Method and system for detecting source network load system interaction message abnormity
A detection method and technology for exchanging messages, applied in the field of information security, can solve the problems of lack of parsing and detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
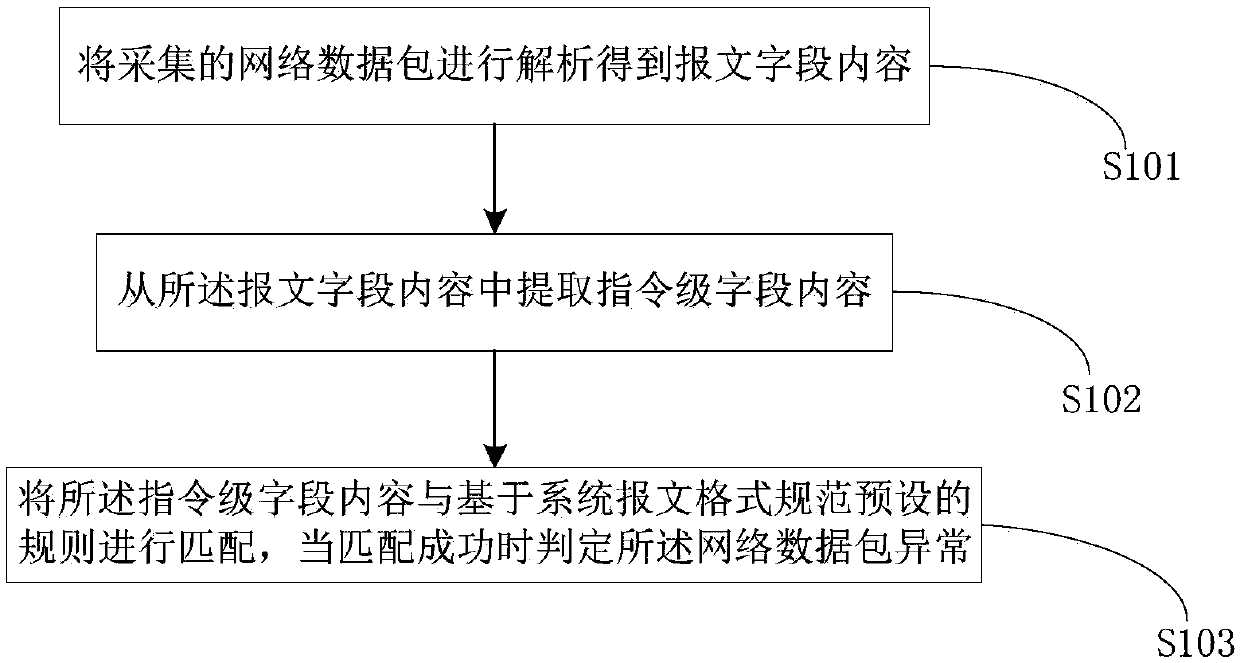
[0050] figure 1 It is a flow chart of the detection method for the abnormality of the interactive message of the source network load system of the present invention, such as figure 1 shown, including:
[0051] Step S101, analyzing the collected network data packet to obtain the content of the message field;
[0052] Step S102, extracting the command-level field content from the message field content;
[0053] Step S103 , matching the content of the command-level field with a preset rule based on the system packet format specification, and determining that the network data packet is abnormal when the matching is successful.
[0054] Step S101, analyzing the collected network data packet to obtain the content of the message field, including:
[0055] The network data packets include: data packets in a shared Ethernet environment or data packets in a switched Ethernet environment.
[0056] Analyze the collected network data;
[0057] Filter the parsed packets;
[0058] In t...
Embodiment 2
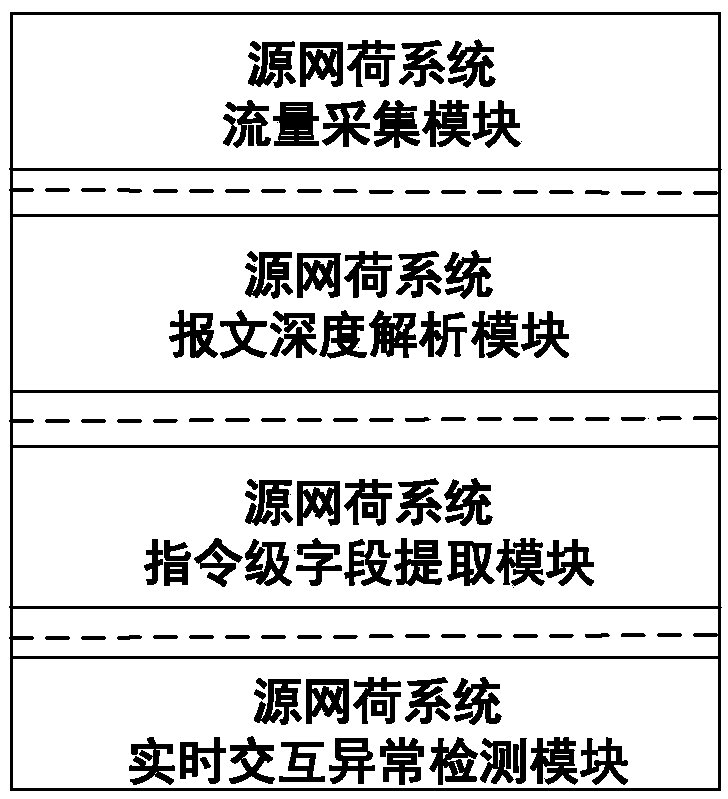
[0079] figure 2 It is a structural diagram of the interactive anomaly detection system of the source-network-load system, which mainly includes four parts: source-network-load system traffic collection module, source-network-load system message depth analysis module, source-network-load system command-level field extraction module and source Network load system real-time interaction detection module.
