Method, storage medium, electronic device and system for preventing bad dll injection
A bad, function-injected technology, applied in digital data processing, instruments, calculations, etc., can solve problems such as client/program/software crashes, platform software leaks, hacking, etc., to improve experience, improve security, The effect of preventing crashes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
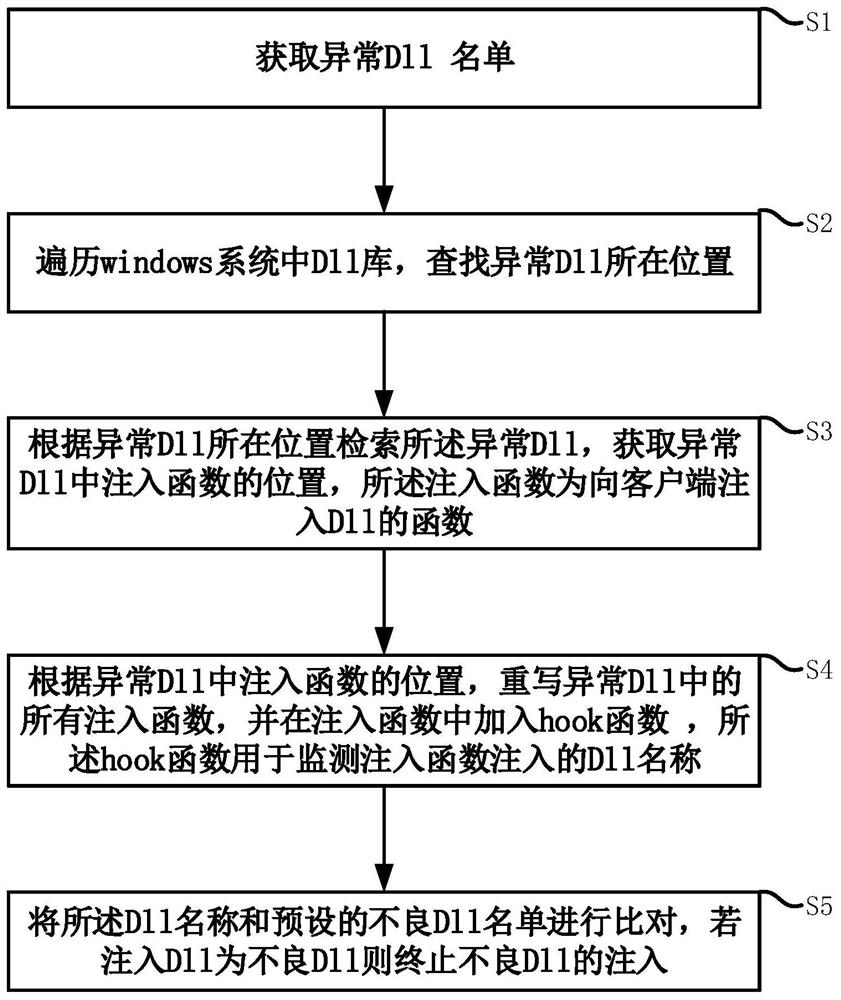
[0056] An embodiment of the present invention provides a method for preventing bad DLL injection, which includes:
[0057] S1: Obtain a list of abnormal DLLs.
[0058] For software, it is impossible to run stably when it runs in different environments. The reason for the unstable operation of the software running in the Windows system is generally not the use of its own functions to run, but the abnormality that occurs when calling the DLL in the Windows system. For these abnormal DLLs, if it is necessary to prevent them from causing software instability, crashes, and intrusion, etc., further processing is required.
[0059] S2: traverse the DLL library in the Windows system to find the location of the abnormal DLL.
[0060] To handle the abnormal DLL, you must first find the location of the DLL. In Windows, its DLL is stored in the DLL library, so you can directly find the location of the abnormal DLL in the DLL library of the Windows system.
[0061] S3: Retrieve the abno...
Embodiment 2
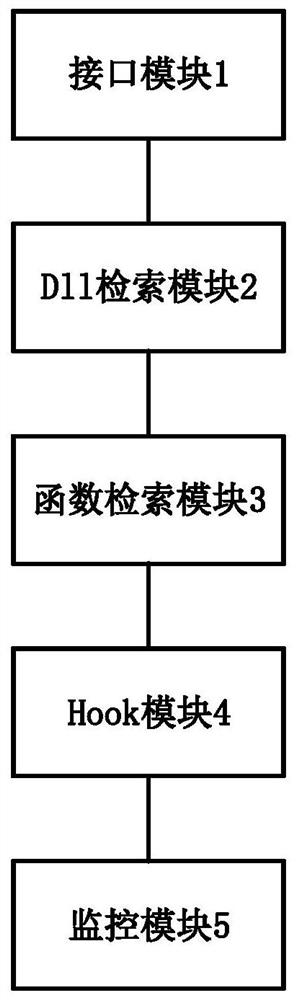
[0078] An embodiment of the present invention provides a system for preventing bad DLL injection, which includes:
[0079] The interface module is used to obtain the abnormal DLL list;
[0080] The DLL retrieval module is used to traverse the DLL library in the Windows system to find the location of the abnormal DLL;
[0081] The function retrieval module is used to retrieve the abnormal DLL according to the location of the abnormal DLL, and obtain the position of the injected function in the abnormal DLL, and the injected function is a function of injecting the DLL to the client;
[0082] The Hook module is used to rewrite all injected functions in the abnormal DLL according to the position of the injected function in the abnormal DLL, and add a hook function in the injected function, and the hook function is used to monitor the DLL name injected by the injected function;
[0083] The monitoring module is used to compare the name of the DLL with a preset list of bad DLLs, an...
Embodiment 3
[0087] The third embodiment of the present invention provides a computer-readable storage medium, on which a computer program is stored. When the program is executed by a processor, the video recommendation method provided in any embodiment of the present invention is implemented. The method includes:
[0088] Obtain each watched video and each unwatched video of the target user within a preset time period, wherein the unwatched video includes a first unwatched video and a second unwatched video;
[0089] According to the collaborative filtering algorithm and each watched video, determine the candidate recommendation set from each first unwatched video;
[0090] Add the second unwatched video to the candidate recommendation set according to the preset adding rules, and determine each added recommendation set;
[0091] According to the user viewing information or video attribute information corresponding to each recommended video in each added recommendation set, and the user v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com