Security access control system communicated with smart home and interaction method thereof
A family and smart technology, applied in the field of security access control system and its interaction, can solve the problems affecting the usability and function expansion of the security access control system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
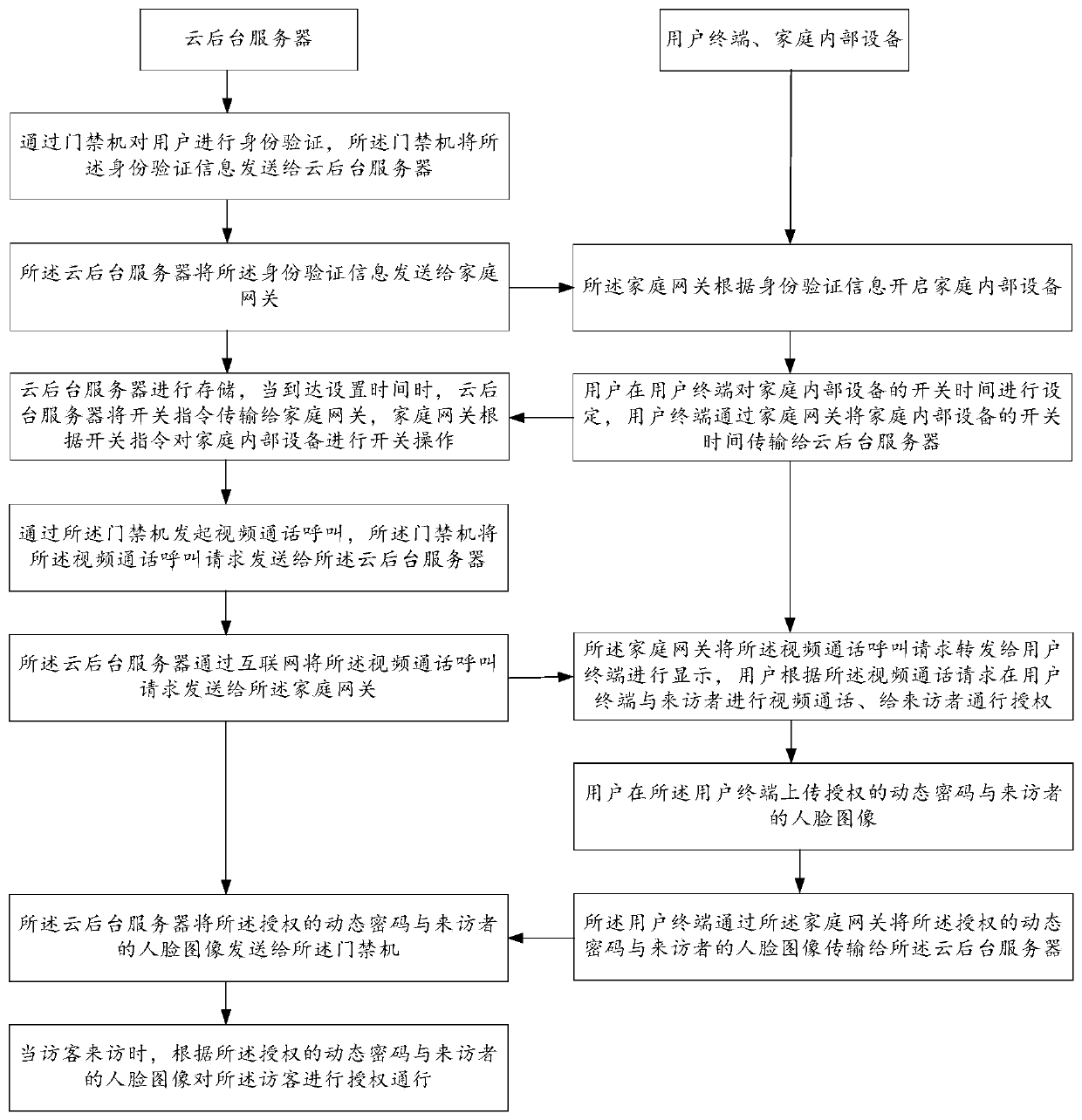
[0092] When a visitor enters the security access control system, the steps are as follows:
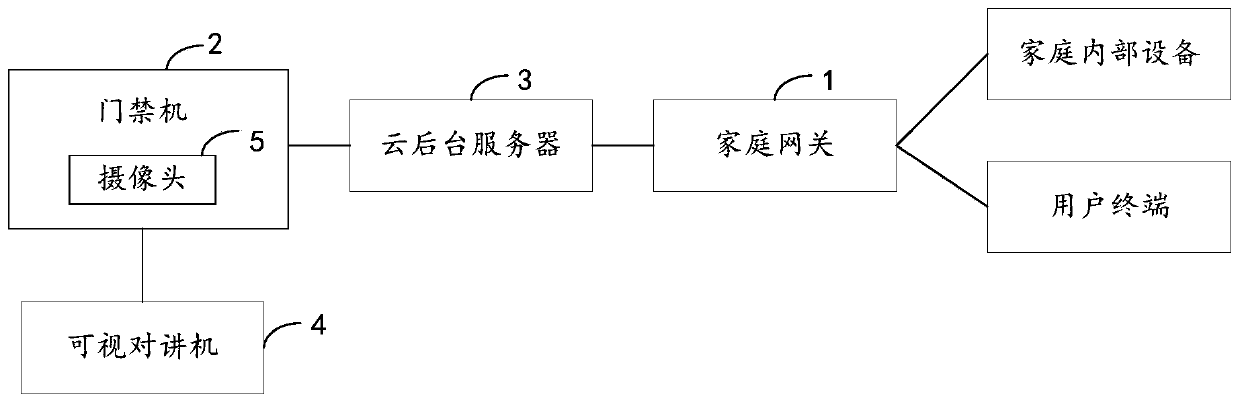
[0093] The visitor initiates a video call to the user through the access control machine, and the cloud background server transmits the video call to the home gateway;
[0094] Further, the home gateway of the smart home forwards the received video call request to the TV, mobile phone and other devices in the smart home;
[0095] Furthermore, when the owner connects to the video call, he can observe the video of the visitor on the mobile phone or TV, talk to the visitor, and authorize the visitor to pass;
[0096] Further, the access authorization instruction is transmitted to the cloud background server through the home gateway, and the cloud background server transmits the access authorization instruction to the access control machine, and the access control machine releases the visitor according to the access authorization instruction.
[0097] Or, when the visitor initiates a vide...
Embodiment 2
[0101] The steps of access control pre-authorization mode are as follows:
[0102] The user uses the mobile phone to upload the pre-authorized dynamic password or the visitor's face image, and the home gateway of the smart home transmits the pre-authorized dynamic password or the visitor's face image to the cloud background server;
[0103]Further, the cloud background server sends the pre-authorized dynamic password and the visitor's face image to the access control machine;
[0104] Furthermore, when visitors arrive, they can use dynamic passwords or faces to directly verify and obtain authorization to pass;
[0105] Furthermore, the access control machine transmits the visitor's visit information to the cloud background server, and then the cloud background server transmits it to the home gateway of the smart home, so as to prompt on the TV and mobile phone of the smart home.
Embodiment 3
[0107] When the visitor does not know the user's house number, the interaction steps of the security access control system are as follows:
[0108] Support visitors to directly make video calls with owners through mobile phones. During video calls, owners can upload visitor face information and authorization instructions to the home gateway of the smart home;
[0109] Further, the home gateway uploads the instruction to the cloud background server;
[0110] Further, the cloud background server sends the visitor's face information and authorized pass instructions to the access control machine, and the access control machine recognizes the visitor and performs the pass operation on the visitor who matches the visitor's face information;
[0111] Furthermore, the access control machine transmits the visitor's visit information to the cloud background server, and then the cloud background server transmits it to the home gateway of the smart home, so as to prompt on the TV and mobi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com