Malicious URL detection method and system
A detection method and detection system technology, applied in the field of network information security, can solve the problems of lack of negative samples, reduced accuracy, and difficulty in obtaining labeled data, etc., and achieve the effect of novel design and strong practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
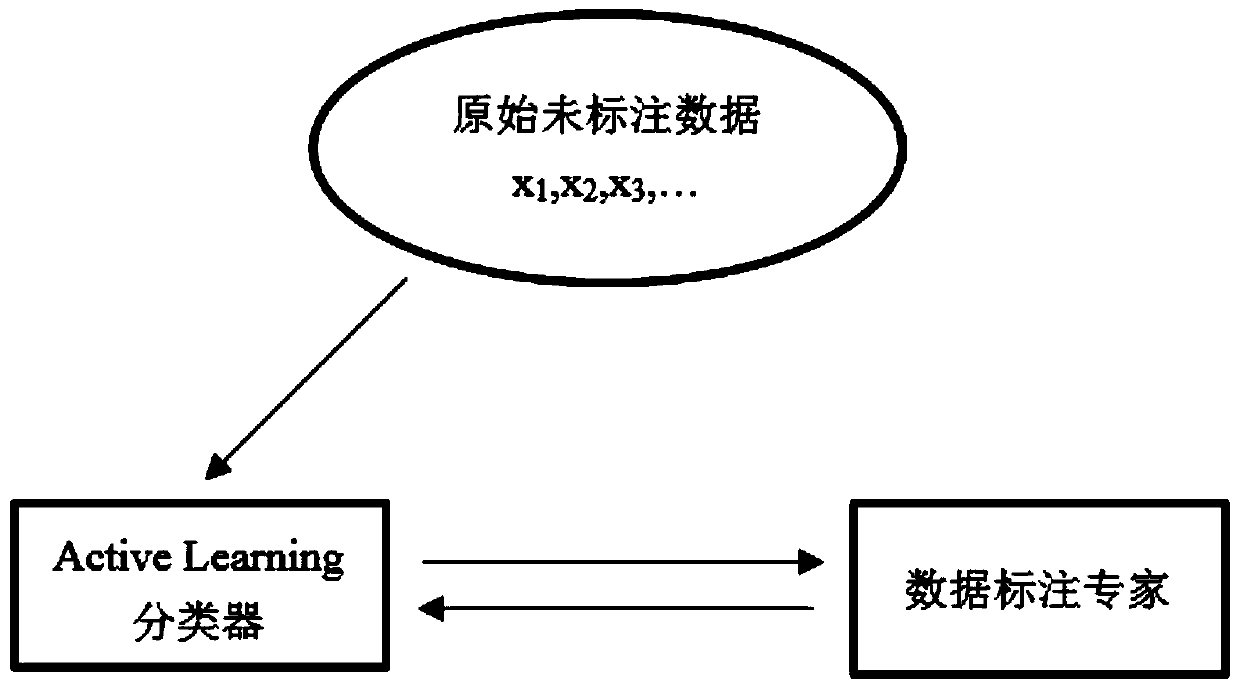
[0027] The technical problem to be solved by the present invention is: when performing URL detection, usually only a small part of malicious URLs and a large number of unlabeled URL samples can be obtained, and there is a lack of reliable enough negative examples, which means that we cannot directly use conventional machines Learning algorithms. Whereas if we simply solve it in an unsupervised manner, the annotation information of known malicious URLs is difficult to fully exploit and may fail to achieve satisfactory performance. The technical idea proposed by the present invention for this technical problem is: construct a malicious URL detection method and system, and combine active learning (Active Learning, AL for short) with semi-supervised (two-step Postive and Unlabled Learning, PU for short) . In the case of limited manual labeling workload, a malicious URL detection model was developed for the URL dataset. Compared with the unsupervised model and the semi-supervised ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com