Cache password-based network equipment security access system and working method thereof
A network device and password technology, applied in transmission systems, electrical components, etc., can solve the problems of asynchrony of passwords, large influence range, inability to log in account password control, etc., to ensure security and consistency, and enhance security and consistency. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
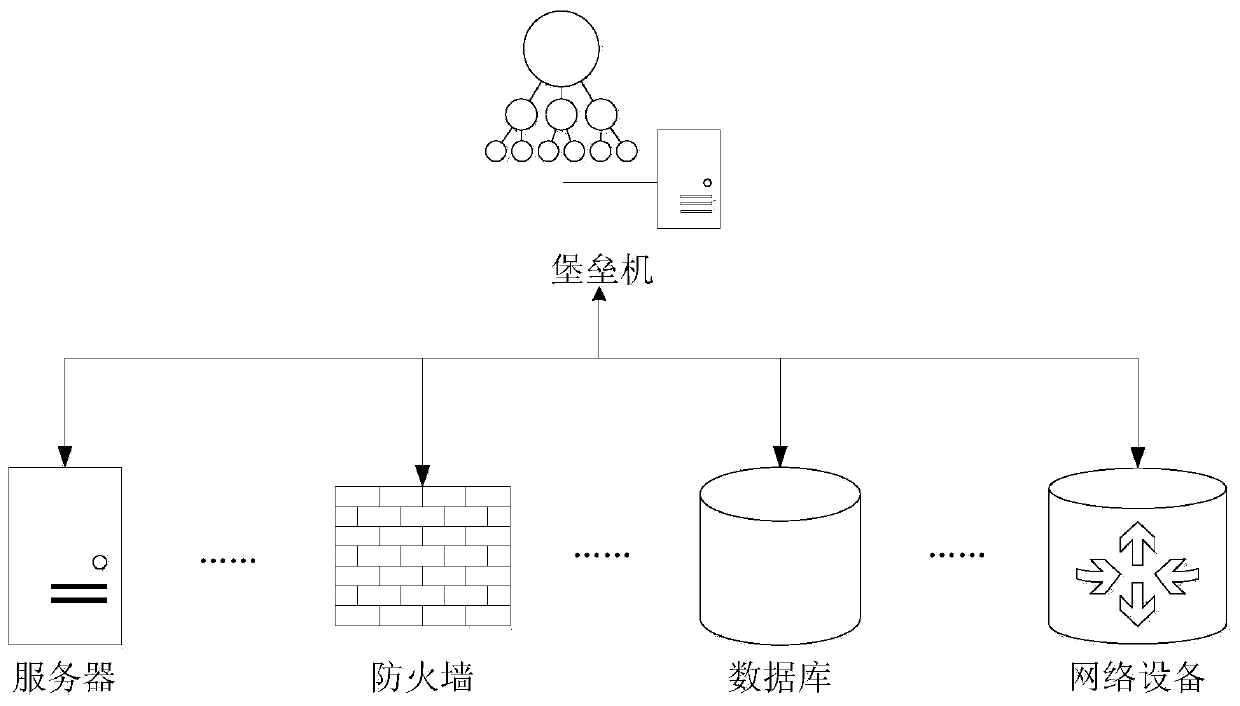
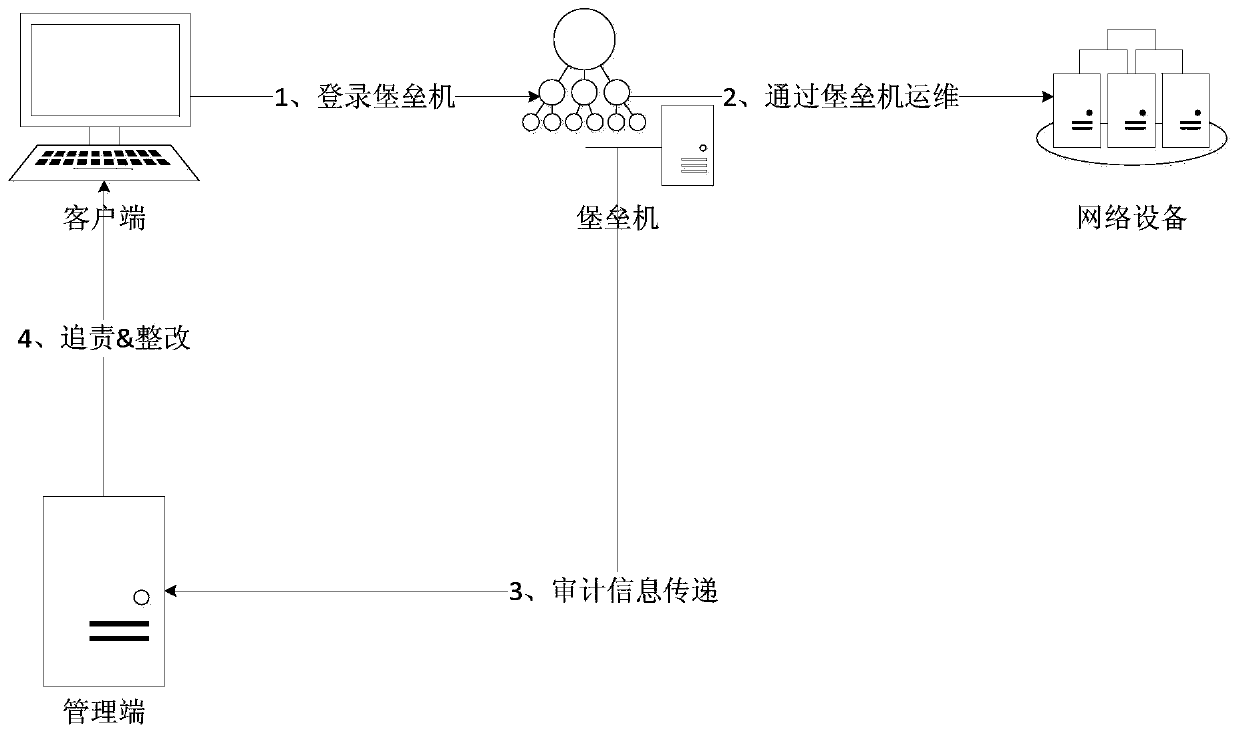
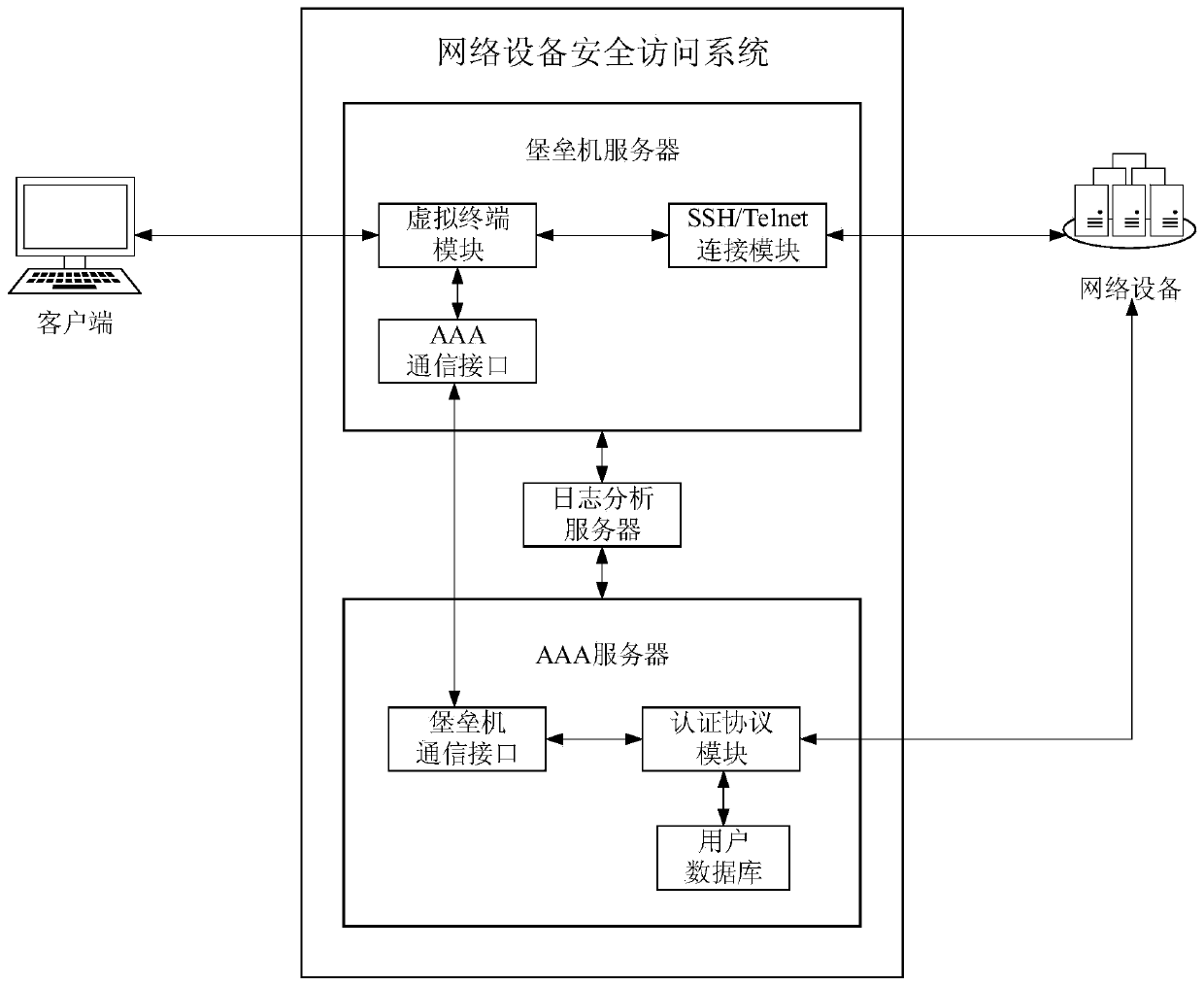
[0047] An important technical innovation feature of the system of the present invention is to use the authentication mode of the cached user account number and password by the AAA server to replace the local authentication mode of the traditional network device originally used when connecting to the managed network device. The cache password used in the system of the present invention is the account number and password of the user cached when the bastion host server receives the user login system connection request from the client. When the user initiates an operation connection request to control the network device, the cached password is sent by the bastion host server to the controlled network device, and then the network device sends the cached ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com