Current limiting method and device
A current limiting method and current limiting technology, applied in the network field, can solve problems affecting client access, high labor cost of the current limiting threshold, and inability to allocate server access, so as to improve accuracy and reduce labor costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
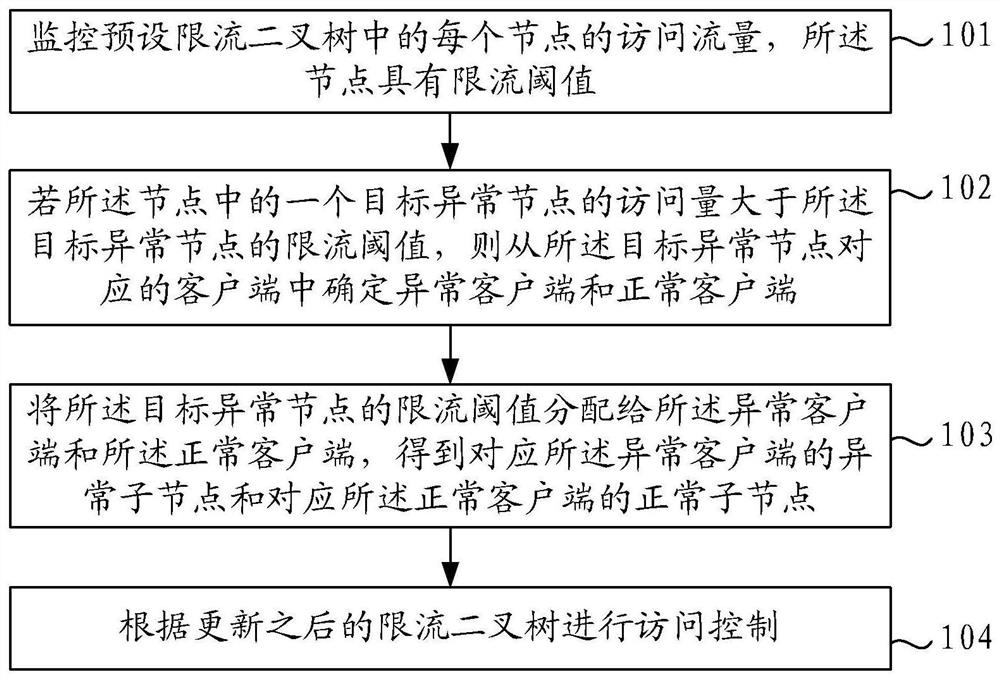
[0033] refer to figure 1 , which shows a flow chart of the steps of the current limiting method in an embodiment of the present disclosure, specifically as follows.
[0034] Step 101 , monitor the access volume of each node in the preset current-limited binary tree, and the node has a current-limited threshold.
[0035] The embodiments of the present disclosure are used to perform access control on the server to ensure that the server can run normally without causing the server to crash due to excessive access.
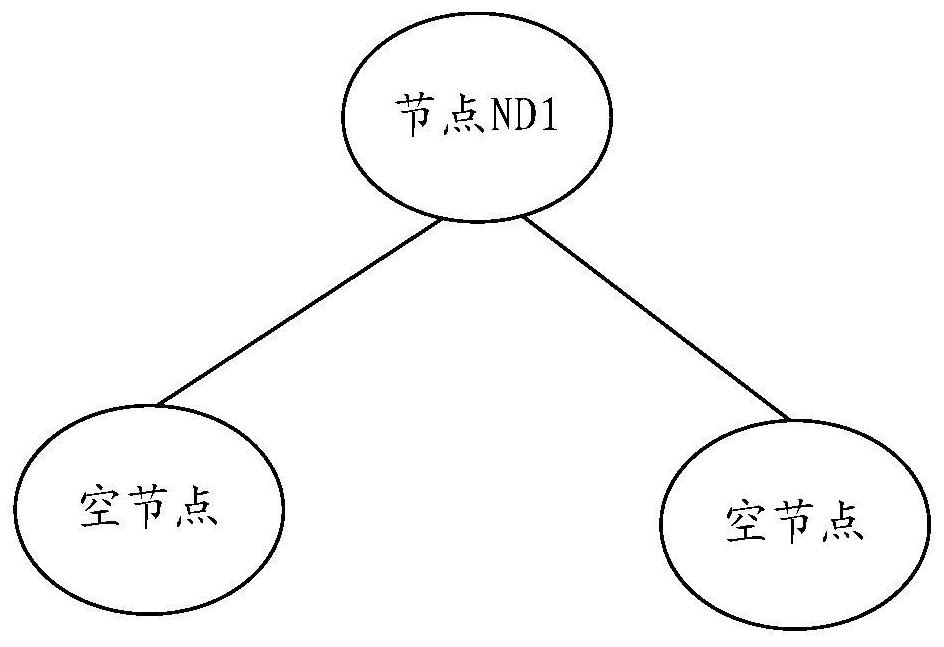
[0036] Among them, the current-limited binary tree is constructed based on the full binary tree. In the initial state, the current-limited binary tree only includes one root node, such as image 3 As shown, the child node can be set as an empty node to process the access requests of all clients; when the access to the root node is greater than the current limiting threshold corresponding to the root node, the root node is split into a normal child node and an abnorma...
