Code security scanning method and system
A security scanning and code technology, applied in the field of code security scanning methods and systems, can solve the problem of insufficient accuracy and reliability of code security scanning results, and achieve the effect of improving accuracy and reliability and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
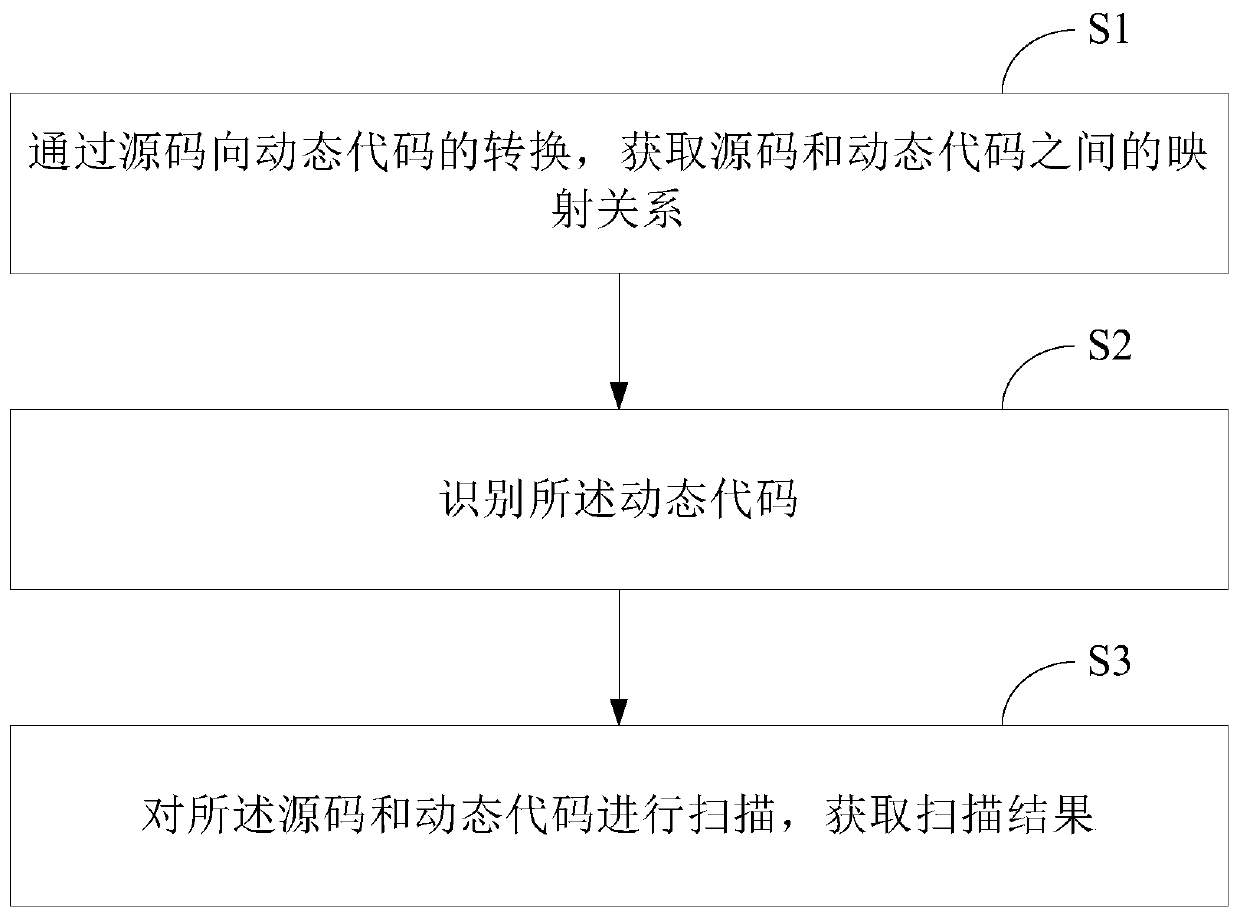
[0057] see figure 1 , figure 1 It is a schematic flowchart of a code security scanning method provided in the embodiment of the present application. Depend on figure 1 It can be seen that the code security scanning method in this embodiment mainly includes the following steps:
[0058] S1: Obtain the mapping relationship between source code and dynamic code through the conversion of source code to dynamic code.
[0059] Specifically, step S1 also includes the following process:
[0060] S11: Convert the source code to generate dynamic code.
