Voice interaction method and Bluetooth equipment
A Bluetooth device and voice interaction technology, applied in speech analysis, speech recognition, short-distance communication services, etc., can solve problems such as poor user experience, client occupancy, and the inability of Bluetooth devices to access the client, so as to improve the experience. , the effect of strong ease of use and practicality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
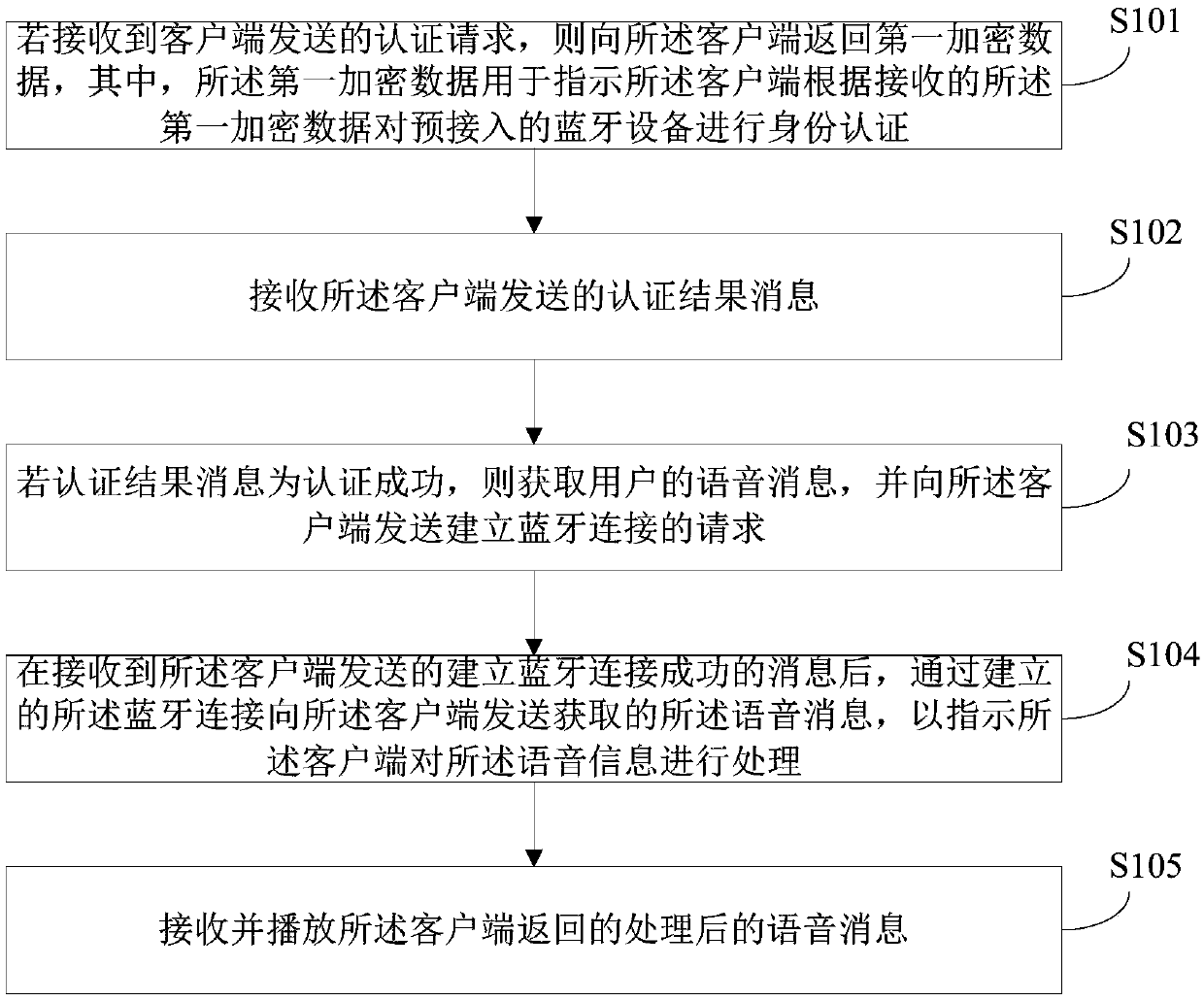
[0033] figure 1 It is a schematic flowchart of the voice interaction method provided by Embodiment 1 of the present invention. The execution subject of this embodiment is a Bluetooth device. The method may include the following steps:
[0034] S101: If an authentication request sent by the client is received, return first encrypted data to the client, where the first encrypted data is used to instruct the client to The connected Bluetooth device performs identity authentication.
