Safe unlocking method
A security and lock technology, applied in instruments, time registers, individual input/output registers, etc., can solve problems such as insecurity, and achieve the effect of reducing financial investment, improving security, and reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
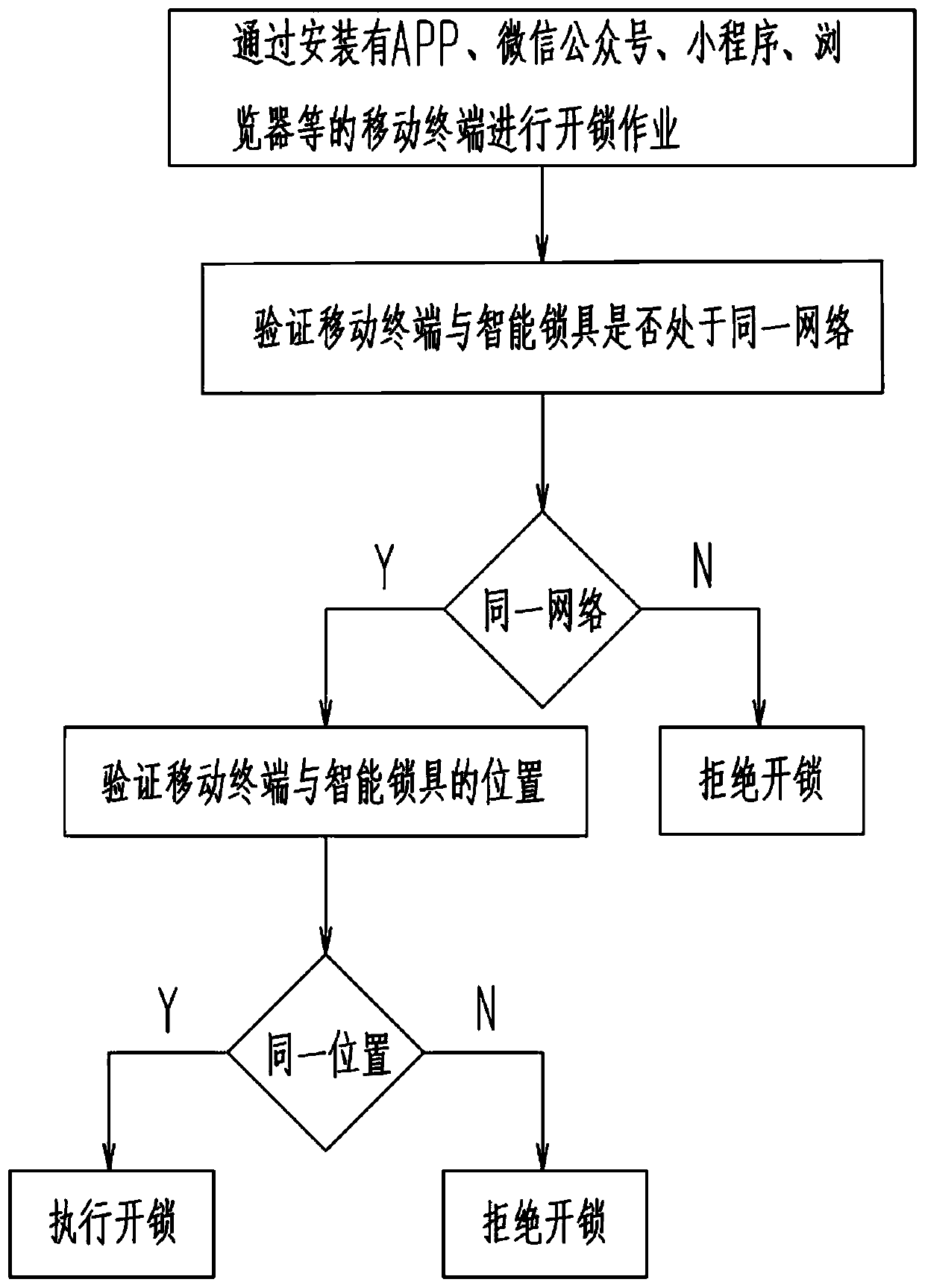
[0033] A method for safely unlocking, the unlocking method comprising the steps of:
[0034] S1. Set the smart lock to be connected to the site wireless network;
[0035] S2. Read the wireless network information on the mobile terminal through the APP, WeChat official account, applet, and mobile website supporting the smart lock, and compare it with the stored networking information of the smart lock;
[0036] S3, APP, WeChat official account, applet, mobile website After the wireless network information connected to the mobile terminal is successfully compared with the stored networking information of the smart lock, the smart lock is opened and personnel are allowed to open the door.
