File encryption and decryption processing method, device and equipment and readable storage medium
A processing method and file encryption technology, applied in the field of data processing, can solve problems such as file offset data length granularity, misalignment, and decryption failure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
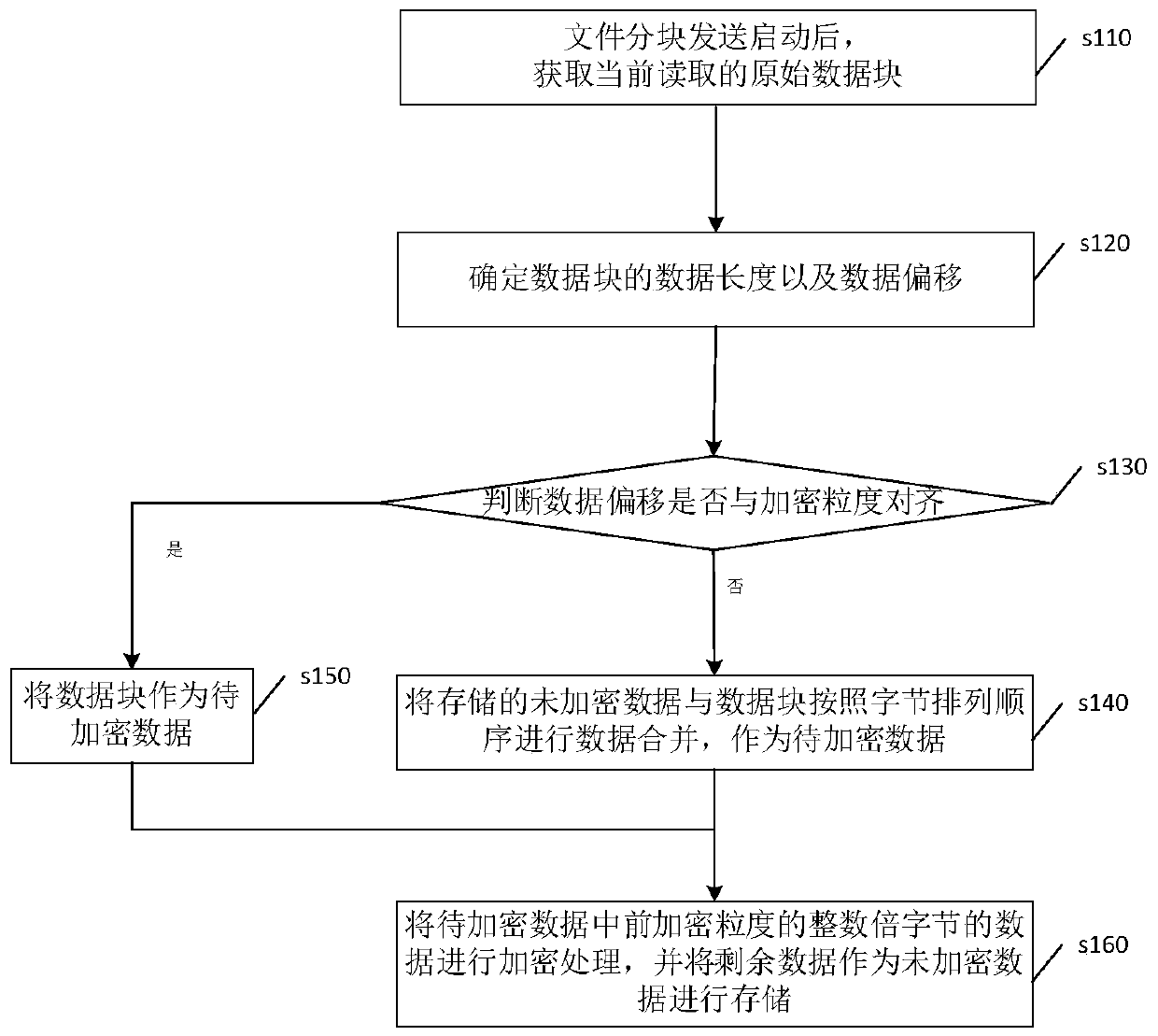
[0061] Please refer to figure 1 , figure 1 A flow chart of a file encryption processing method provided in this embodiment; the method mainly includes:
[0062] Step s110, after the block sending of the file is started, the currently read original data block is obtained;
[0063] First, when the software reads and writes file data for encryption and decryption, the sender of the software sends a file and reads the files to be sent in batches. During the reading process, the original data block is read in blocks. The currently read data block in the process is called the original data block because the data in the data block is original unencrypted data.
[0064] Step s120, determining the data length and data offset of the data block;
[0065] The data length refers to the data length of the currently read original data block. For example, when every 20 bytes is read as a data block, the data length of the data block is 20 bytes.
[0066] Every time a process reads data, t...