[0035] It should be noted that the bluetooth device includes but not limited to bluetooth products that support voice input such as bluetooth earphones and bluetooth speakers; It is called APP (Application); the authentication request includes a section of random number, which can be randomly generated by the mobile terminal or other equipment according to the needs; in addition, in order to distinguish it from the encrypted data sent by the subsequent client, the present invention sends the bluetoo...
Embodiment 2
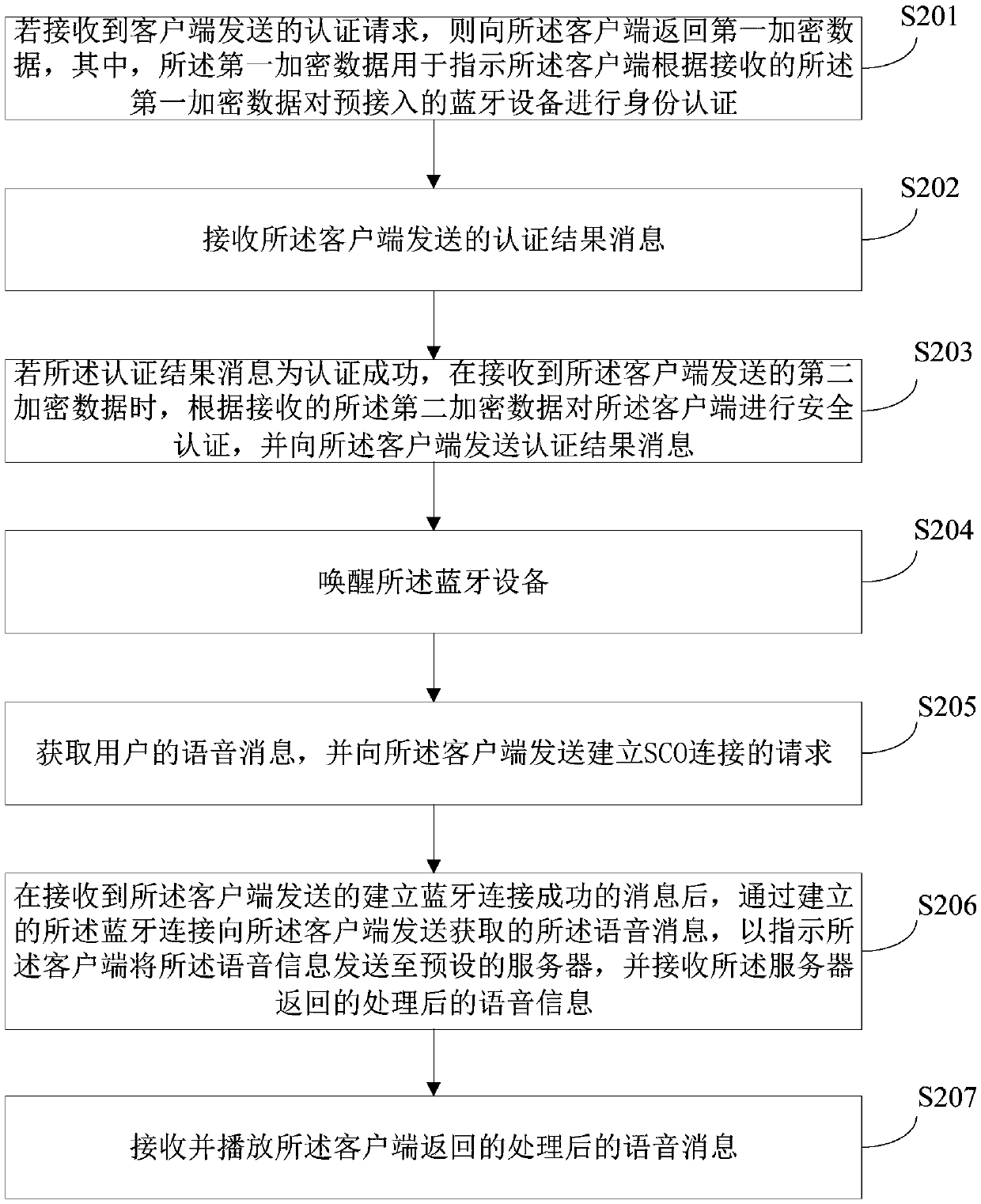
[0062] figure 2 The flow diagram of the voice interaction method provided by Embodiment 2 of the present invention is a further refinement and description of step S102 in Embodiment 1 above. The execution subject of this embodiment is a Bluetooth device, and the method may include the following steps:
[0063] S201: If the authentication request sent by the client is received, return first encrypted data to the client, where the first encrypted data is used to instruct the client to The connected Bluetooth device performs identity authentication.
