Request data verification system and method
A technology for requesting data and verifying methods, applied in the field of network security, can solve the problems of high access platform cost, less security processing, security risks, etc., to reduce the cost of intranet system access platform, save manpower and time costs , The effect of saving the time of review and risk control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
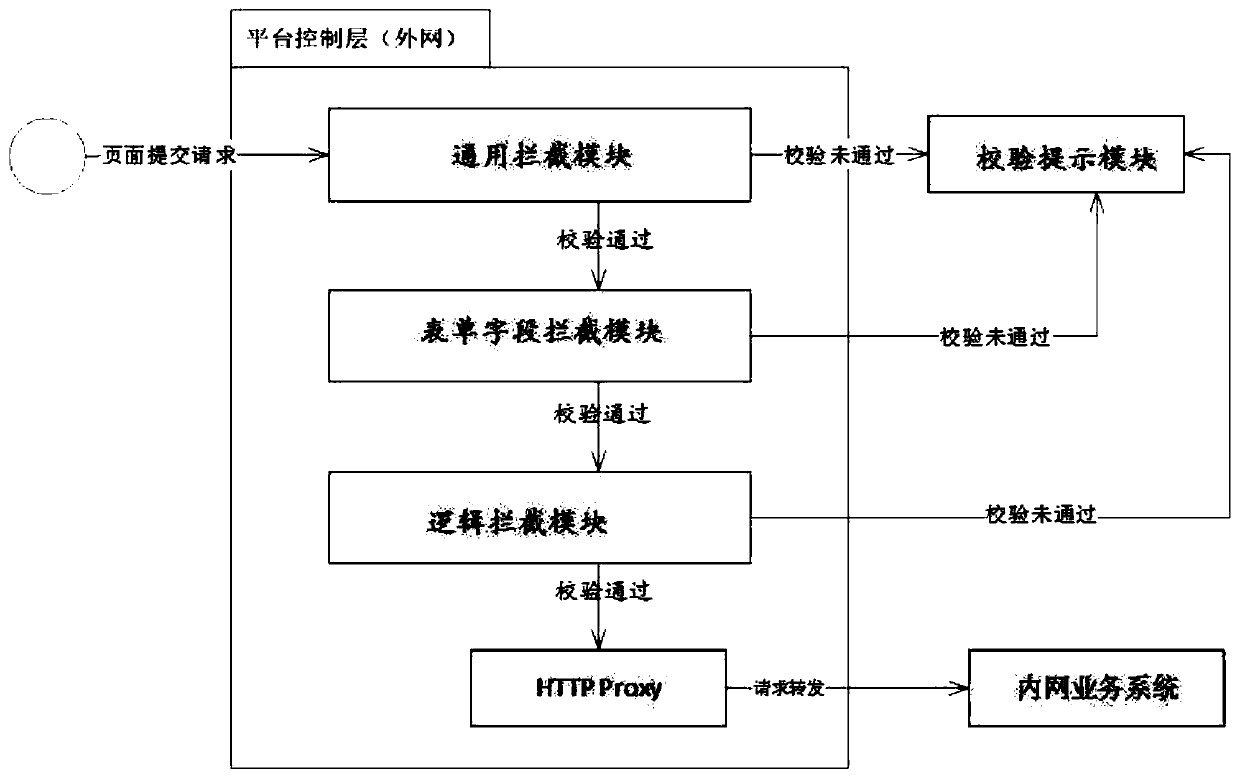
[0031] like figure 1 As shown, this embodiment provides a verification system for request data, including:
[0032] The general interception module is used to receive the request data sent by the user from the external network platform to the internal network platform, and perform the first dimension verification on the request data, and continue to transmit the request after the request data passes the verification data;
[0033] The form field interception module is used to receive the request data transmitted from the general interception module, and verify the page form information on the request data, and continue to transmit the request data after the verification is passed. request data;
[0034] A logic interception module, configured to receive the request data transmitted from the form field interception module, and perform application programming interface verification on the request data, and when the request data passes the verification, the requesting data to ...
