Deep attention rumor identification method and device based on ternary features
A technology of attention and attention model, applied in special data processing applications, instruments, text database query, etc., can solve the problems of inaccurate identification and single use of features, and achieve the effect of overcoming single features and improving accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
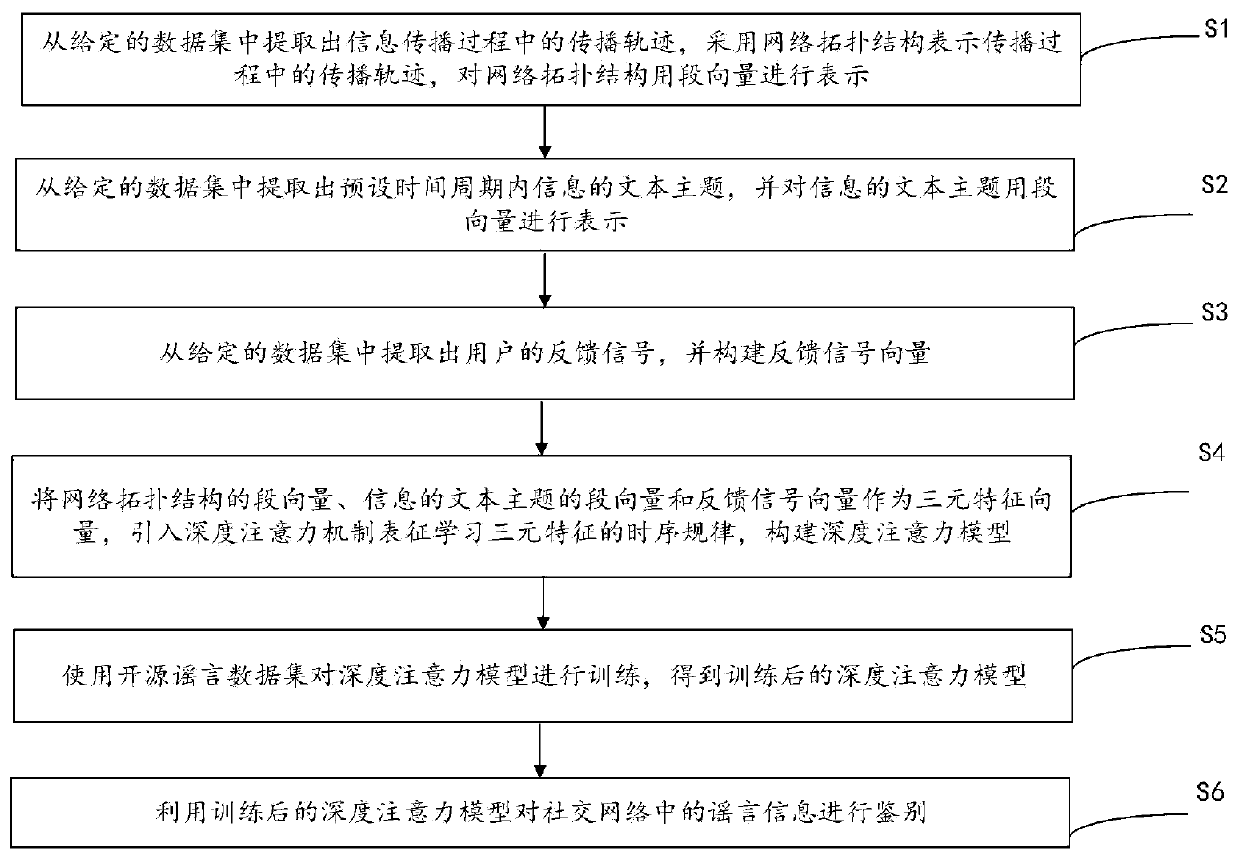
[0064] This embodiment provides a deep attention rumor identification method based on triple features, please refer to figure 1 , the method includes:
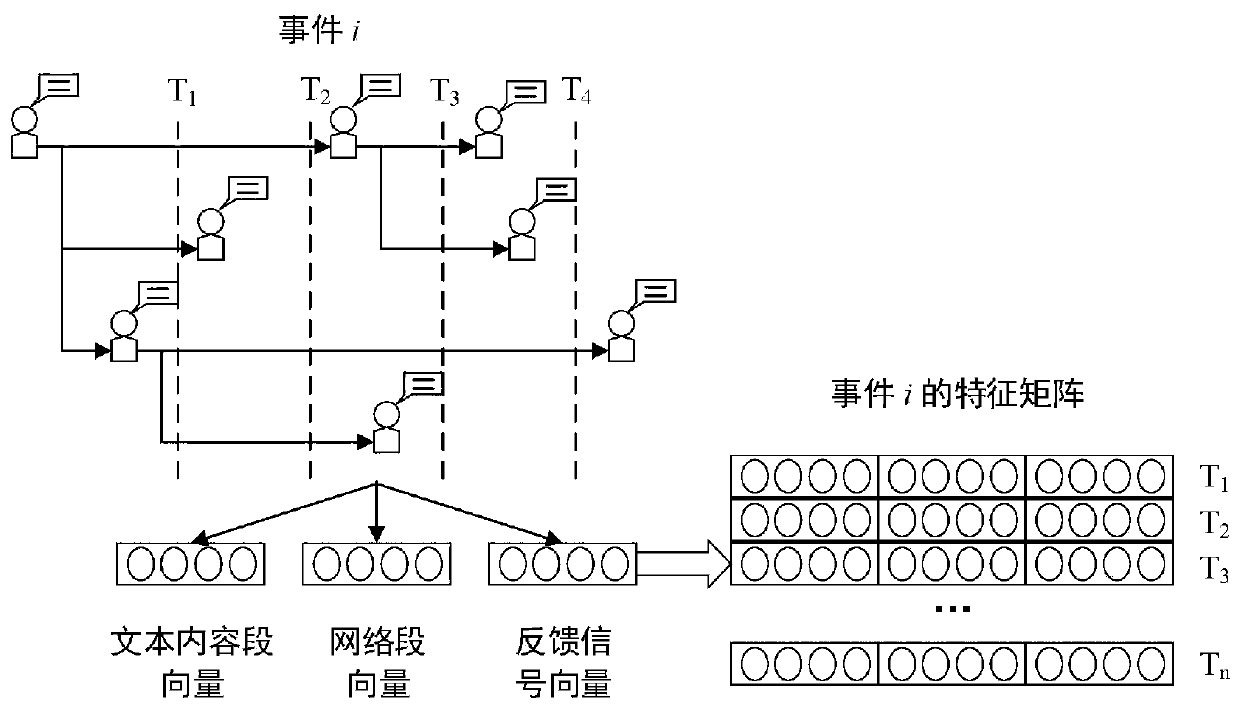
[0065] Step S1: Extract the propagation track during the information dissemination process from the given data set, use the network topology structure to represent the propagation track during the propagation process, and express the network topology structure with segment vectors.
[0066] Step S2: Extract the text topic of the information within the preset time period from the given data set, and represent the text topic of the information with a segment vector;
[0067] Step S3: extract the user's feedback signal from the given data set, and construct a feedback signal vector.
[0068] Specifically, due to the temporal variability of the social network itself, in the traditional methods for identifying rumors on social networks, the model is only constructed for the overall data characteristics or the original data content...
