Method and device for testing service process of security chip
A security chip and business process technology, applied in software testing/debugging, error detection/correction, instruments, etc., can solve the problem of inability to conduct remote and local business interaction process testing, project and project codes cannot be shared, and business process testing cannot be effective Inheritance and other issues to achieve the effect of facilitating the development of automated test scripts, comprehensive test coverage, and convenient design
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
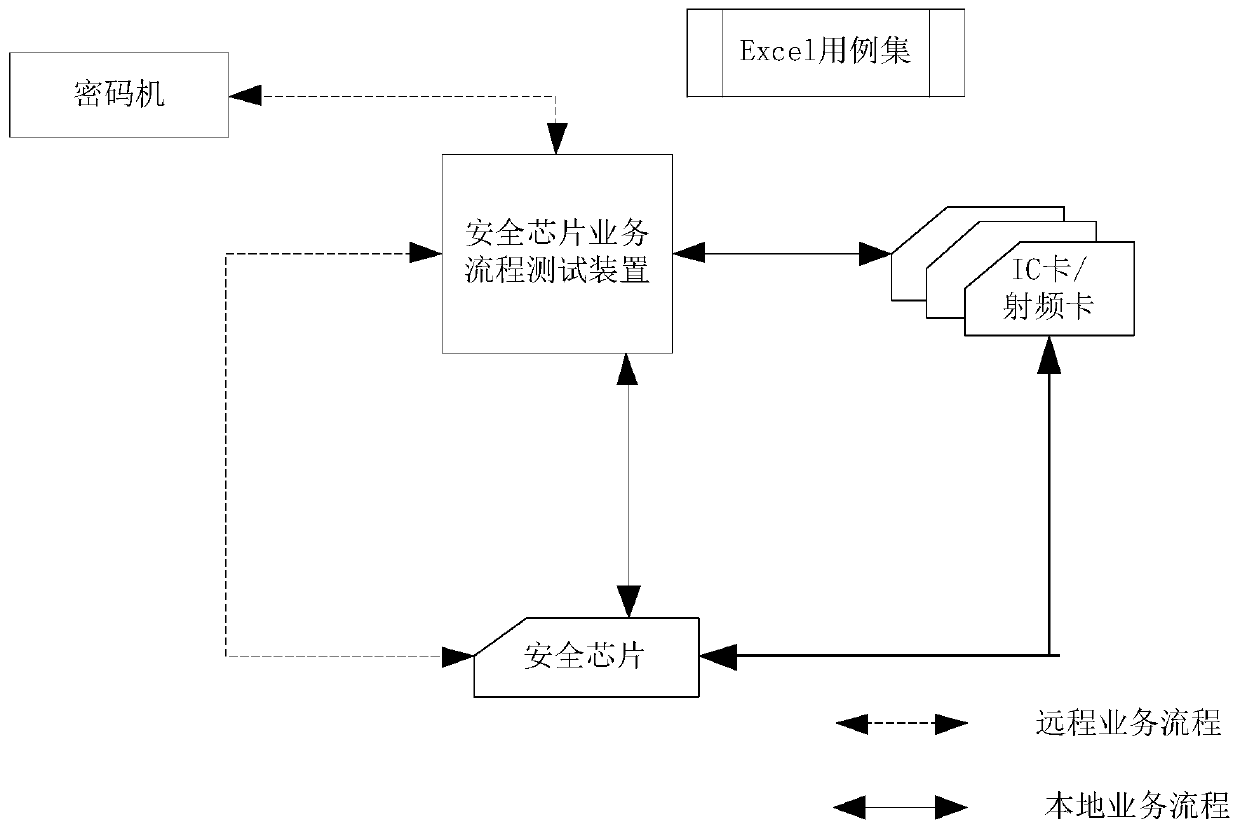
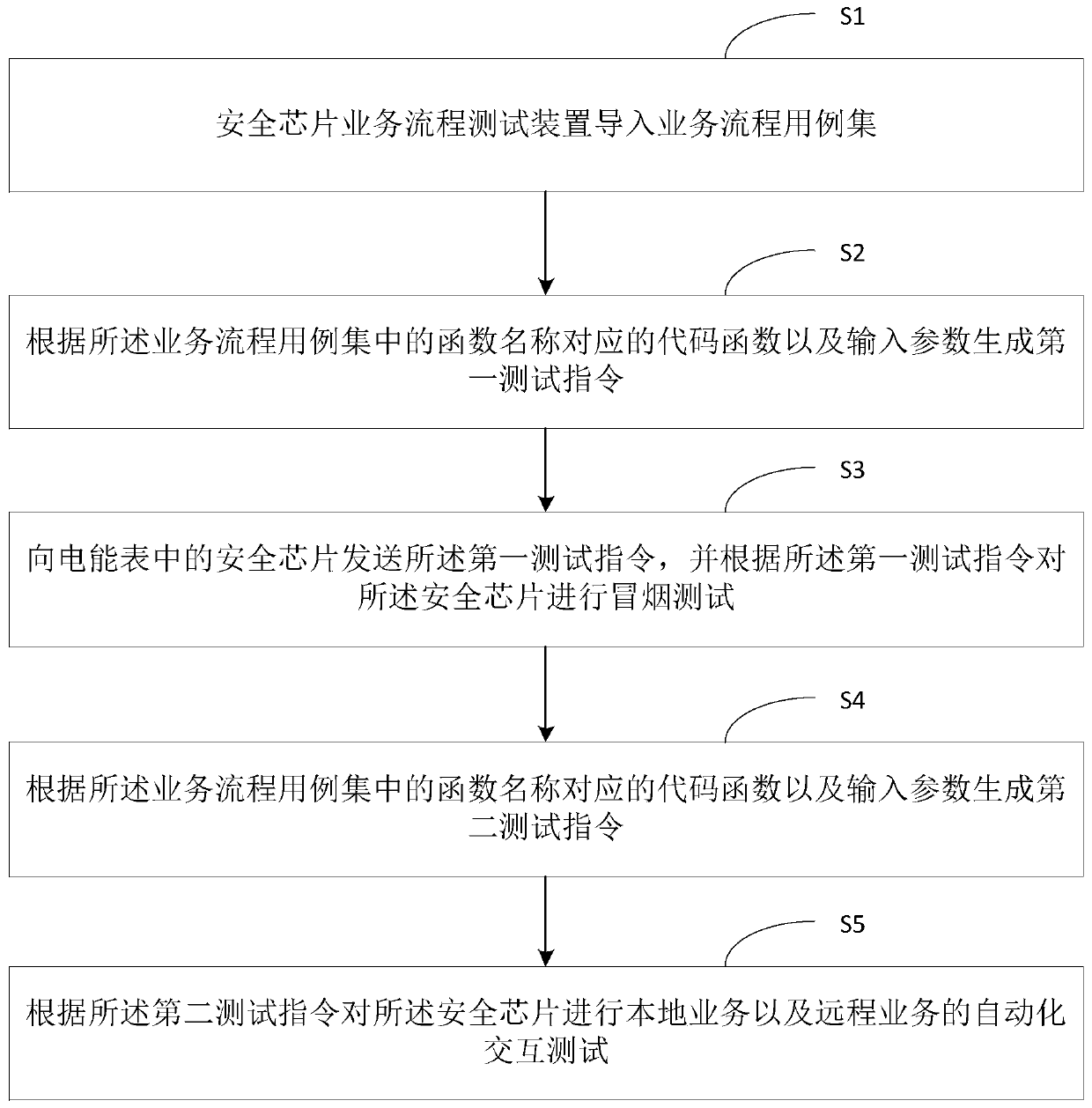
[0022] Such as Figure 1-2 as shown, figure 1 It is a schematic diagram of the testing structure of the security chip business process testing device according to the preferred embodiment of the present invention, figure 2 It is a flowchart of a security chip business process testing method according to a preferred embodiment of the present invention, and the testing method includes: steps S1-S5.
[0023] Step S1, the security chip business process testing device imports a business process use case set, wherein the business process use case set stores a plurality of function names and input parameters corresponding to the function names, and the business process use case set includes remote business use cases set and the set of local business use cases.