[0064] S202: Receive an authentication result message sent by the client.
[0065] Wherein, the above steps S201-S202 are the same as the steps S101-S102 in the first embodiment, and the specific implementation process can refer to the description of the steps S101-S102, which will not be repeated here.
[0066] S203: If the authentication result message indicates that the authentication is successful, when receiving the second e...
Embodiment 3
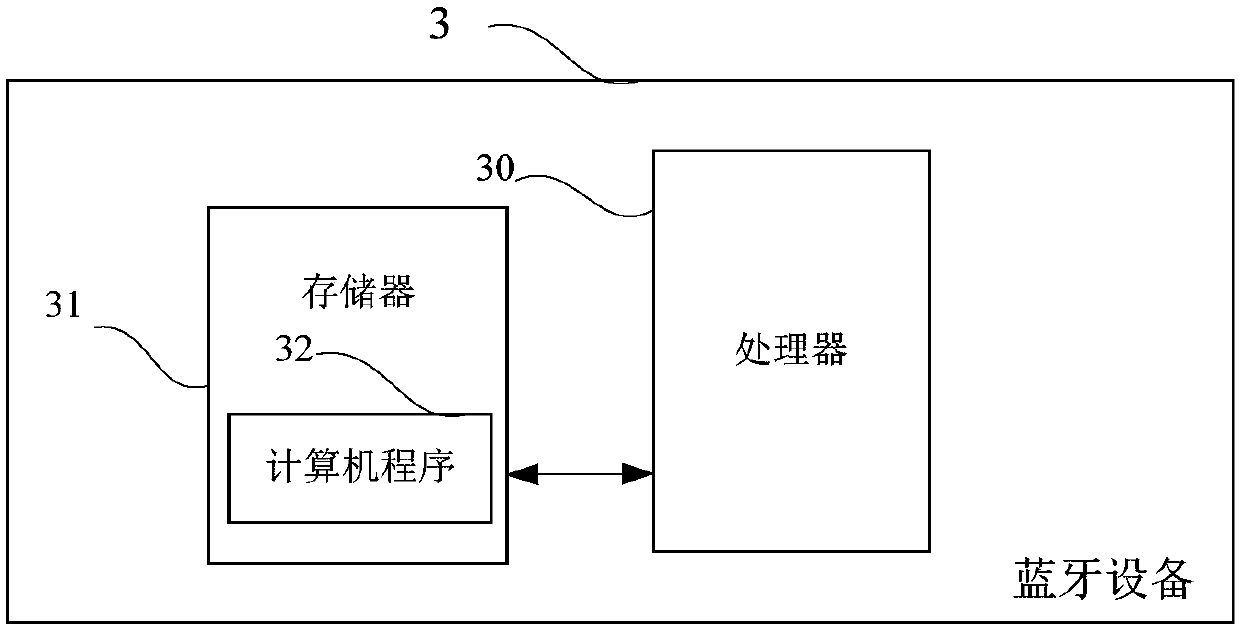
[0083] image 3 It is a schematic structural diagram of the bluetooth device provided by Embodiment 3 of the present invention. Such as image 3 As shown, the Bluetooth device 3 of this embodiment includes: a processor 30 , a memory 31 , and a computer program 32 stored in the memory 31 and operable on the processor 30 . When the processor 30 executes the computer program 32, the steps in the first method embodiment above are implemented, for example figure 1 Steps S101 to S105 are shown. Or, realize the steps in the second embodiment of the above method, for example figure 2 Steps S201 to S207 shown in
[0084] The Bluetooth device may include, but not limited to, a processor 30 and a memory 31 . Those skilled in the art can understand that, image 3 It is only an example of the bluetooth device 3, and does not constitute a limitation to the bluetooth device 3. It may include more or less components than shown in the figure, or combine certain components, or different ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com