Consortium Chain Construction Method Based on Discrete Logarithm
A discrete logarithm and construction method technology, applied in the field of network security, can solve problems such as difficult calculations, huge calculation overhead, and reduced system computing performance, and achieve the goals of improving security, efficient verification and confirmation, and efficient block recording and confirmation Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
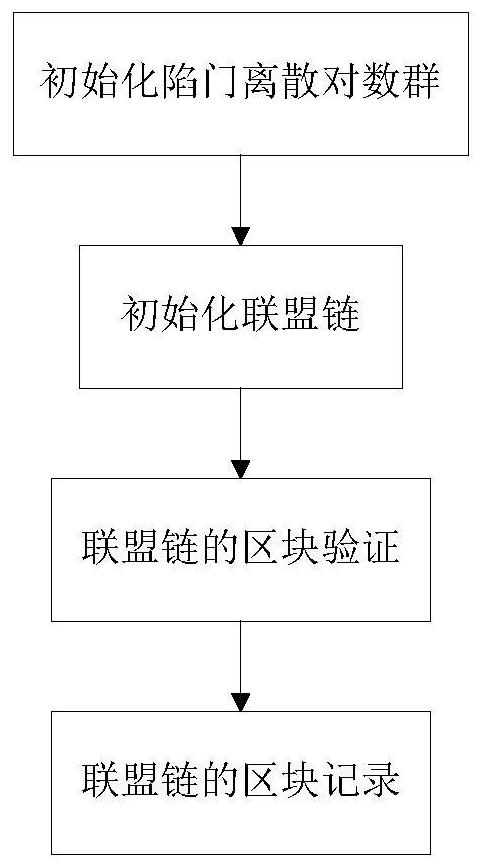
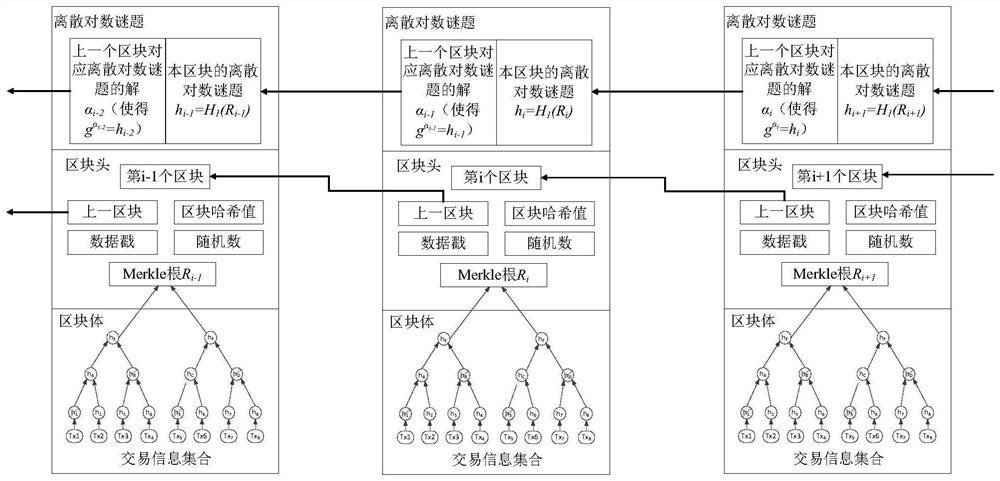
[0026] Such as figure 1 and figure 2 The method for constructing the consortium chain based on discrete logarithm in the present invention includes:
[0027] A. Initializing the trapdoor discrete logarithm group: According to the security parameter λ, a q-order multiplicative group G is generated, the generator of the multiplicative group G is g, and a trapdoor Td for calculating the discrete logarithm is generated to form a discrete The parameters corresponding to the logarithmic group (G, q, g, Td). by g α =h calculates the solution α of the discrete logarithm, where h∈G is an element on the multiplicative group G.
[0028] B. Initialize the consortium chain: generate the initial block (Genesis Block) of the consortium chain, and publicize the parameters P=(G, q, g, H 1 ) into the initial block, where the first hash function H 1 For: H 1 : {0, 1} * → G, then designate a batch of alliance nodes, and send the trapdoor Td to each alliance node.
[0029]C. Block verific...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com