[0024] Specifically, the business process use case set may be an Excel table. By writing the instructions of the business process into Excel, using the cell content of Excel to specify the calling code function, that is, ...
Embodiment 2
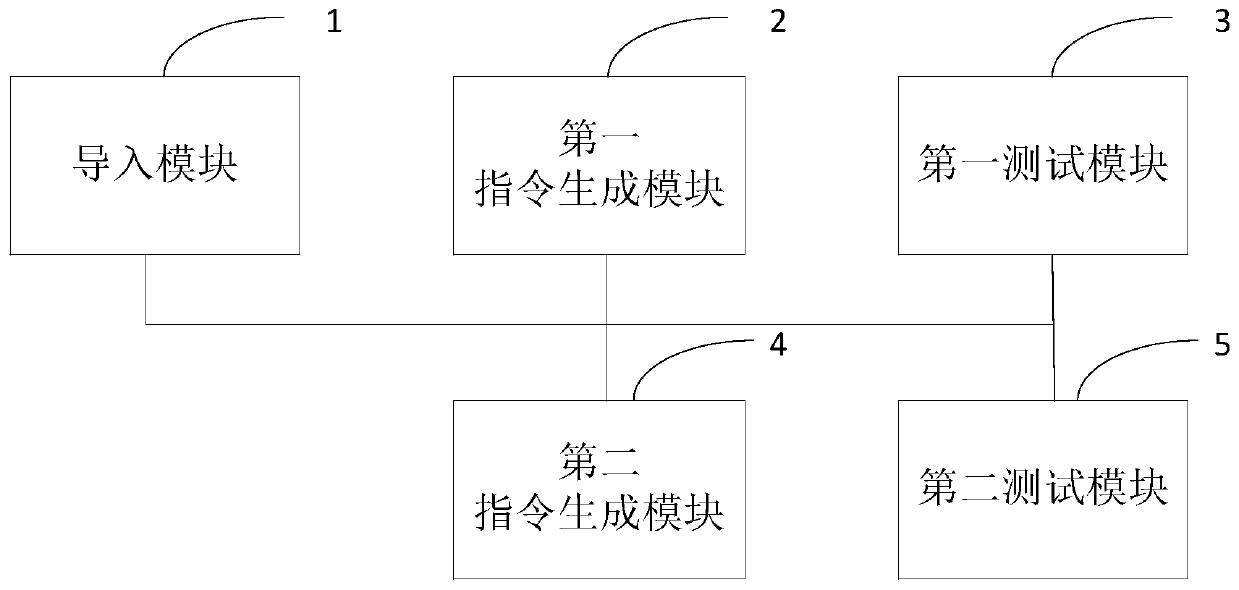
[0050] Such as figure 2 As shown in , it is a schematic structural diagram of a security chip business process testing device according to a preferred embodiment of the present invention.
[0051] The test device includes: an import module 1 , a first instruction generation module 2 , a first test module 3 , a second instruction generation module 4 , and a second test module 5 .
[0052] The import module 1 is used to import a business process use case set, wherein the business process use case set stores a plurality of function names and input parameters corresponding to the function names, and the business process use case set includes a remote business use case set and a local business Set of use cases.
[0053] The first instruction generation module 2 is connected with the import module 1, and is used to generate the first test instruction according to the code function corresponding to the function name in the business process use case set and the input parameters.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com