Anti-quantum computing identity authentication method and system based on secret sharing and quantum communication service station
A quantum communication and identity authentication technology, applied in the field of anti-quantum computing identity authentication, which can solve the problems of complex process, invalid public and private keys of key cards, and high communication cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
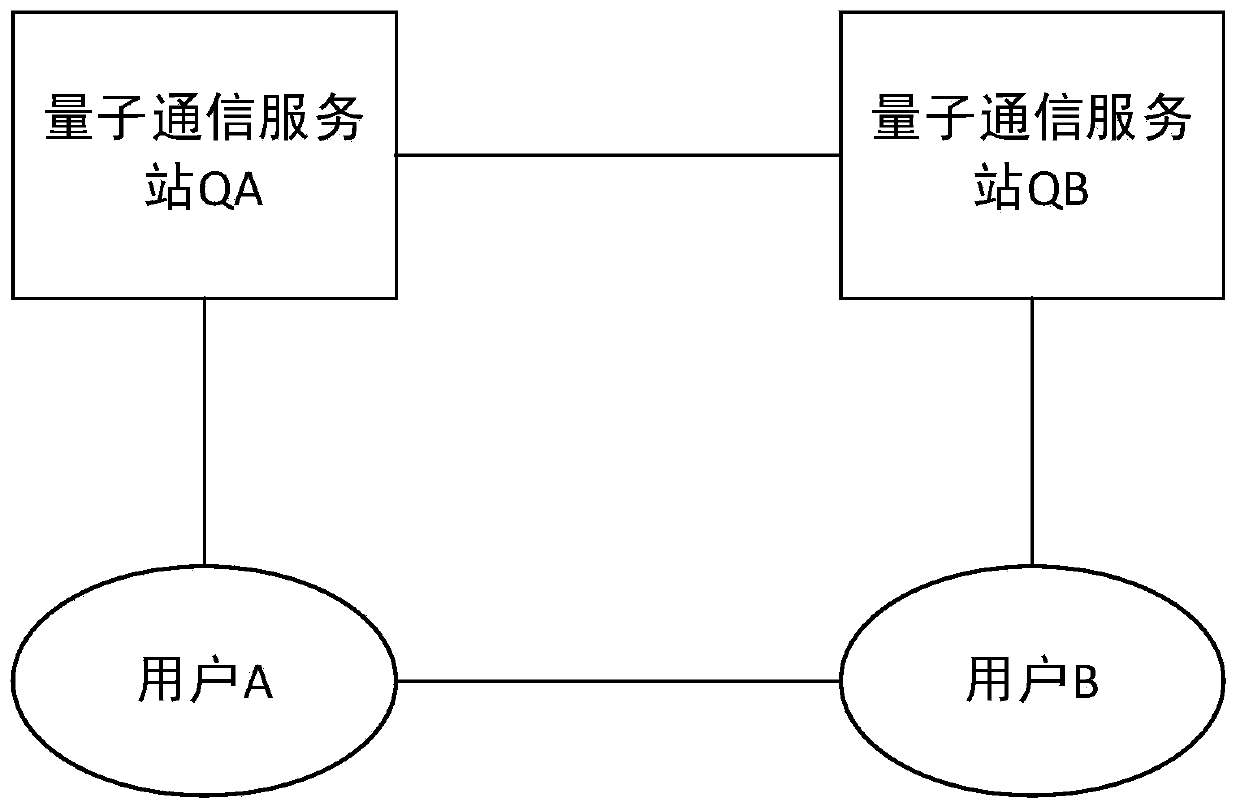
[0075] In this embodiment, it is implemented as identity authentication and key agreement between user A and user B. User A belongs to quantum communication service station QA, and user B belongs to quantum communication service station QB.
