Data secrecy method and system for MapReduce computing
A data confidentiality and data technology, applied in transmission systems, electrical components, etc., can solve problems such as high-performance overhead of failure, unsupported user shuffle function, high-performance overhead, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
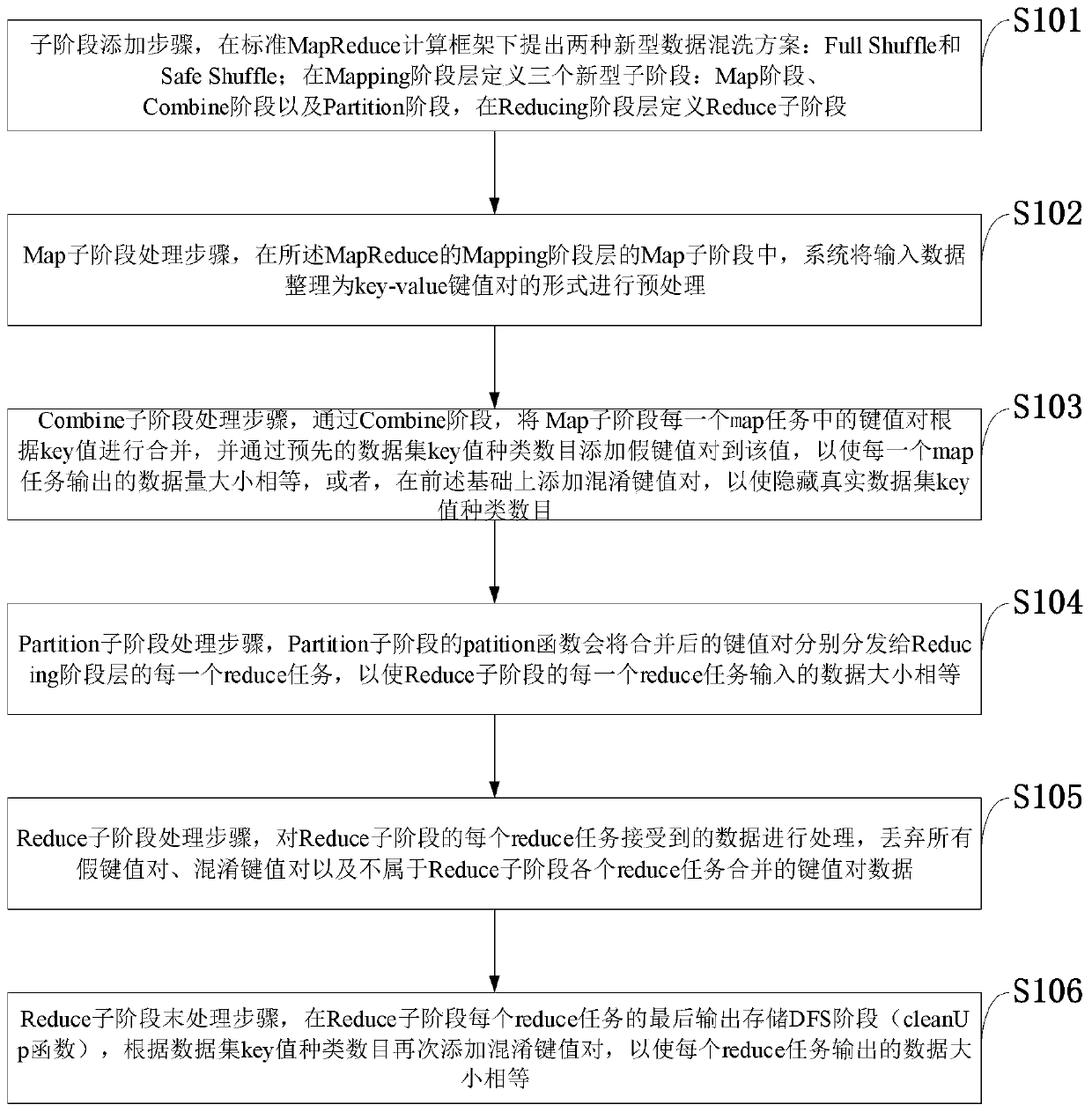
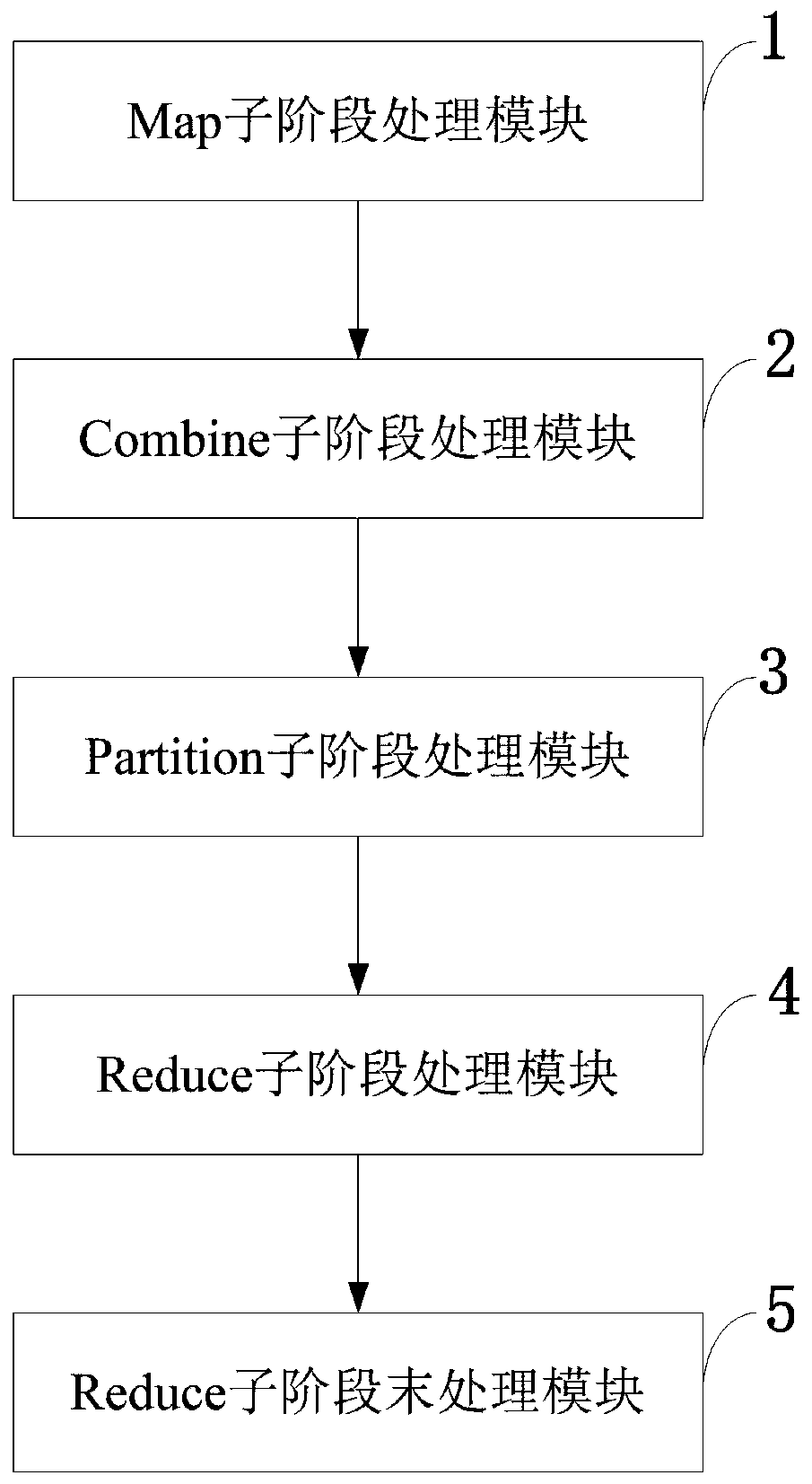
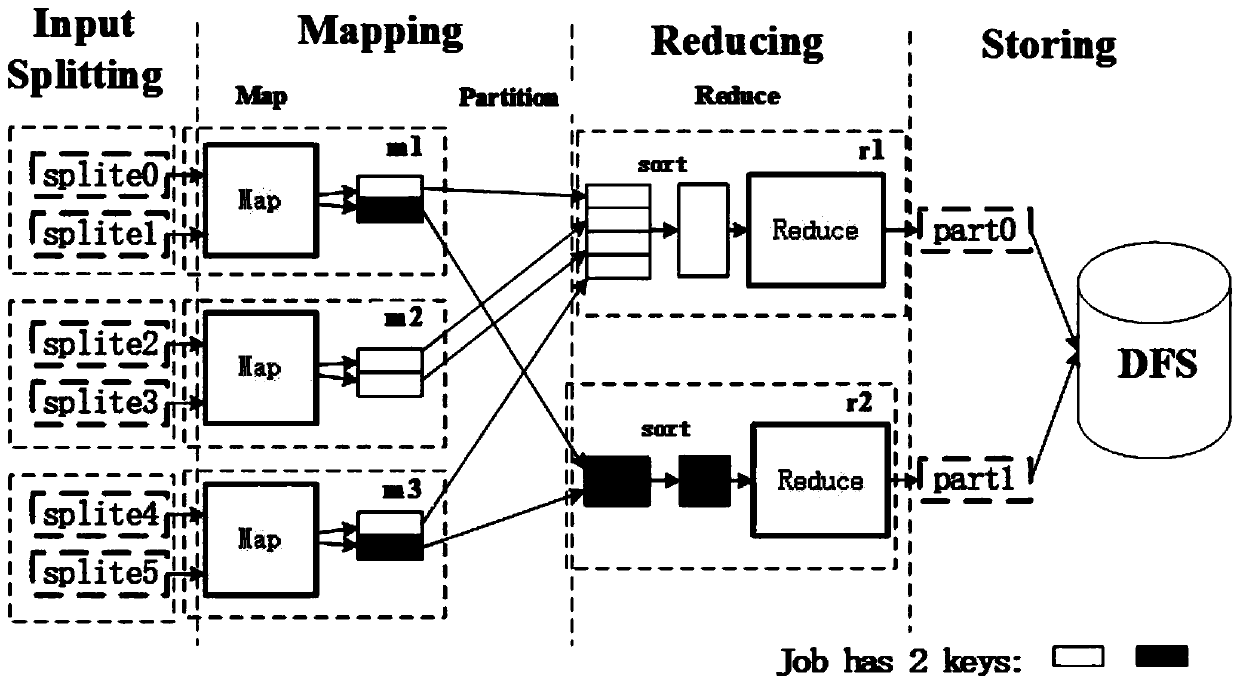
[0077] Such as Figure 4 As shown, compared with the standard MapReduce process (such as image 3 , standard MapReduce framework), this embodiment mainly defines three new sub-phases in the Mapping phase layer: Map phase, Combine phase and Partition phase, and defines the Reduce sub-phase in the Reducing phase layer. This scheme conforms to the indistinguishability of the input and output of the map task, and the indistinguishability of the input and output of the reduce end. The amount of data received and stored by each reduce task is equal.
[0078] Assume that the data set input used by the user to submit the job is D, |D| indicates the size of the input data, |.| indicates the size of the encrypted data, M indicates the number of map tasks, R indicates the number of reduce tasks, and Map_function is The map main function in each map task, Reduce_function is the reduce main function in each reduce task, the user-defined allocation function User_Partition_function and the ...
Embodiment 2
[0086] In this embodiment, the way of adding fake data is used to realize data confidentiality, and at the same time, the number K of types of key values is protected. In this embodiment, MapReduce is rewritten to meet the indistinguishability of the input and output of the map task, and the amount of data received by each reduce task that is indistinguishable from the input and output of the Reduce end is equal.
[0087] Such as Figure 5 As shown, compared with the standard MapReduce process (such as image 3 , standard MapReduce framework), this embodiment mainly defines three new sub-phases in the Mapping phase layer: Map phase, Combine phase and Partition phase, and defines the Reduce sub-phase in the Reducing phase layer. This scheme conforms to the indistinguishability of the input and output of the map task, and the indistinguishability of the input and output of the reduce end. The amount of data received and stored by each reduce task is equal.
[0088] Assume th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com