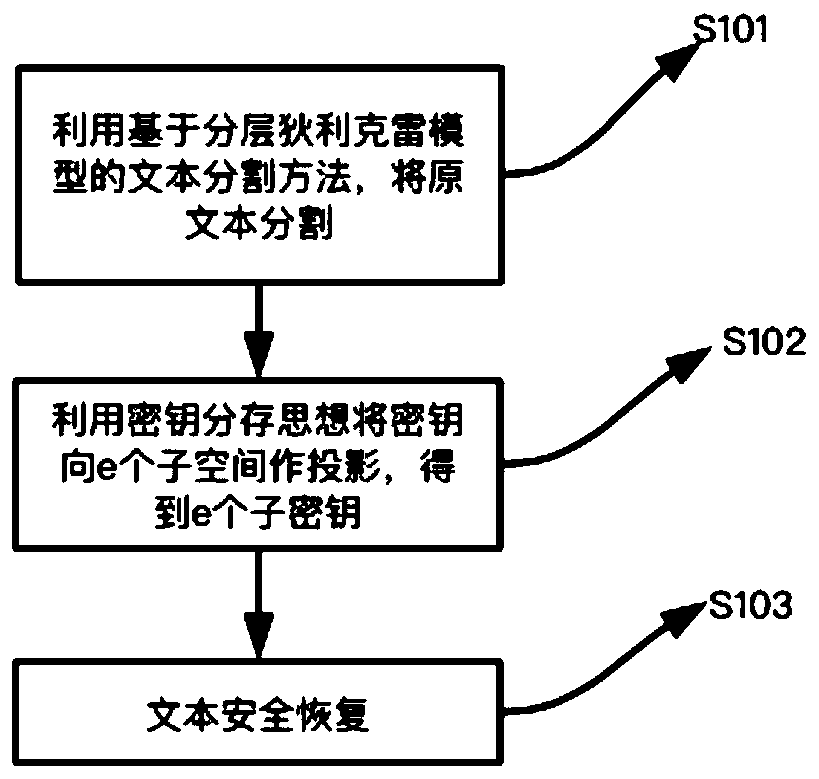
Text security segmentation method
A text segmentation, text technology, used in secure communication devices, computer security devices, key distribution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0086] In order to verify the method of the present invention, Sogou classified news is analyzed, and it is used as the experimental test corpus. Randomly select 10 different texts from 4000 corpus each time, extract 3-11 sentences highlighting themes from each text to form a paragraph, combine these 10 paragraphs to form a new text, and use this new text as the text to be segmented.
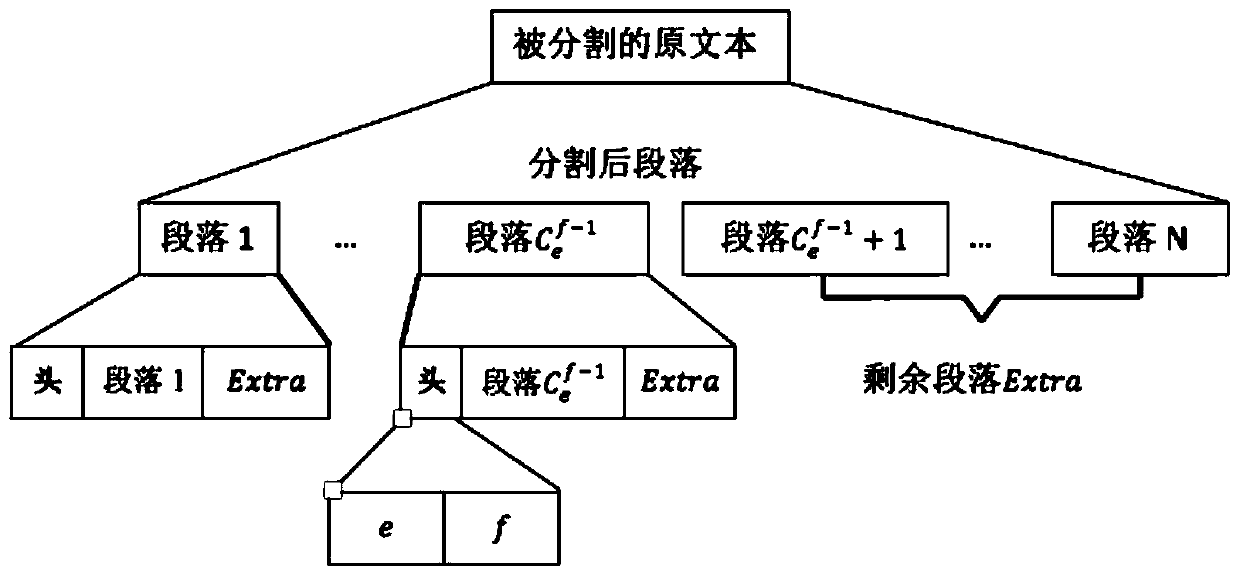
[0087] Segment the new text into 10 paragraphs using a text segmentation method based on the hierarchical Dirichlet model. According to the formula:
[0088]
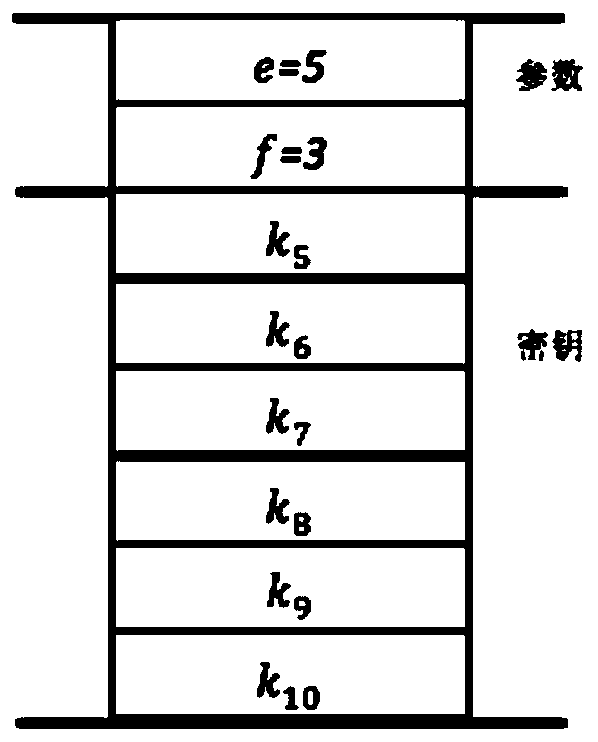
[0089]Obtain e=5, f=3, represent that 10 paragraphs are mapped to 5 subtexts (P 1 , P 2 , P 3 , P 4 , P 5 ), the text can be restored with 3 of the subtexts. key is k 1 , k 2 ,...,k 10 , corresponding to the divided 10 paragraphs. as P 1 The header of the file is attached image 3 , where parameters e=5, f=3 constitute the segmentation parameter area, P 1 has key k 5 , k 6 , k 7 , k 8 , k 9 , k 10 .
[0090] The di...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com