Security upgrading method and system, server and vehicle-mounted terminal
A technology for security upgrades and in-vehicle terminals, which is applied in the field of Internet of Vehicles and can solve the problem of vehicles exposed to security risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
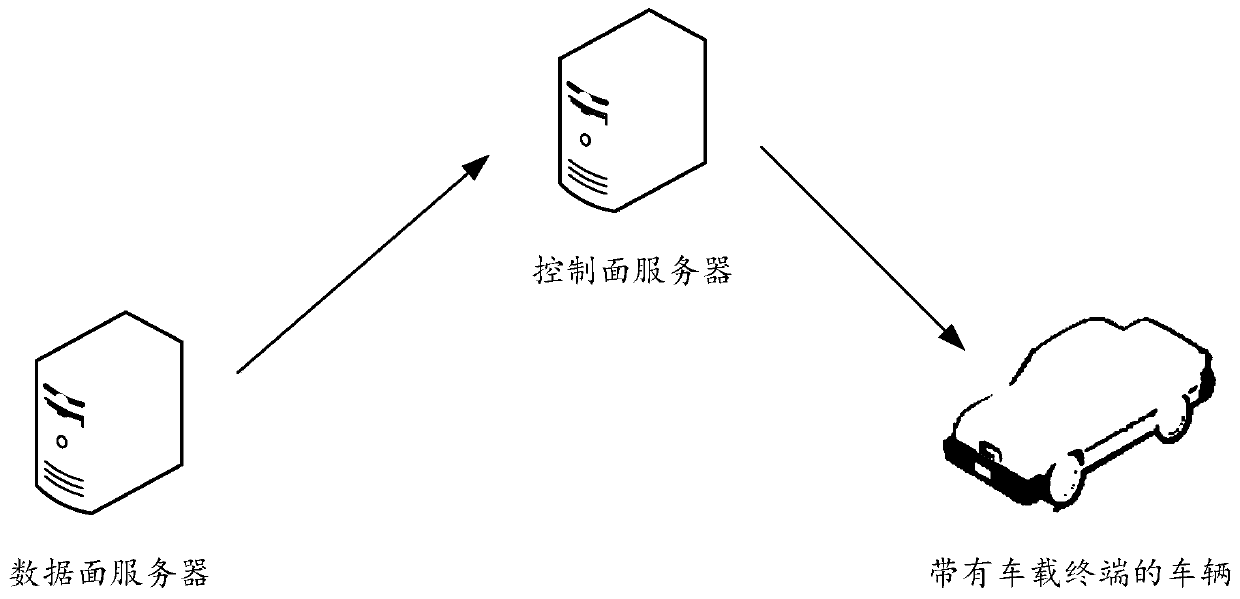
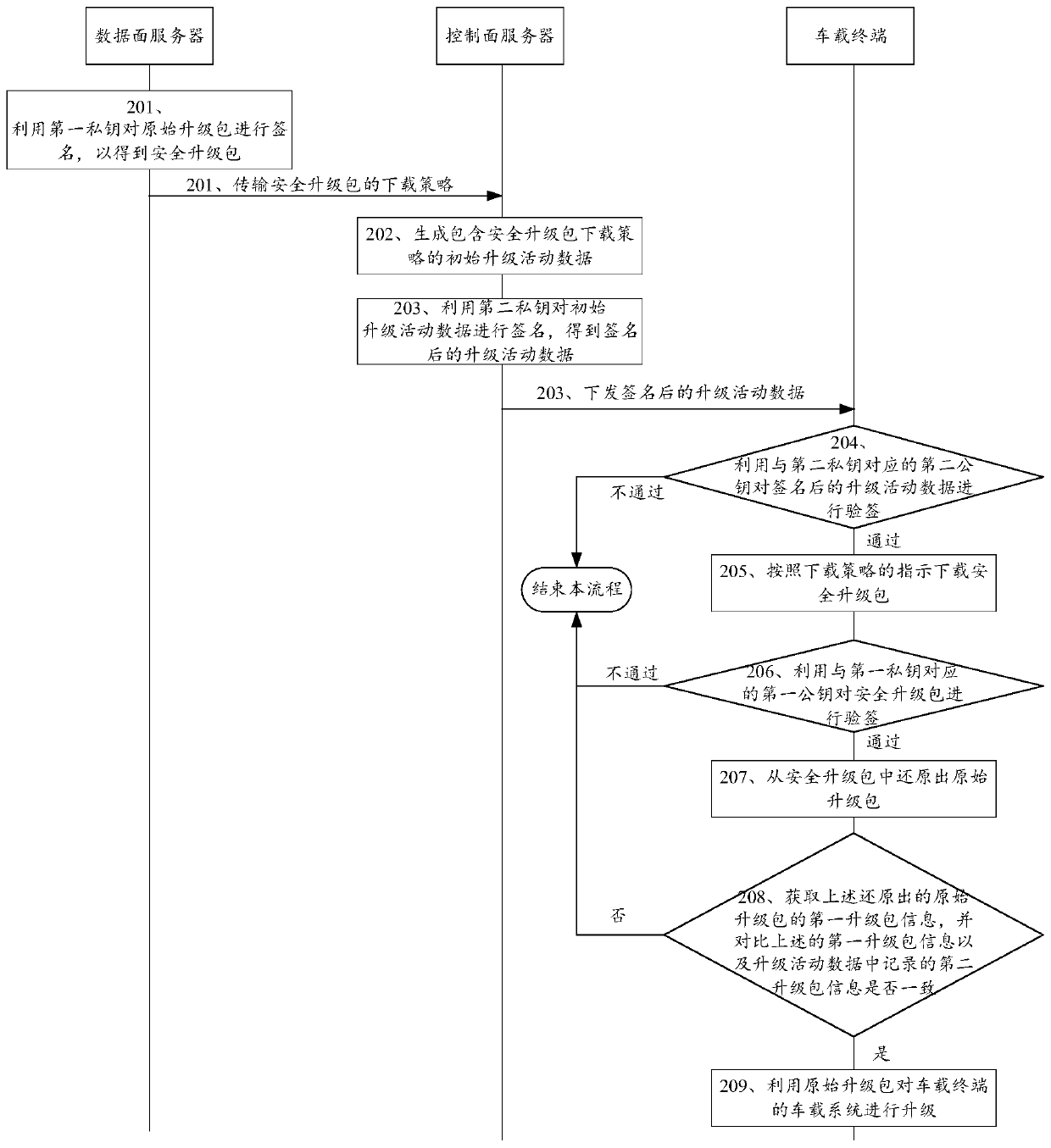
[0091] see figure 2 , figure 2 It is a schematic flowchart of a security upgrade method disclosed in an embodiment of the present invention. figure 2 The security upgrade method shown can be applied as figure 1 Upgrade system shown. Such as figure 2 As shown, the security upgrade method may include the following steps:
[0092] 201. The data plane server uses the first private key to sign the original upgrade package to obtain the security upgrade package, and transmits the download policy of the security upgrade package to the control plane server.
[0093] First, the configuration of the key pair in the embodiment of the present invention is introduced. Among them, the first private key and the first public key are a set of corresponding key pairs, the following second private key and the second public key are another set of corresponding key pairs, and each set of key pairs has a unique ID number as identification. Specifically, the private key in the key pair an...
