image captured by the terminal camera in real time, and use the image recognition technology to identify the human body posture on the target image.
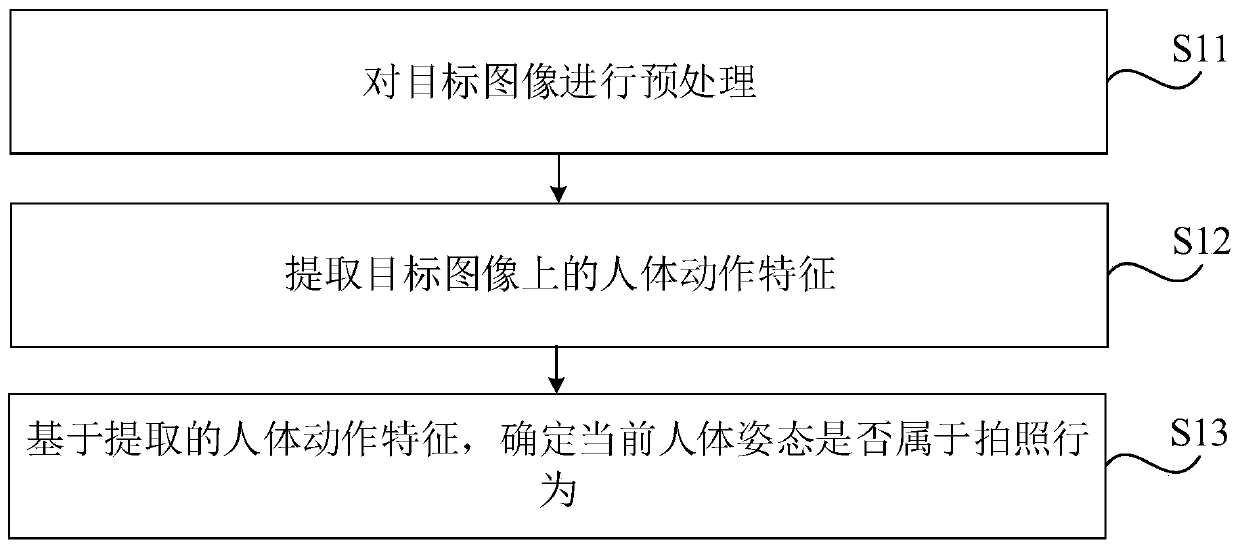
[0051] S230. If recognizing the posture of the human body is a photographing action, extract pixels of the target image, and rearrange the order of the pixels of the target image according to a preset sorting rule.
[0052] For example, using the set key to rearrange the pixel order of the target image according to the corresponding relationship between the key and the pixel arrangement rules is equivalent to improving the confidentiality of the blind watermark i...
Embodiment 3
[0065] Figure 4 It is a schematic structural diagram of the terminal information traceability device provided by Embodiment 3 of the present invention. This embodiment is applicable when someone uses a camera to capture the terminal screen to steal confidential information on the terminal. By analyzing the information image captured by the user, Get the blind watermark, so as to trace the source of the information leaked on the terminal. The device can be implemented in the form of software and / or hardware, and can be integrated on the terminal.
[0066] Such as Figure 4 As shown, the terminal information traceability device provided in this embodiment may include a terminal identification information acquisition module 310, a target image acquisition module 320, and a blind watermark generation and display module 330, wherein:
[0067] Terminal identification information acquisition module 310, configured to acquire identification information of the terminal;
[0068] Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com