Anti-peeping secret key input method for mobile phone
An input method and anti-peeping technology, applied in the direction of internal/peripheral computer component protection, digital data authentication, etc., can solve the problems of poor convenience and security, achieve high security, reduce the risk of key eavesdropping, and improve convenience sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] Below in conjunction with accompanying drawing and specific embodiment, the present invention is described in further detail:
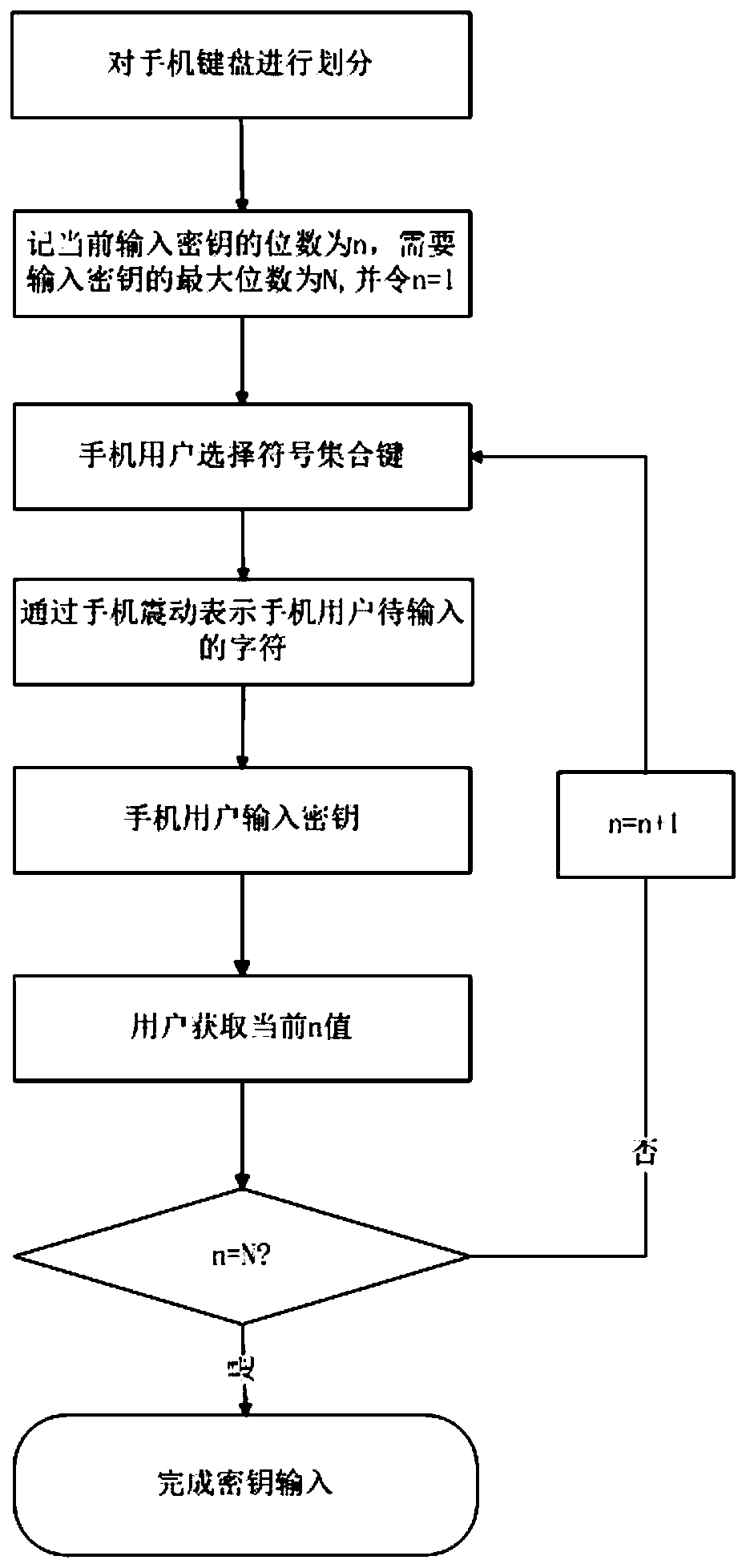
[0026] refer to figure 1 , the present invention comprises the following steps:
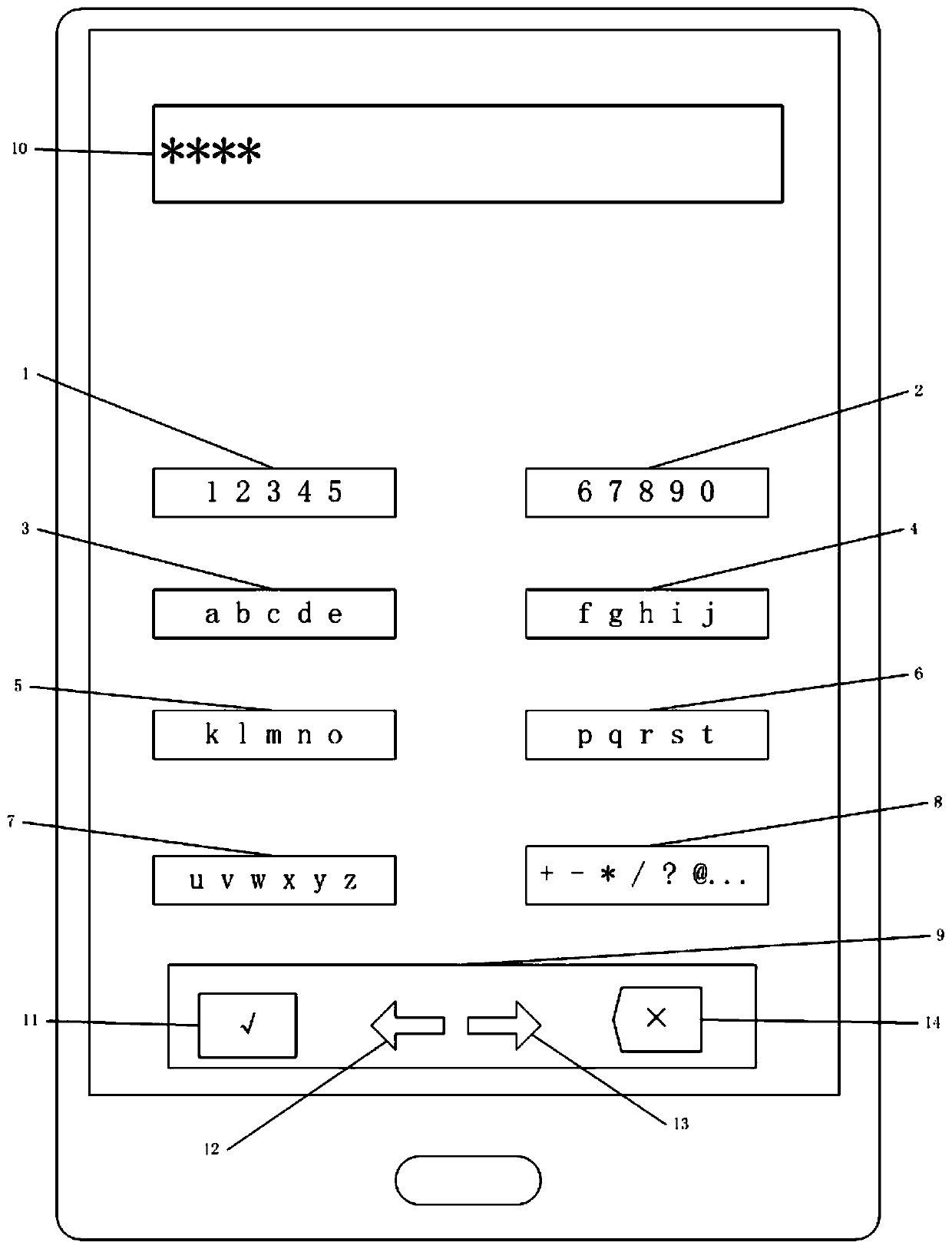
[0027] Step 1) divide the mobile phone keyboard, such as figure 2 Shown:
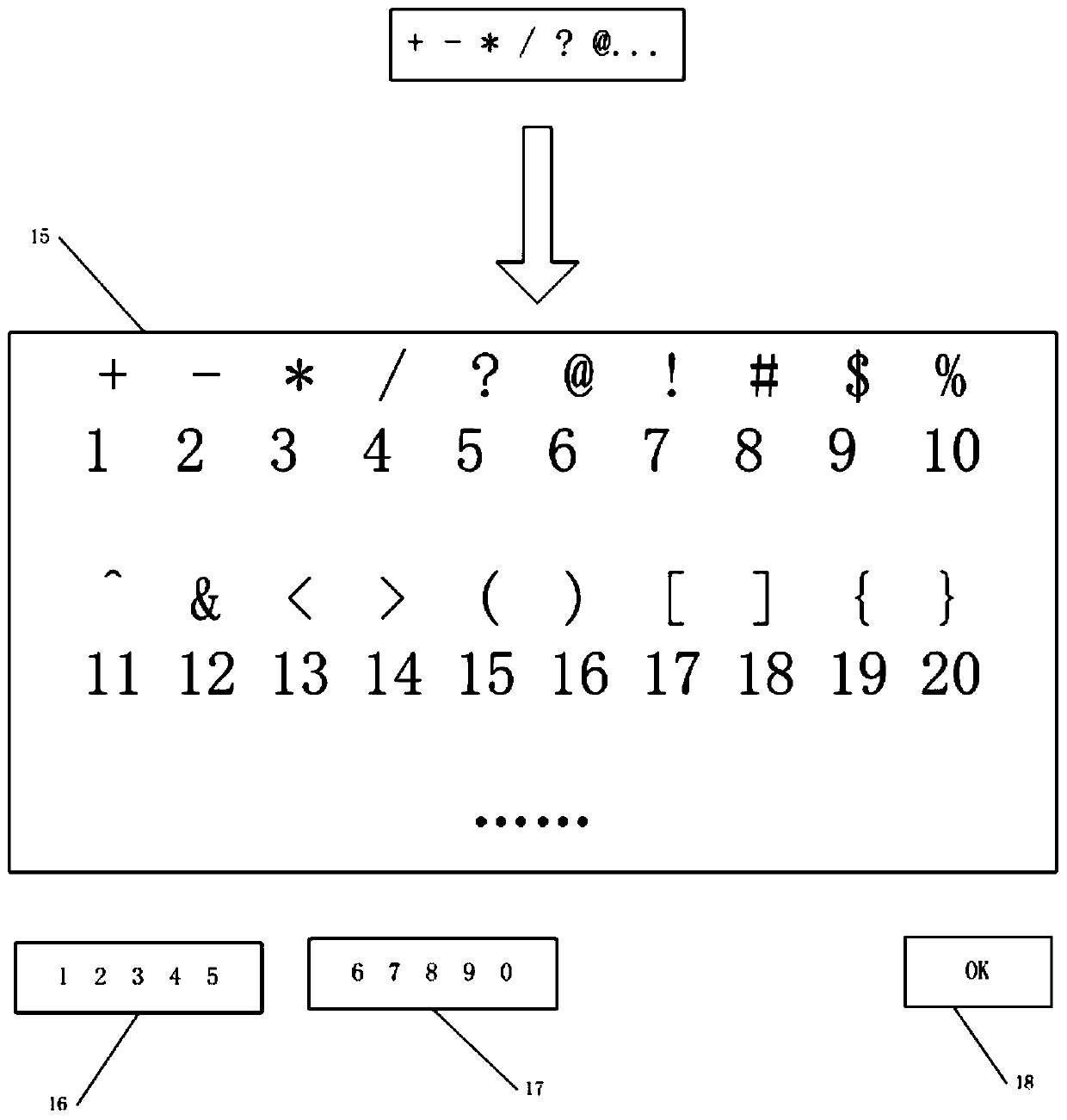
[0028] Divide the mobile phone keyboard into the first number set key (1) composed of number keys 1-5, the second number set key (2) composed of number keys 6-0, and the first letter set composed of letter keys a-e Set key (3), the second letter set key (4) made up of letter keys f~j, the third letter set key (5) made up of letter keys k~o, the fourth letter set key made up of letter keys p~t Letter set key (6) and the fifth letter set key (7) composed of letter keys u~z, special symbol set key (8) composed of all special symbol keys, confirmation key, forward key, backward key and delete key The modification set key (9) that key is formed, and the different characters on each key in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com