[0061] In this embodiment, the conversion from source code to dynamic code includes the conversion between any two codes, and the source code is marked as source code A, and the dynamic code is marked as dynamic code B. In this embodiment, the conversion from source code A to dynamic code B uses the dynamic code conversion script of source code A. The dynamic code conversion script of the source code in this embodiment is a script f...
Embodiment 2
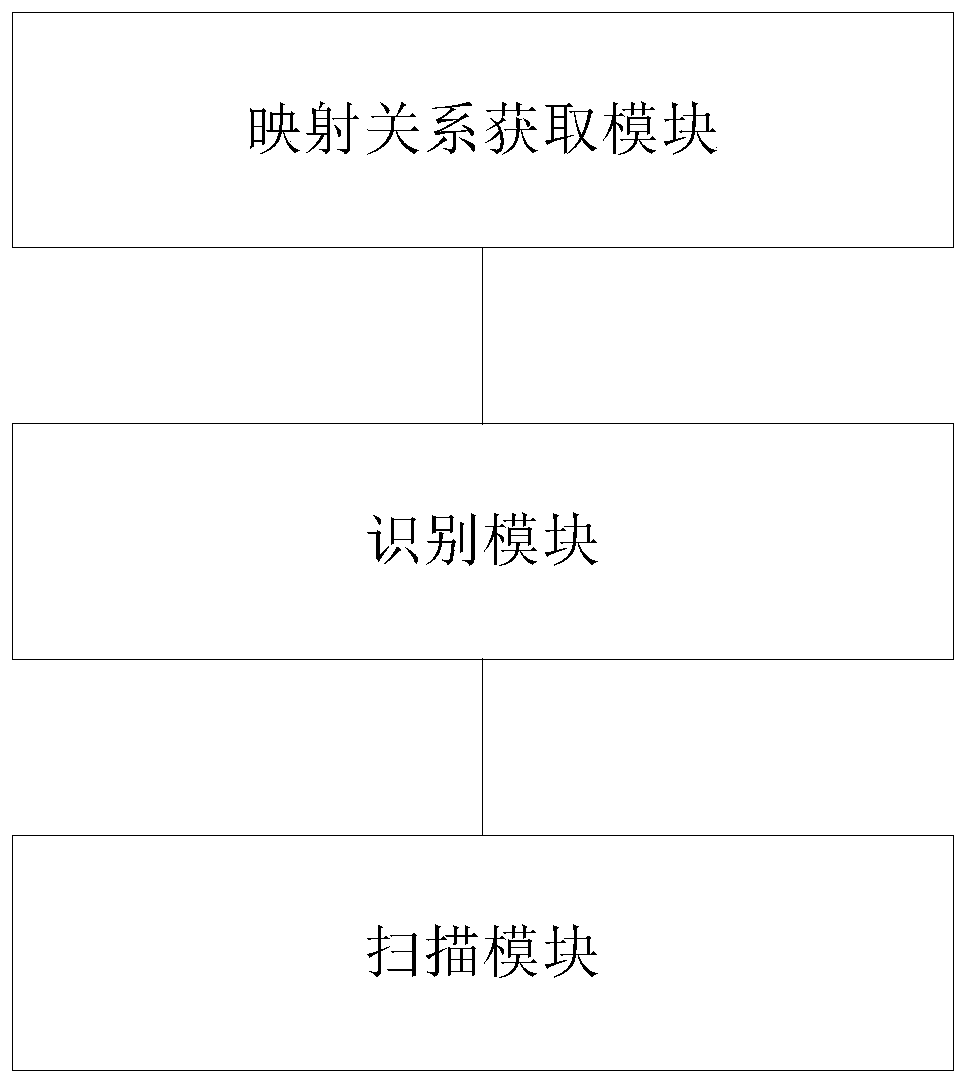
[0098] exist figure 1 On the basis of the illustrated embodiment see figure 2 , figure 2 It is a schematic structural diagram of a code security scanning system provided by the embodiment of the present application. Depend on figure 2 It can be seen that the code security scanning system in this embodiment mainly includes three parts: a mapping relationship acquisition module, an identification module and a scanning module. Among them, the mapping relationship acquisition module is used to obtain the mapping relationship between the source code and the dynamic code through the conversion of the source code to the dynamic code; the identification module is used to identify the dynamic code; the scanning module is used to scan the source code and the dynamic code to obtain the scanned result.
[0099] Wherein, the mapping relationship acquisition module further includes: a conversion unit, a first storage unit, a mapping relationship acquisition unit and a second storage ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com