[0080] Among them, the traffic collection module of the source-network-load system, the packet depth analysis module, and the command-level field extraction module are responsible for the collection, analysis, and command-level field extraction of the real-time interactive traffic of the source-network-load system. The real-time interaction detection module of the source-network-load system completes the source network The identification of malformed packets, violations and attack behaviors in the business flow of the load system.
[0081] The 104 protocol is used in the sourc...
Embodiment 3
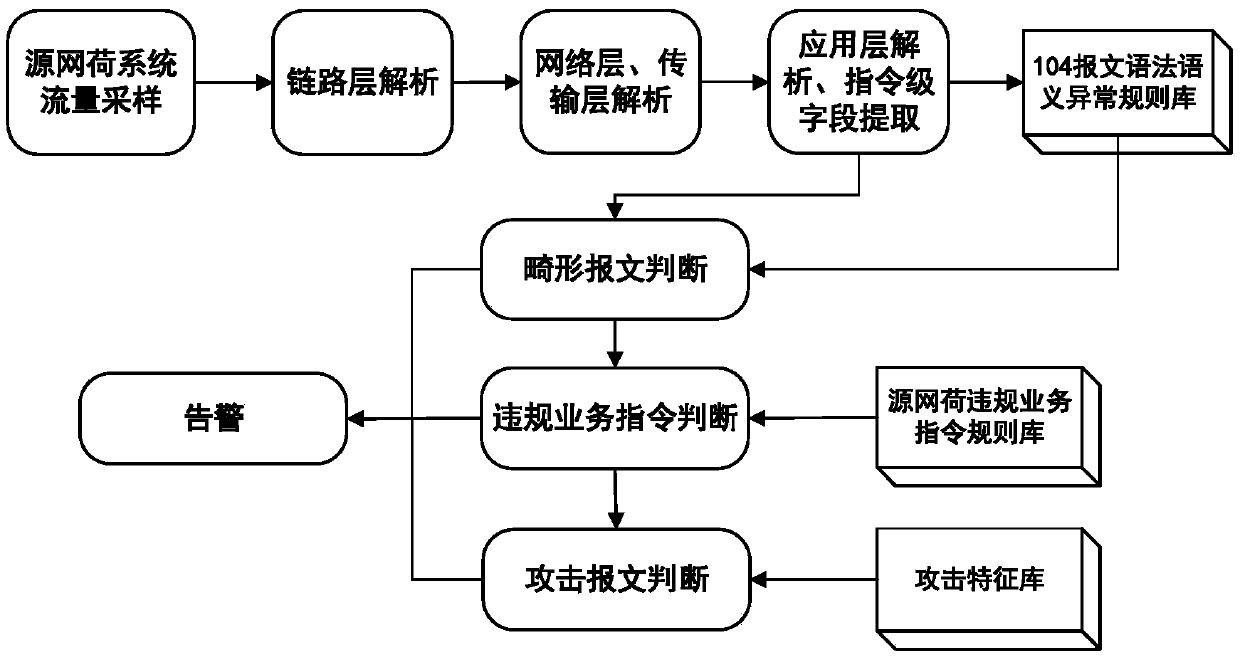
[0141] like Figure 4 As shown, the specific implementation flow chart of the detection method is implemented, and the specific steps include:
[0142] Step 1: The traffic collection module collects data packets in the network, and sends the captured data packets to the packet depth analysis module for analysis.
[0143] Step 2: The packet depth analysis module of the source network load system performs TCP / IP layer analysis, extracts information such as source mac address, destination mac address, source ip address, destination ip address, source port number, destination port number, etc., and analyzes the packet Perform application layer analysis.
[0144] Step 3: The command-level field extraction module of the source network load system extracts the initial character of the message header of 1 byte, the field value of the message control field of 4 bytes, and the length character of the application service data unit of 1 byte , the 7th byte type identification of the app...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com