Embodiment 2
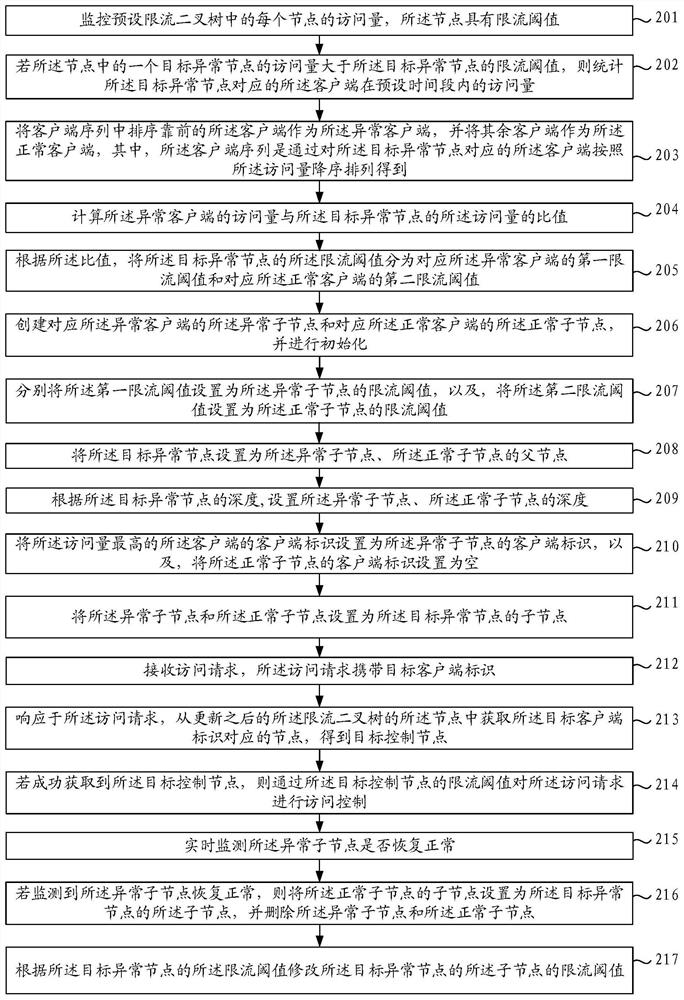
[0052] refer to figure 2 , which shows a flow chart of specific steps of the current limiting method in another embodiment of the present disclosure, specifically as follows.
[0053] Step 201, monitor the access volume of each node in the preset current-limited binary tree, and the node has a current-limited threshold.
[0054] For this step, reference may be made to the detailed description of step 101, which will not be repeated here.
[0055] Step 202, if the visit volume of a target abnormal node among the nodes is greater than the traffic limiting threshold of the target abnormal node, count the visit volume of the client corresponding to the target abnormal node within a preset time period.
[0056] Wherein, the preset time period may be a period of time before the current moment. For example, if the unit time is minutes, the ratio of the total number of access requests in the past two hours to 120 minutes is counted as the access amount.
[0057] It can be understoo...
Embodiment 3
[0121] refer to Figure 8 , which shows a structural diagram of a current limiting device in another embodiment of the present disclosure, as follows.
[0122] The traffic monitoring module 301 is configured to monitor the traffic of each node in the preset current-limited binary tree, and the node has a current-limiting threshold.
[0123] The client division module 302 is used to determine the abnormal client and the normal client from the clients corresponding to the target abnormal node if the visit volume of one target abnormal node in the nodes is greater than the current limiting threshold of the target abnormal node. client;
[0124] A current limiting threshold allocation module 303, configured to allocate the current limiting threshold of the target abnormal node to the abnormal client and the normal client, and obtain the abnormal child node corresponding to the abnormal client and the Normal child nodes.
[0125] The access control module 304 is configured to pe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com