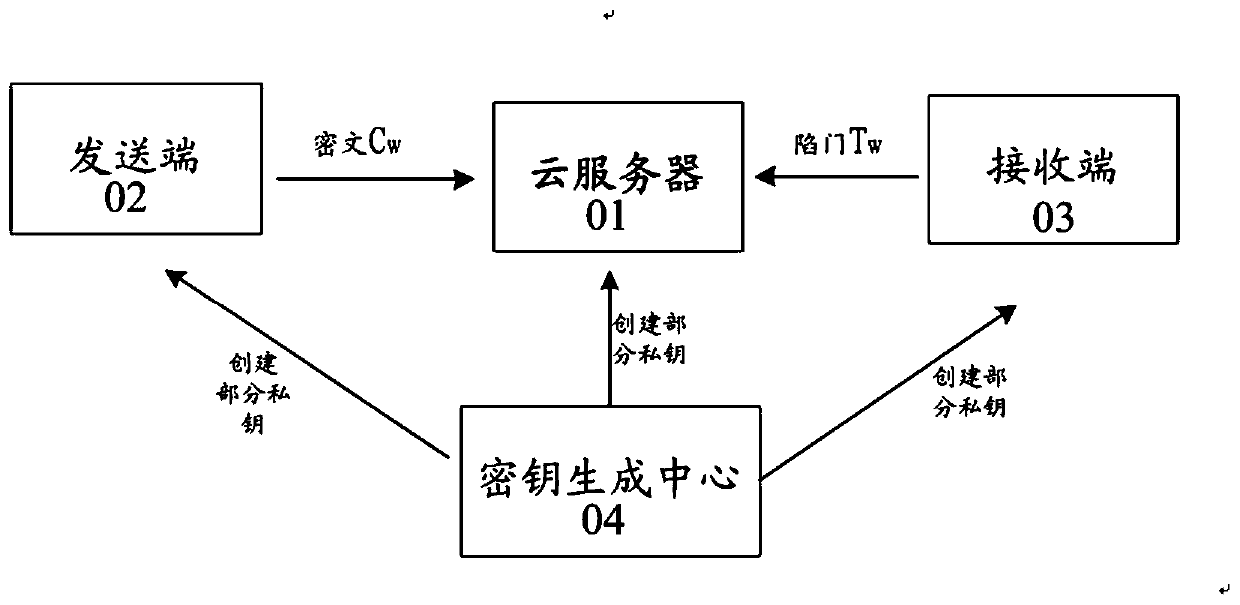
Certificateless public key searchable encryption method and certificateless public key searchable encryption system
An encryption method, certificateless technology, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0107] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
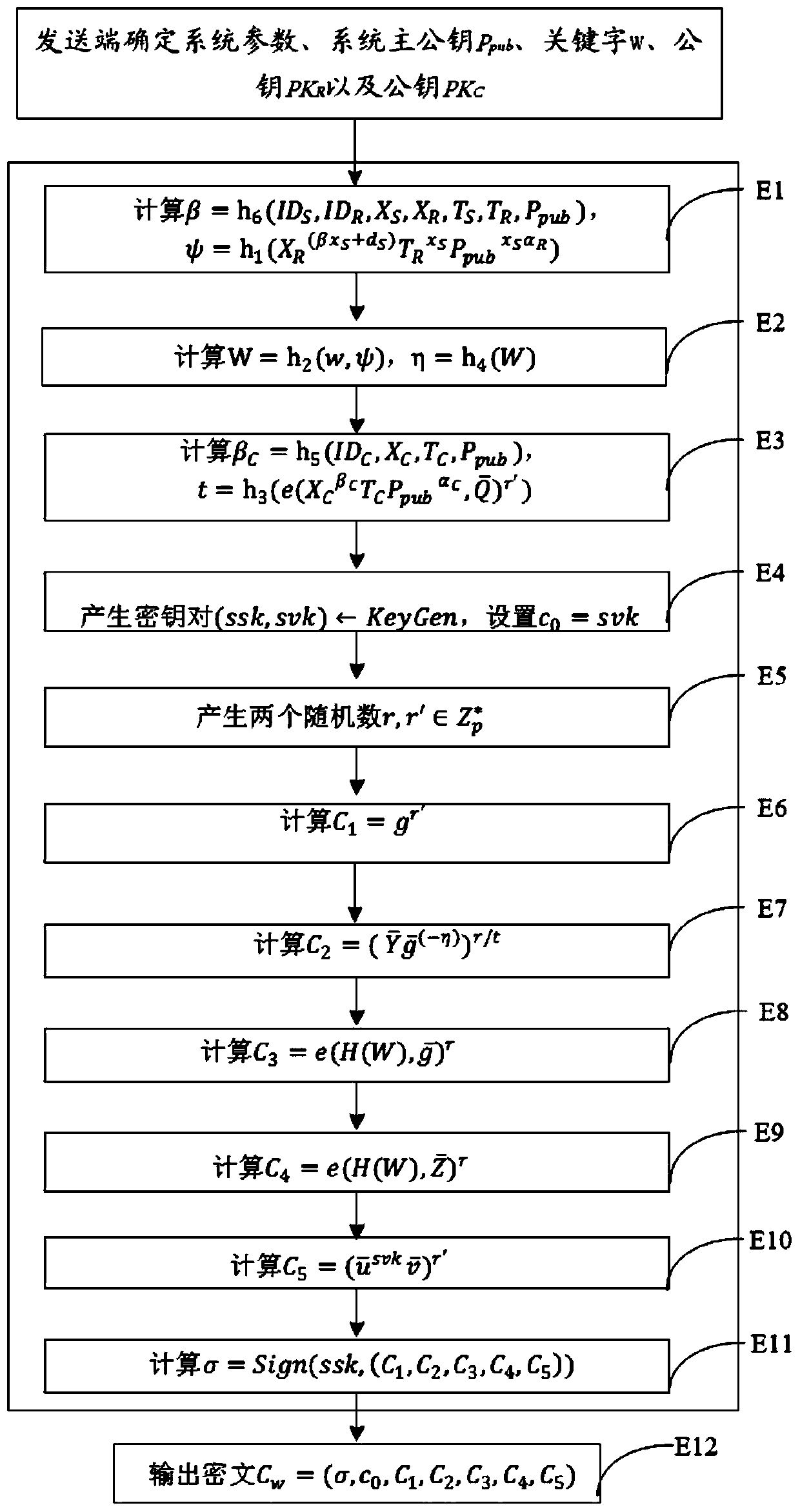
[0108] The symbols of the embodiments of the present invention are described as follows:
[0109] p: a large prime number.
[0110] A collection of integers consisting of 1,2,...,p-1.
[0111] G 1 , G 2 , G T : A cyclic group of order p.
[0112] g, group G 1 and G 2 generator of .
[0113] Group G 2 elements in .
[0114] g u , Group G 1 , G 2 middle element g and to the power of u.
[0115] e: from G 1 ×G 2 to G T The bilinear pairing map of .
[0116] h 0 (·), h 1 (·), h 2 (·), h 3 (·), h 4 (·), h 5 (·), h 6 ( ): One-way hash function.
[0117] s: The system master key secretly held by the key generation center (KGC, key generation center).
[0118] P pub : The system master public key disclosed by KGC, the calculation formula is P pub =g s .
[0119] sig=(KeyGen,Sign,Verify)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com