Network flow anomaly detection method
An anomaly detection and network traffic technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as infeasibility, difficulty in simulating traffic data by statistical methods, and difficulty in determining thresholds, resulting in false positives and false negatives. , to achieve the effect of good security, good real-time performance and strong adaptability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0078] In order to better understand the present invention, the content of the present invention is further illustrated below in conjunction with the examples, but the content of the present invention is not limited to the following examples.
[0079] The invention provides a network traffic abnormality detection method, which strengthens the network situation security monitoring, improves the automatic security early warning capability, and achieves the purpose of enhancing network security.
[0080] In order to solve the problems of the technologies described above, the technical scheme adopted in the present invention is as follows:
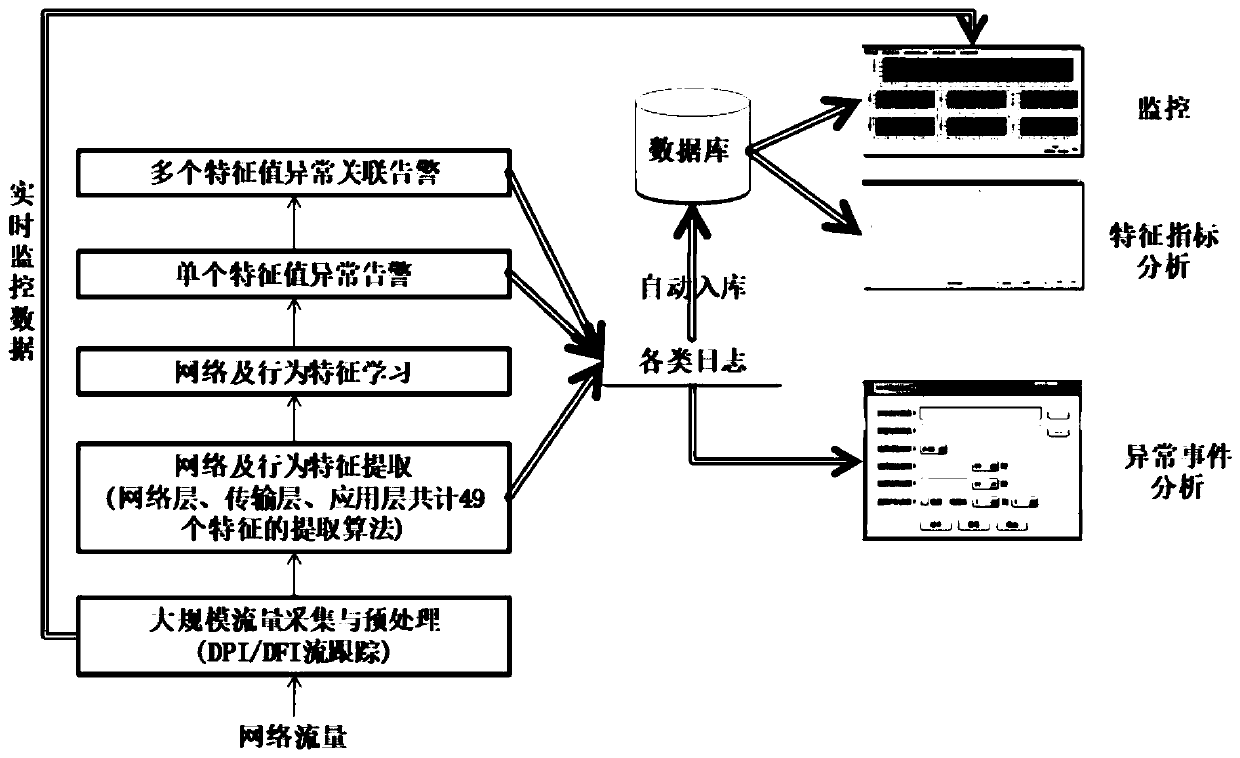
[0081] A network traffic anomaly detection method, the quantitative expression of cyberspace security situation includes the following steps:
[0082] (1) Flow feature collection and situation feature index extraction;
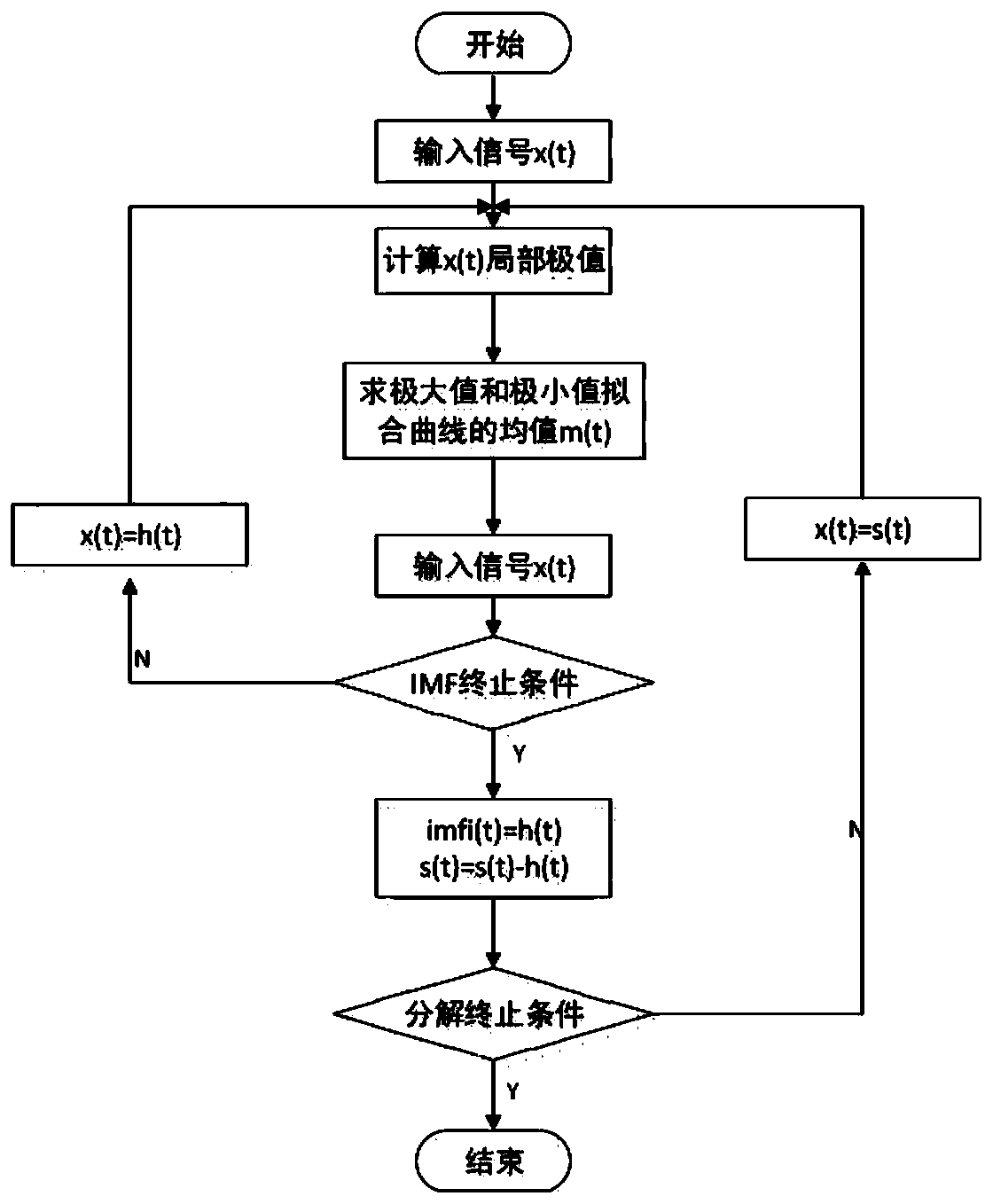
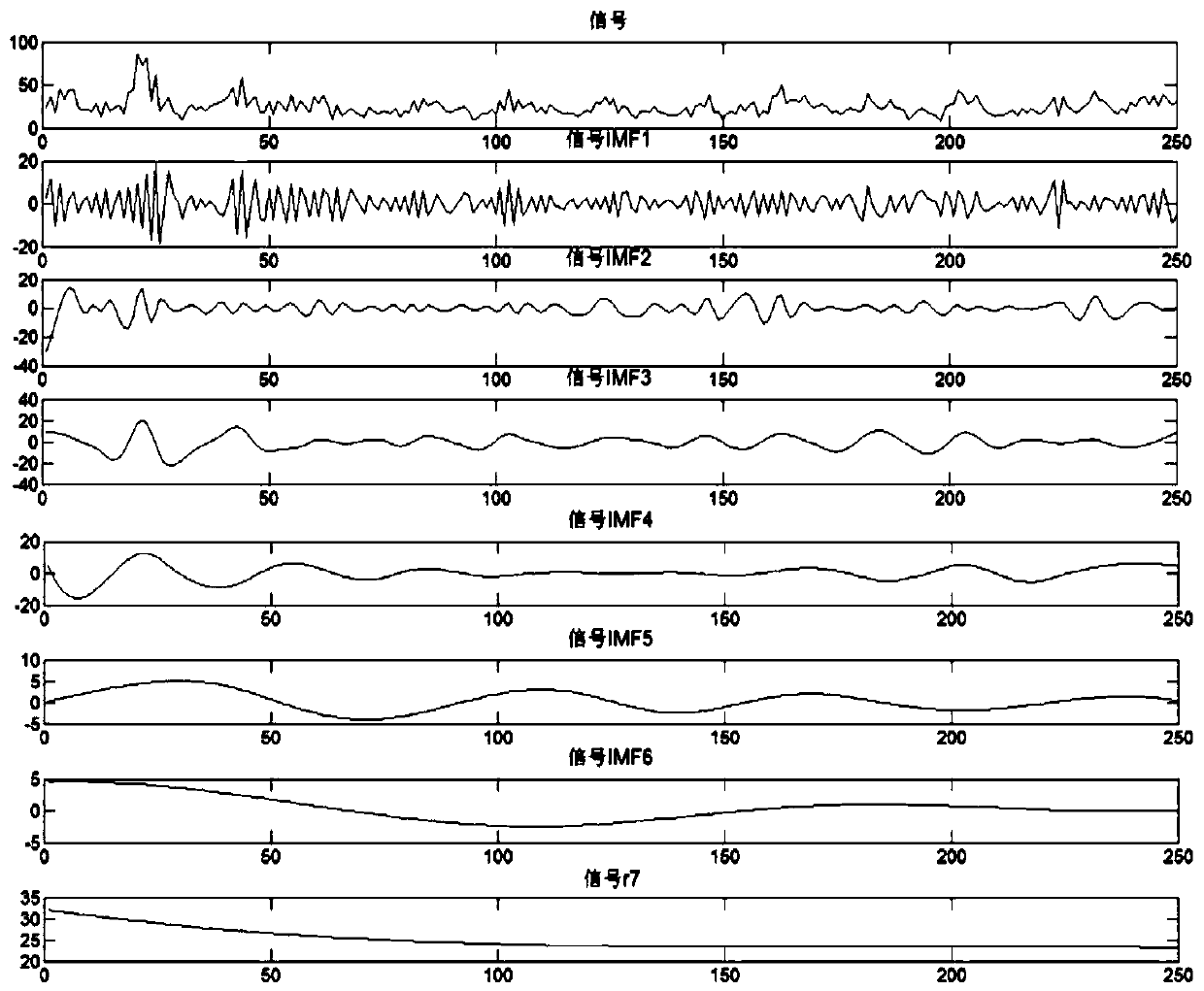
[0083] (2) Adaptive learning and abnormal analysis for situational characteristics;
[0084] (3) Network abnormal situatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com