Embodiment 2
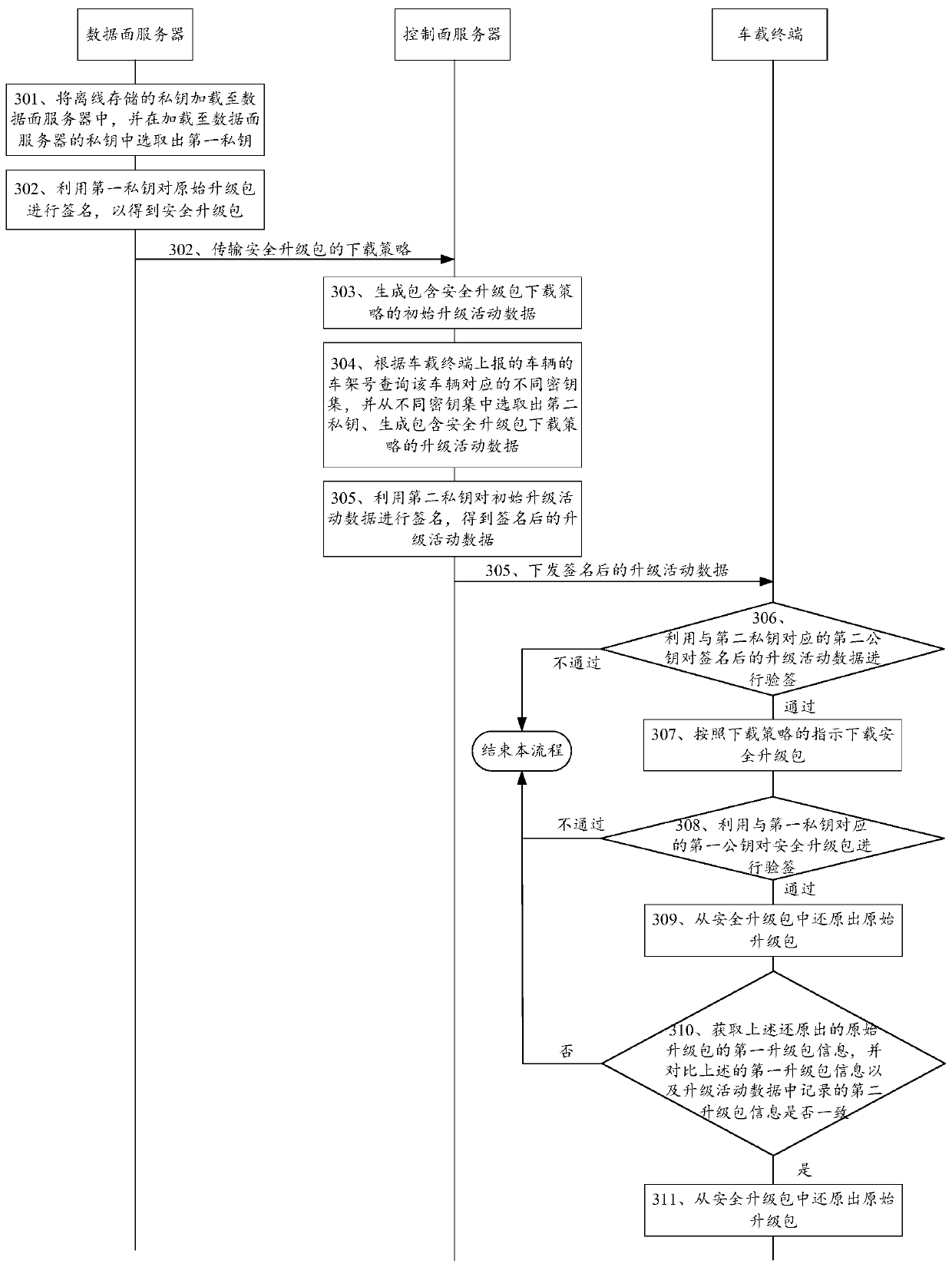
[0117] see image 3 , image 3 It is a schematic flowchart of another security upgrade method disclosed in the embodiment of the present invention. like image 3 As shown, the security upgrade method may include:
[0118] 301. The data plane server loads private keys stored offline to the data plane server, and selects a first private key from the private keys loaded to the data plane server.
[0119] In this embodiment of the present invention, the data plane server may be a server located in an internal local area network. The closedness of the internal LAN is relatively high, and it is relatively difficult for external attackers to attack the servers in the internal LAN. Moreover, the private key used by the data plane server is stored offline, and then loaded into the data plane server when used. In this way, even if the data plane server is compromised, it is difficult for the attacker to obtain the private key used by the data plane server when signing.
[0120] In...
Embodiment 3
[0143] see Figure 4 , Figure 4 It is a schematic structural diagram of a server disclosed in an embodiment of the present invention. Figure 4 The server shown may be a control plane server. Optionally, the control plane server may be located in a public network. like Figure 4 As shown, the server can include:
[0144] The generating unit 401 is configured to generate initial upgrade activity data including a security upgrade package download policy; wherein, the security upgrade package is obtained after the data plane server signs the original upgrade package with a first private key; the data plane server and the control plane Servers are separate and distinct servers.
[0145] The first signing unit 402 is configured to use the second private key to sign the above-mentioned initial upgrade activity data to obtain signed upgrade activity data;
[0146] In the embodiment of the present invention, as an optional implementation, the first signing unit 402 may also be ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com