Embodiment 2
[0038] A method for safely unlocking, the unlocking method also includes the following steps:
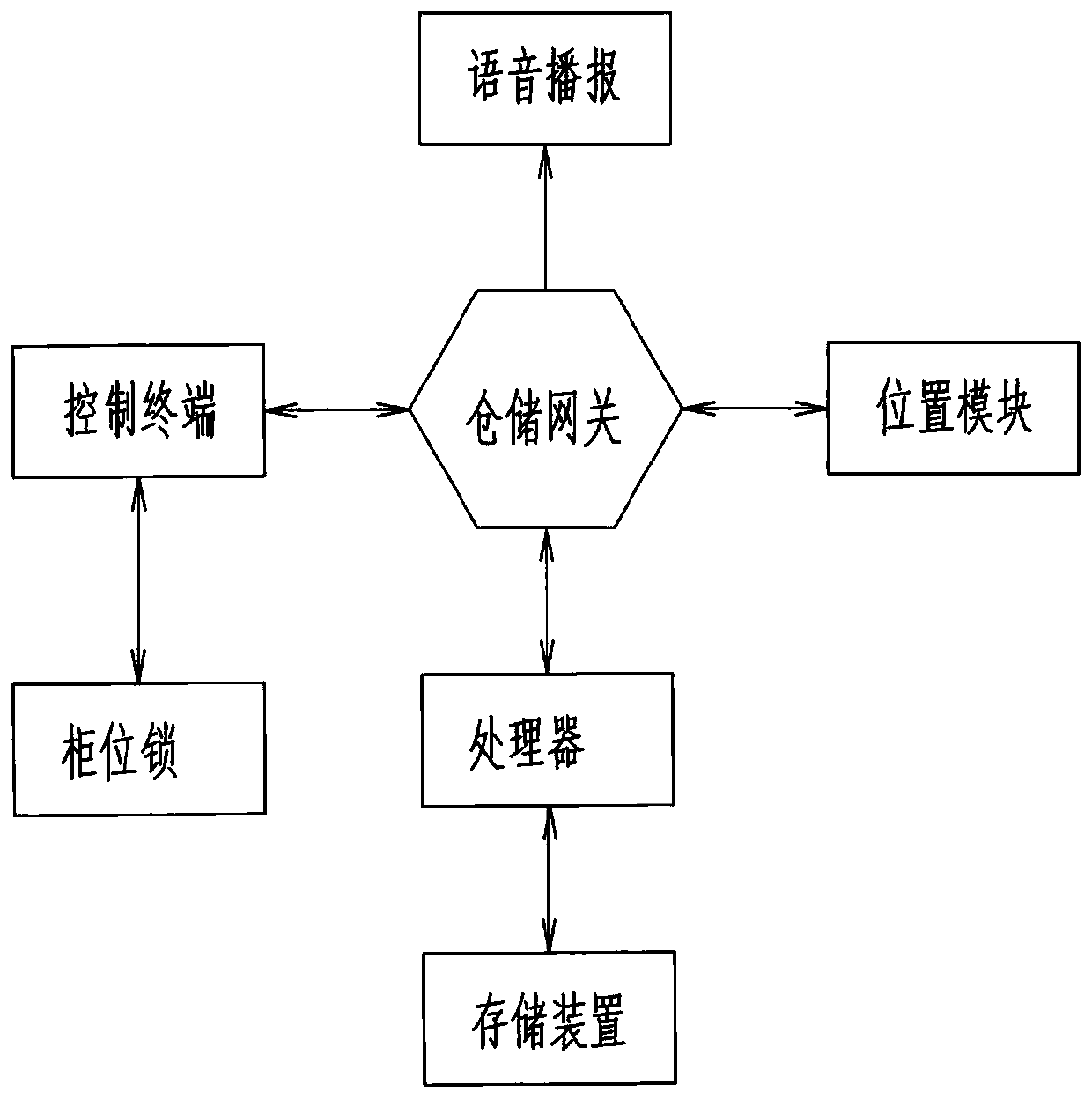
[0039]The smart lock includes a positioning module, which can obtain positioning information and transmit the positioning information through the connected wireless network to the supporting APP, WeChat official account, and mobile phone website through the background server; Official accounts, applets, and mobile websites can read the location information of the location module on the mobile terminal and compare it with the location information of the smart lock. If the comparison is successful, the unlocking operation will be executed. The positioning module includes one of a GPS chip and its associated circuits, a Beidou chip and its associated circuits. After the location information collected on the smart lock is compared with the location information collected by the APP, WeChat official account, applet, and mobile website on the mobile terminal, the distance between the two s...
Embodiment 3
[0041] A method for unlocking safely, wherein the method for unlocking also includes the following steps:
[0042] The mobile terminal includes one of a smart phone, a tablet computer, a PDA, and a notebook computer. The smart lock is connected to the wireless network of the site, and the wireless network of the site includes one of WIFI and WLAN. The WIFI and WLAN use 2.4GHz or 5GHz, and the smart lock and APP should be connected to the WIFI or WLAN network at the same frequency. The data exchange between the APP, WeChat official account, mobile website and the smart lock is carried out through the carrier network and the background server, and the carrier network includes optical fiber and WLAN network. The mobile terminal APP, WeChat official account, applet, mobile website communicate with the background server of the outlet, and the background server verifies whether the request has normal unlocking authority. The smart lock sends an unlocking request, and the smart loc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com