[0076] The specific steps of identity authentication are as follows:
[0077] 1. User A initiates an identity authentication request
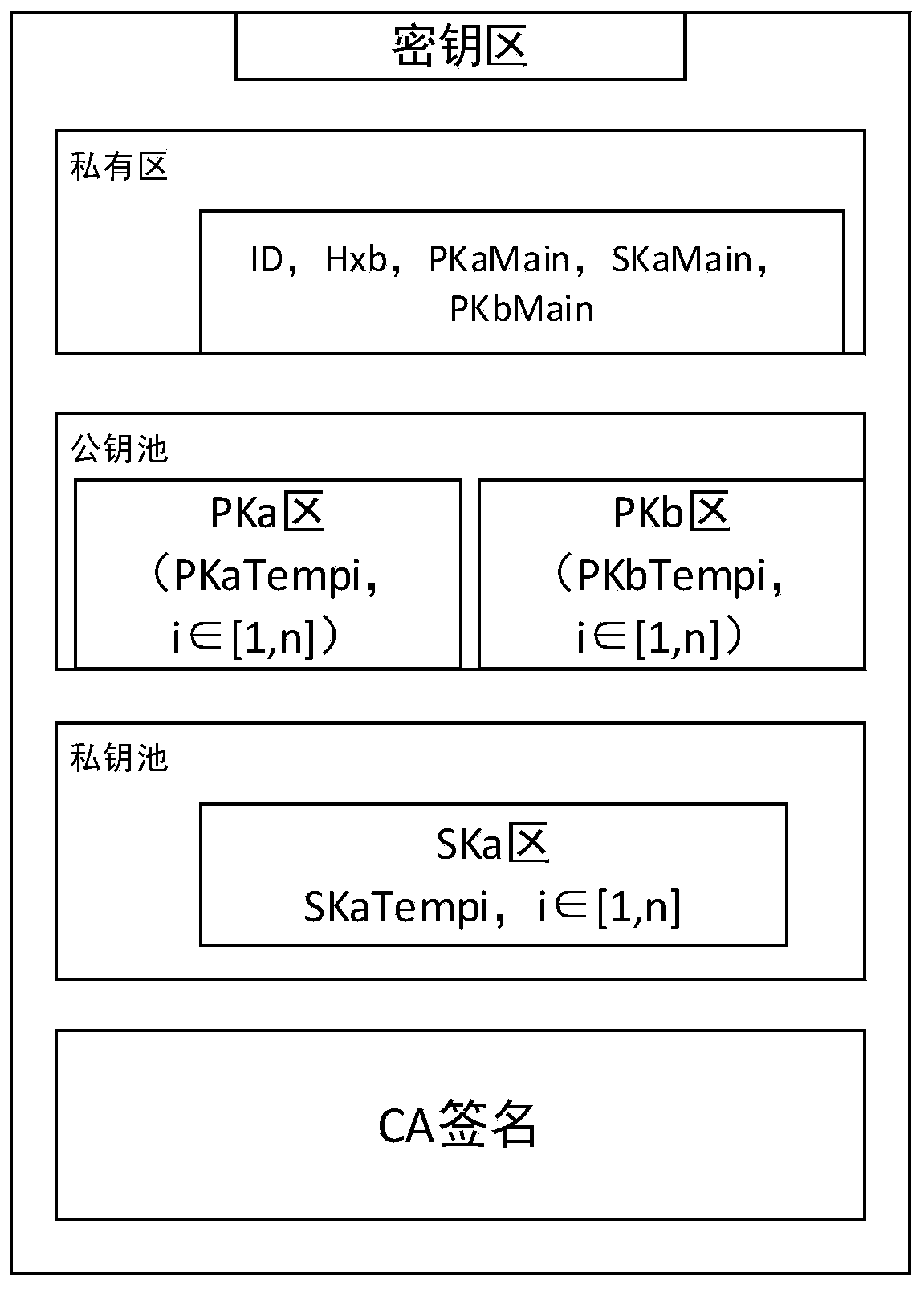
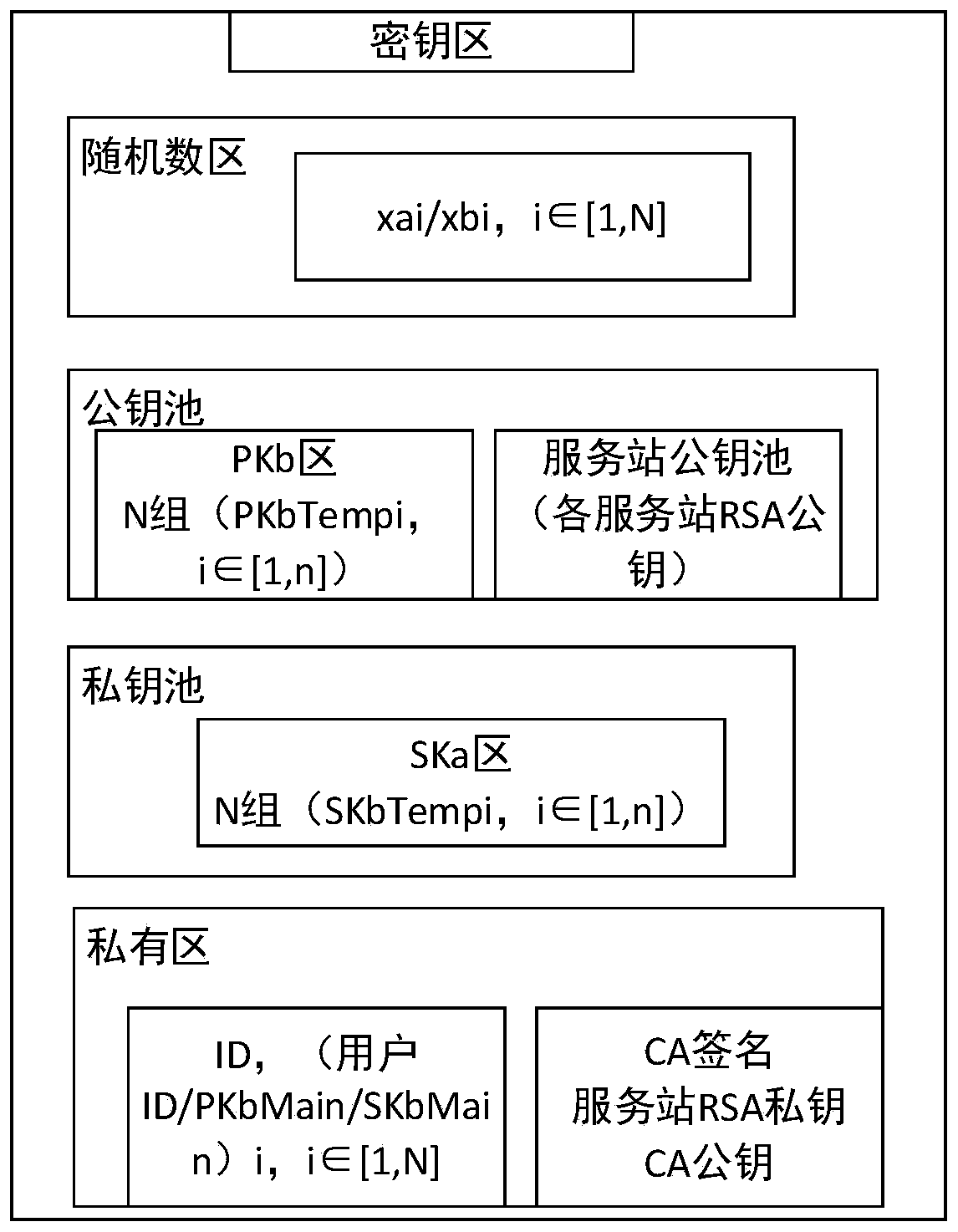
[0078] User A obtains the current timestamp Time, and obtains RK=H(Time) through hash calculation. According to KN key pointer functions {FPm,m∈[1,KN]} and key coefficient calculation functions {FUm,m∈[ 1, KN]} to calculate the position of the secret component {Pm=FPm(RK), m∈[1,KN]}, key coefficient {μm=FUm(RK), m∈[1,KN]}. Take out KN keys from the PKa area, SKa area, and PKb area according to the position to obtain {PKaTempm,m∈[1,KN]}, {SKaTempm,m∈[1,KN]}, {PKbTempm,m∈[1, KN]}, obtained by calculating with the coefficient
[0079] User A generates a true random number DHa, and calculates it with t...
Embodiment 2
[0112] In this embodiment, it is implemented as identity authentication and key agreement between user A and user B. User A and user B both belong to quantum communication service station Q.
[0113] The specific steps of identity authentication are as follows:
[0114] 1. User A initiates an identity authentication request
[0115] User A obtains the current timestamp Time, and obtains RK=H(Time) through hash calculation. According to KN key pointer functions {FPm,m∈[1,KN]} and key coefficient calculation functions {FUm,m∈[ 1, KN]} to calculate the position of the secret component {Pm=FPm(RK), m∈[1,KN]}, key coefficient {μm=FUm(RK), m∈[1,KN]}. Take out KN keys from the PKa area, SKa area, and PKb area according to the position to obtain {PKaTempm,m∈[1,KN]}, {SKaTempm,m∈[1,KN]}, {PKbTempm,m∈[1, KN]}, obtained by calculating with the coefficient
[0116] User A generates a true random number DHa, and calculates it with the base point P to obtain DHA=DHa*P. Encrypt PKaM...
Embodiment 3
[0149] In this embodiment, it is implemented as identity authentication and key agreement between user A and user B. User A belongs to quantum communication service station QA, and user B belongs to quantum communication service station QB.
[0150] The specific steps of identity authentication are as follows:
[0151] Step 1 is the same as embodiment 1, and step 2 is as follows:
[0152] 2. Quantum communication service station QA verifies the request and returns a response
[0153] Quantum communication service station QA receives a request MsgA from user A. According to the IDA in MsgA, it is judged whether it belongs to the quantum communication service station. If it does not belong to the service station, the authentication process of user A fails; otherwise, QA of the quantum communication service station judges whether the time stamp Time is reasonable. If it is unreasonable, the authentication process of user A fails; otherwise, quantum communication service stati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com