Embodiment 2
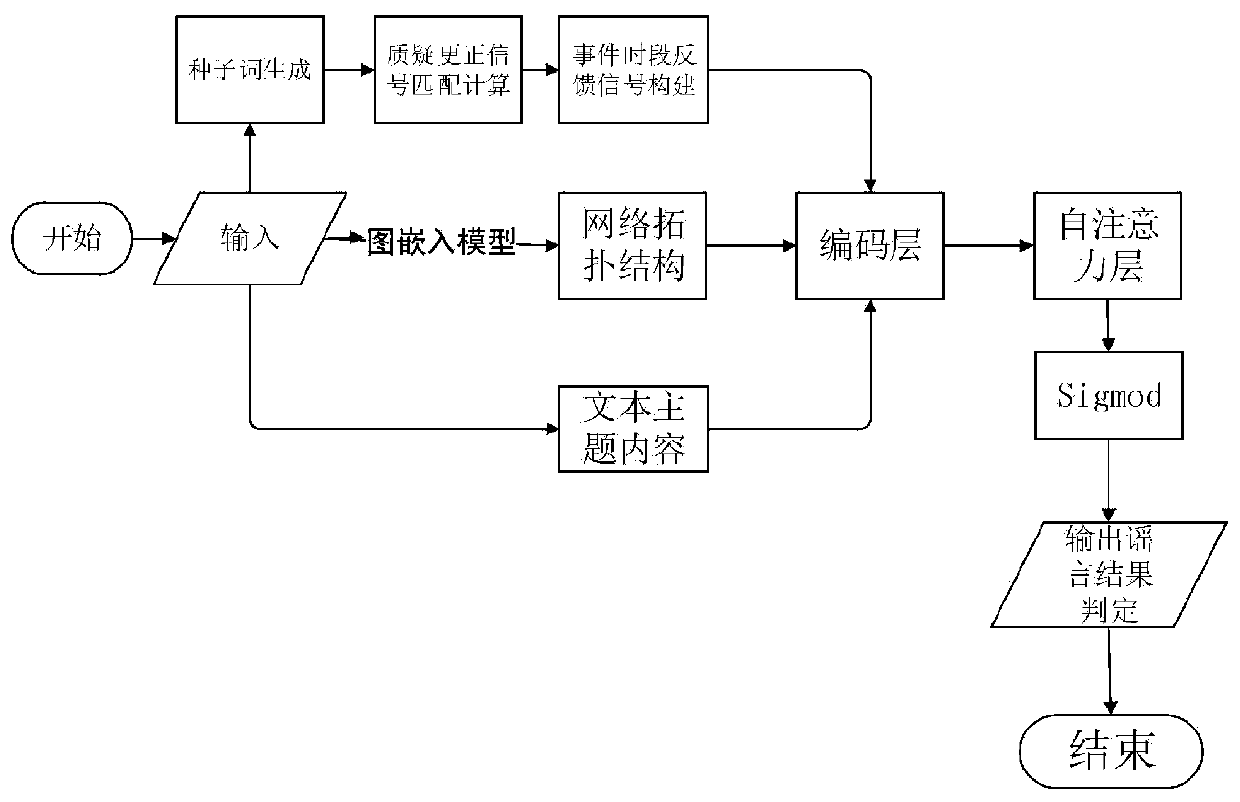
[0152] Based on the same inventive concept, this embodiment provides a deep attention rumor identification device based on ternary features, please refer to Figure 7 , the device consists of:
[0153] The propagation trajectory extraction module is used to extract the propagation trajectory in the process of information dissemination from a given data set, using the network topology to represent the propagation trajectory in the propagation process, and expressing the network topology with a segment vector;
[0154] The text topic extraction module is used to extract the text topic of the information within the preset time period from the given data set, and express the text topic of the information with a segment vector;
[0155] The user feedback signal extraction module is used to extract the user's feedback signal from a given data set, and construct a feedback signal vector;
[0156] The attention module is a building block, which is used to use the segment vector of th...
Embodiment 3
[0161] Based on the same inventive concept, the present application also provides a computer-readable storage medium 300, please refer to Figure 8 , on which a computer program 311 is stored, and when the program is executed, the method as described in the first embodiment is realized.
[0162] Since the computer-readable storage medium introduced in the third embodiment of the present invention is the readable storage medium used to implement the deep attention rumor identification method based on the ternary feature in the first embodiment of the present invention, it is based on the introduction in the first embodiment of the present invention Those skilled in the art can understand the specific structure and deformation of the computer-readable storage medium, so details will not be repeated here. All computer-readable storage media used in the method in Embodiment 1 of the present invention fall within the scope of protection intended by the present invention.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com