An anti-reconnaissance evasion attack method for deep person re-identification system
A pedestrian re-identification and evasion attack technology, applied in the field of artificial intelligence security design, can solve problems such as spy intrusion and security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
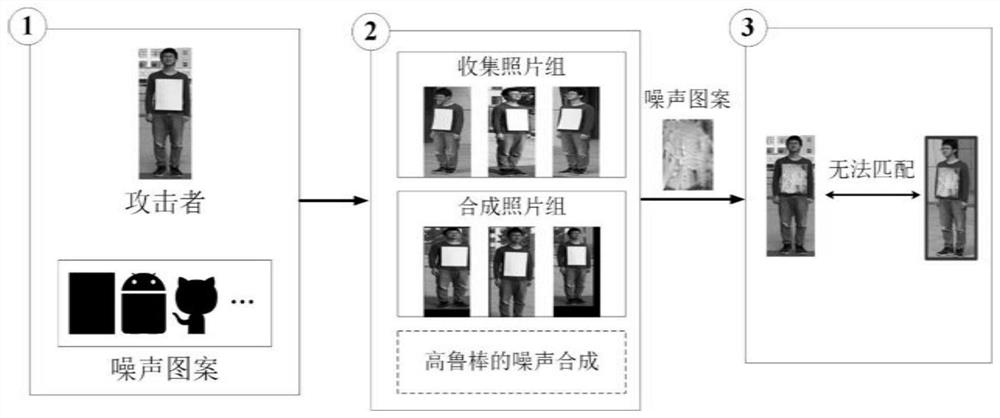
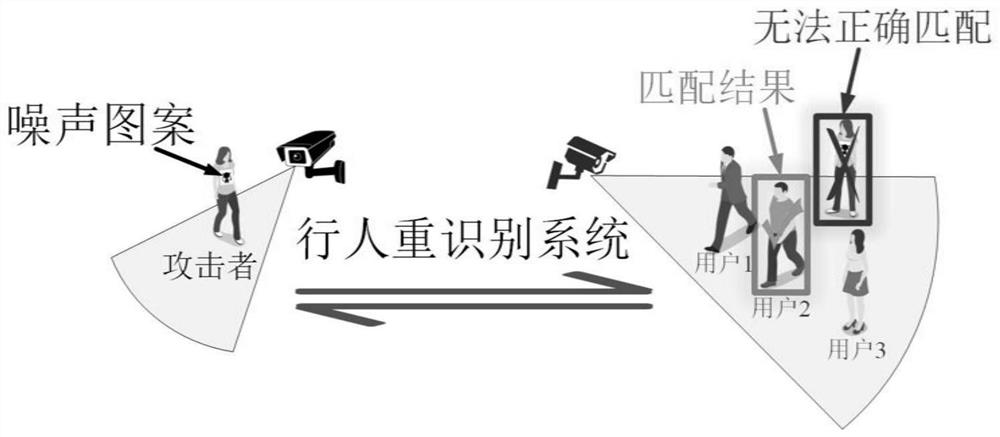
[0032] The present invention considers that the security issue of deep person re-identification has not been paid attention to, and it will bring potential security threats when it is widely used. Therefore, there is an urgent need for an anti-reconnaissance and evasion attack method for deep person re-identification systems.
[0033] The anti-reconnaissance escape attack method designed by the present invention for the deep pedestrian re-identification system includes the following steps:
[0034] 1) Given a pedestrian re-identification system, the query image is input, and the system outputs the similarity and similarity ranking between images captured by other cameras and the query image. The attacker can access the parameters and weights of the target model, and set the specific users that the attacker wants to match.
[0035] The target person re-identification system can be expressed as f θ (x,y)=sc, where x is the image that the system needs to query, y is the pedestri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com