Honeypot service port self-adaptive application method and system based on attack behavior analysis
A service port and behavior analysis technology, which is applied in the self-adaptive application field of honeypot service port, can solve the problems of increasing the detection by the attacker, increasing the running time of the system, increasing the probability of being detected, and achieving the effect of increasing the chance of trapping
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] Preferred embodiments of the present invention will be described below in conjunction with the accompanying drawings. It should be understood that the embodiments described here are only used to illustrate and explain the present invention, and are not intended to limit the present invention.
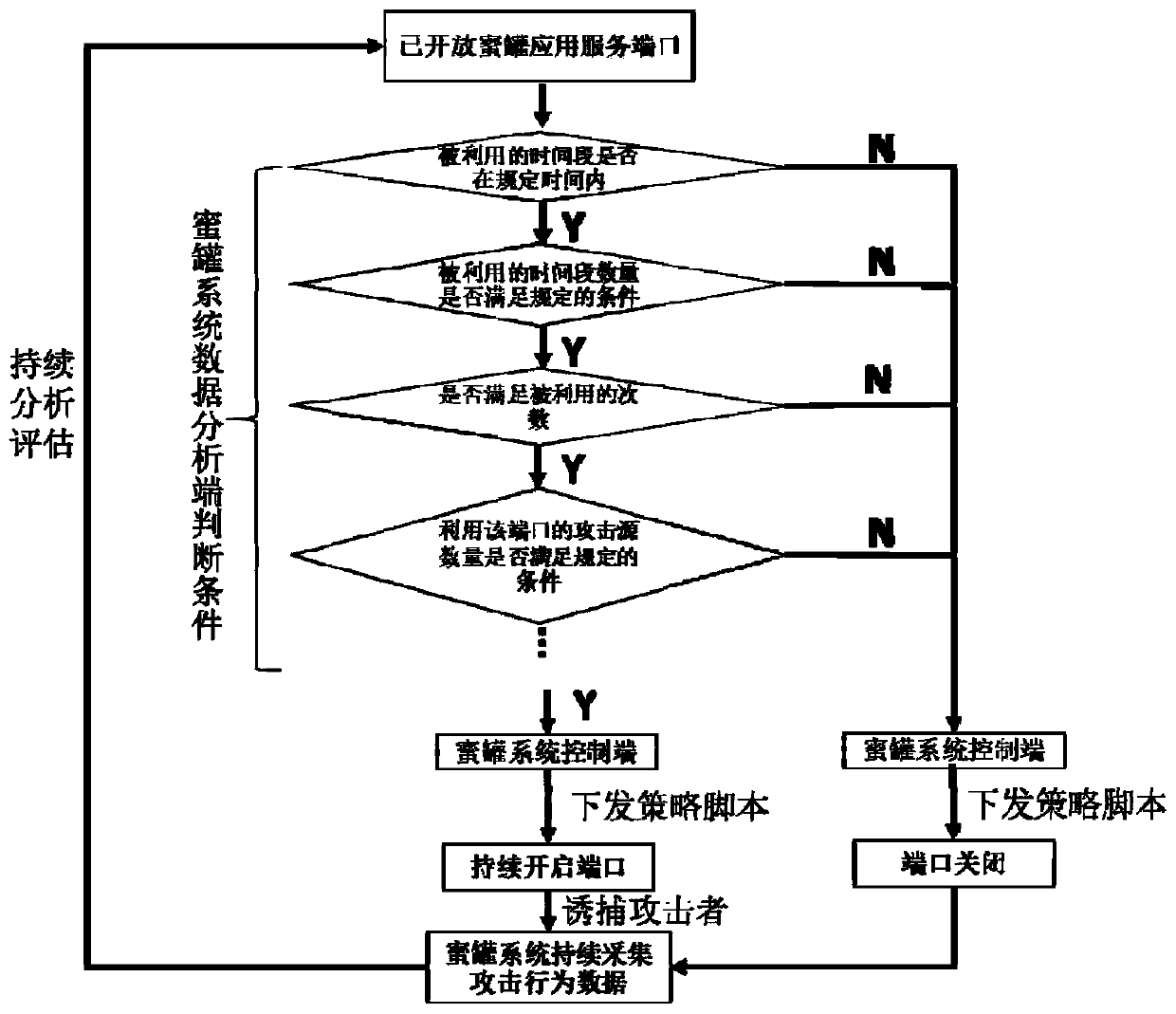
[0034] combine figure 1 As shown, the present invention provides a honeypot service port adaptive application method based on attack behavior analysis, comprising the steps of:
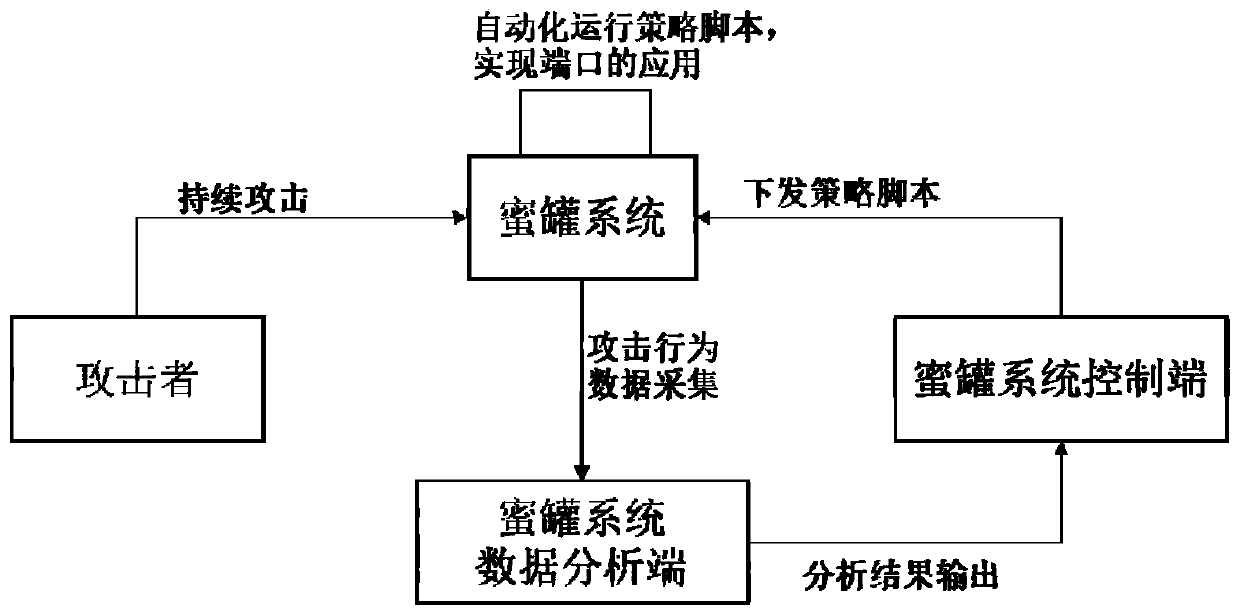
[0035] S01. The honeypot system traps attackers for continuous attacks, and different attackers have different attack purposes and target application ports;
[0036] S02. The honeypot system collects and transmits attacker behavior data to the data analysis terminal of the honeypot system;
[0037] S03. The data analysis end of the honeypot system judges the collected attacker behavior data according to the judgment conditions;
[0038] S04. The data analysis terminal of the honeypot system outputs the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com