A Classification Method for Encrypted Traffic Based on Dual-Channel Convolutional Neural Network
A convolutional neural network and traffic classification technology, which is applied in the field of network security and information, can solve problems such as inconsistency in size, and achieve the effect of improving accuracy and strong generalization ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
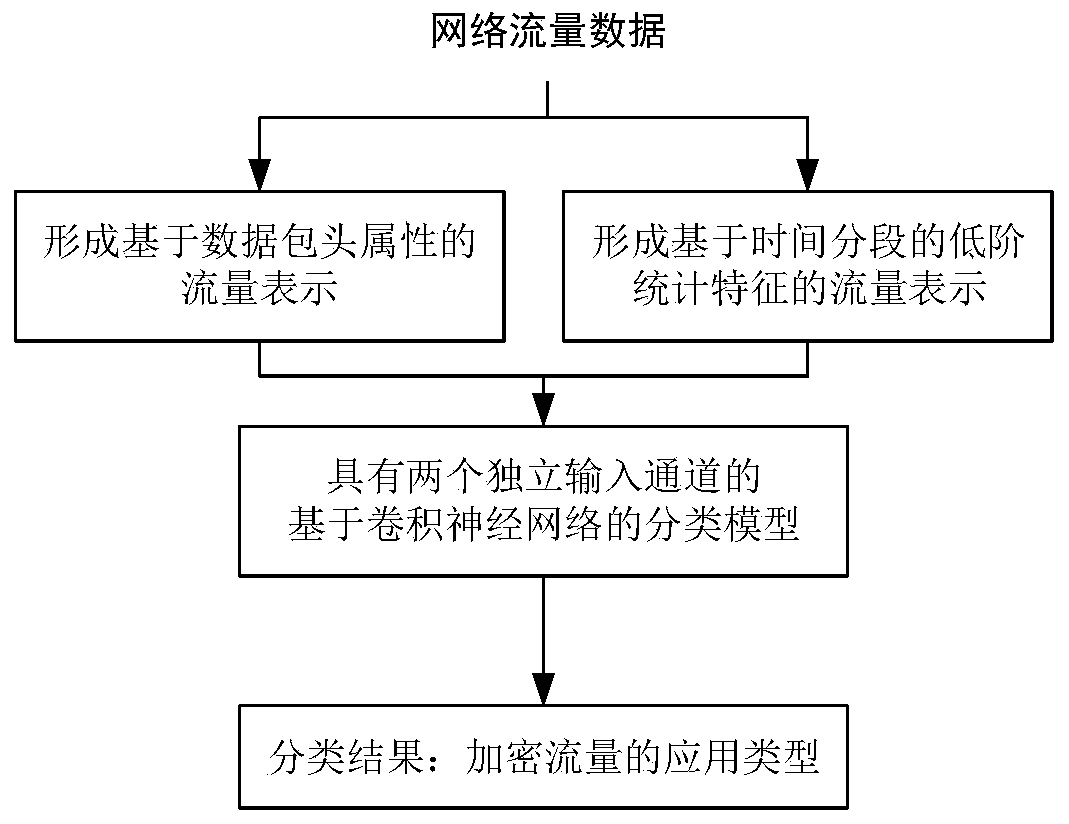
[0031] Such as figure 1 As shown, taking the application type classification of ShadowSocks encrypted traffic as an example, the application types to be divided are video (Video), Tor, mail (Mail), file transfer (File Transfer), audio (Audio) and web page access (Web) categories, including the following steps:
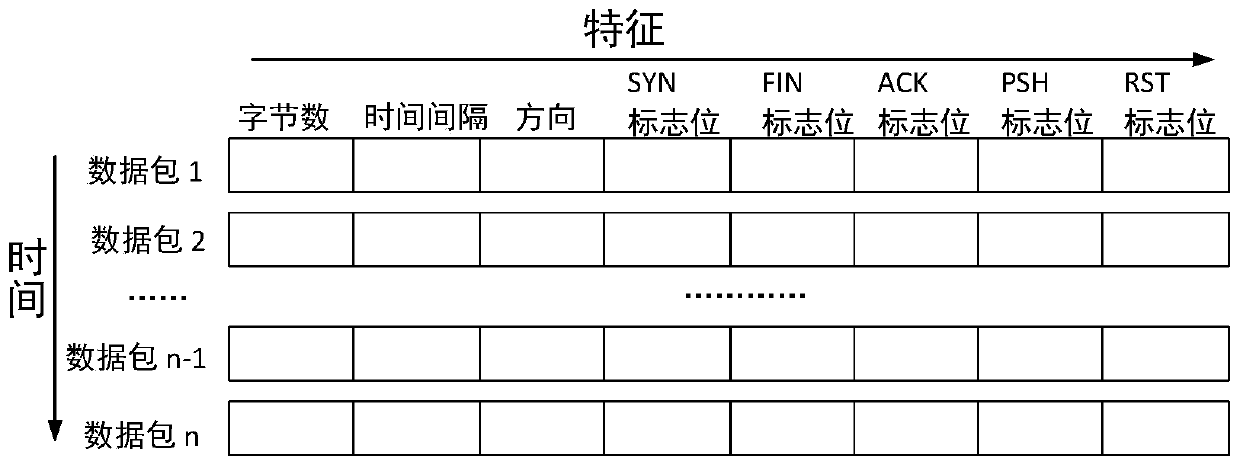
[0032] Step 1: Preprocess the network flow to form a flow representation based on the attributes of the packet header;
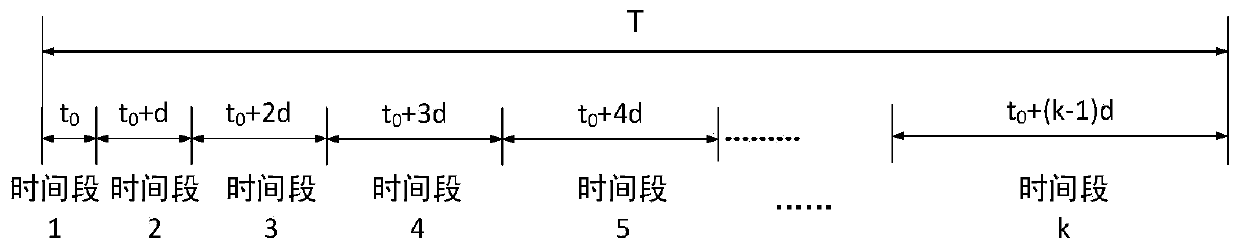
[0033] Step 2: Preprocess the network flow to form a flow representation based on time-segmented low-order statistical features;
[0034] Step 3: Build a convolutional neural network-based classification model with two independent input channels;
[0035] Step 4: Take the sample data represented by the two flows of step 1 and step 2 as input at the same time, and verify the classification effect of the model through the model training and testing process.
[0036] The network flows in step 1 and step 2 are all bidirectional flows (bidirectional fl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com