Embodiment 2
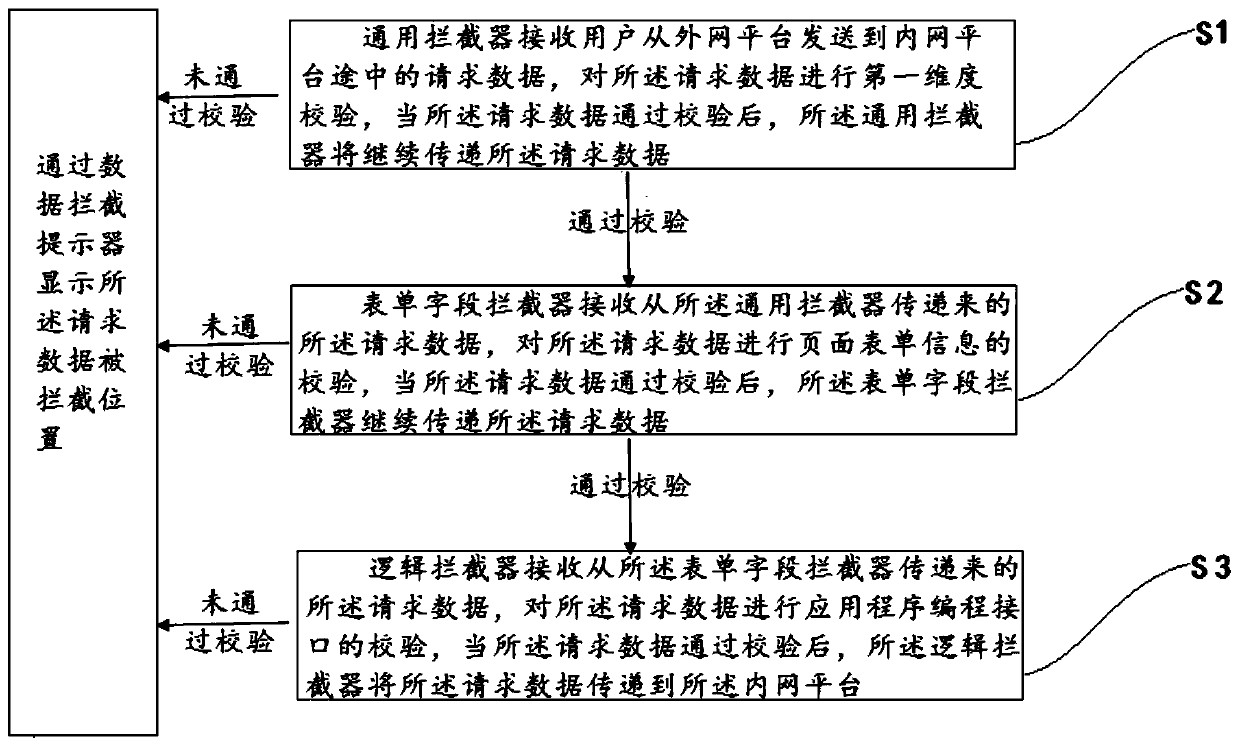
[0040] like image 3 As shown, this embodiment provides a method for verifying request data, including the following steps:
[0041] S1: The general interceptor receives the request data sent by the user from the external network platform to the internal network platform, and performs the first dimension verification on the request data. When the request data passes the verification, the general interceptor will continue passing said request data;
[0042] S2: The form field interceptor receives the request data transmitted from the general interceptor, and verifies the page form information on the request data. When the request data passes the verification, the form field interceptor continue to pass said request data;
[0043] S3: The logic interceptor receives the request data transmitted from the form field interceptor, and performs application programming interface verification on the request data, and when the request data passes the verification, the logic interceptor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com