Embodiment 2
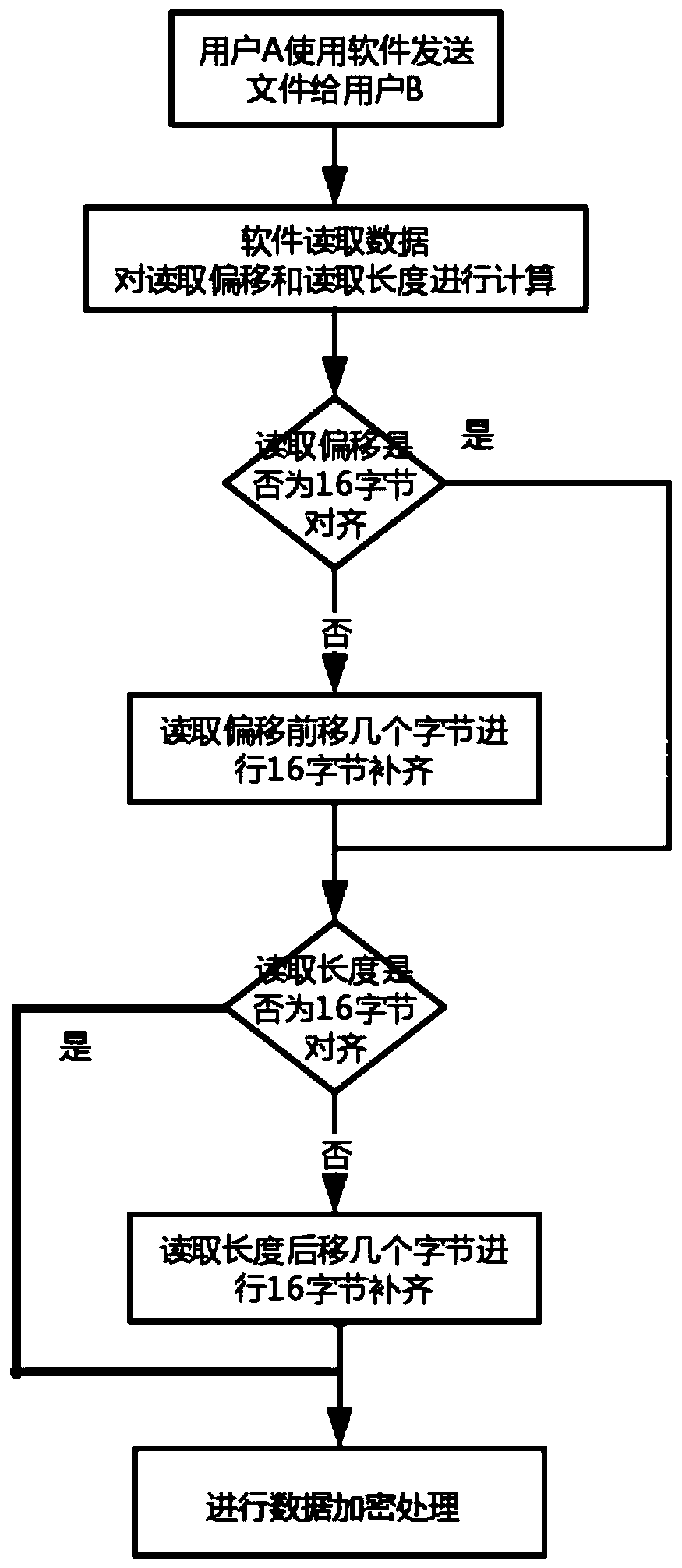
[0083] In order to deepen the understanding of the file encryption method introduced in the above-mentioned embodiments, in this embodiment, the AES encryption algorithm with a key length of 128 bits and an encryption granularity of 16 bytes is used in this embodiment. The size of the file is 100 bytes, and every 20 characters Take data reading as a data block as an example to introduce the implementation method.
[0084] When reading 20 bytes starting from 0 for the first time, the file offset read for the first time is 0, the length of the read content is 20, the file offset 0 is an integer multiple of 16, no correction is required, and the length is 20 It is not an integer multiple of 16, 20=16+4, the encryption process after reading 20 bytes is: encrypt the first 16 bytes, and keep the remaining 4 bytes unencrypted, but need to be saved.
[0085] The second time read 20 bytes from the file offset of 20, the file offset is 20, not an integer multiple of 16, 20=16+4, you nee...
Embodiment 3
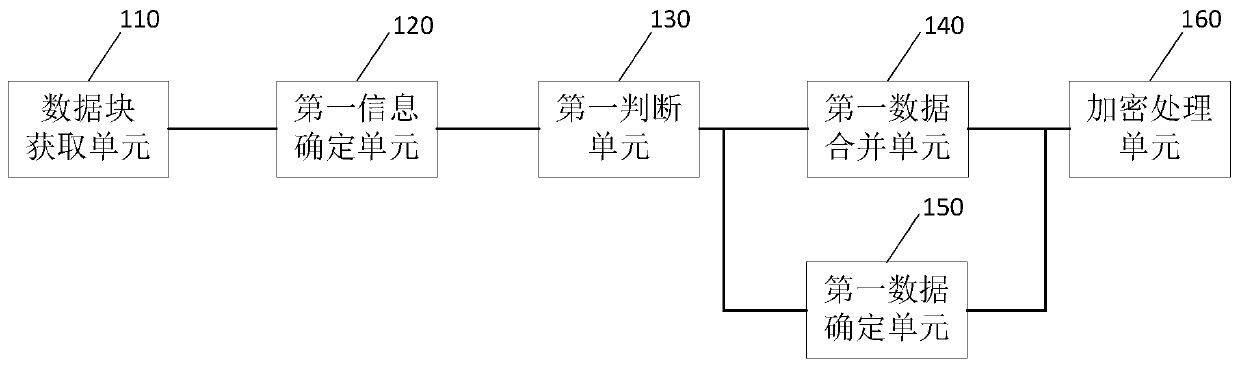
[0089] Based on the above-mentioned embodiments, in order to increase the acquisition speed of the original data block, thereby further increasing the speed of file encryption processing, optionally, after the file block sending is started, the file reading process of the monitoring application can be used to obtain the currently read the original data block.
[0090] By monitoring the read and write file operations of the application, encryption processing can be performed while determining the currently read data block. Compared with passively receiving data, active monitoring to obtain data can significantly increase the speed of data acquisition.
[0091] In this embodiment, only the above data acquisition method is used as an example for introduction, other specific data acquisition methods may refer to the introduction of this embodiment, and will not be repeated here.
[0092] Further, after encrypting the data, in order to strengthen the closeness of the relationship b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com