Anti-quantum computing vehicle-mounted network identity authentication system and method based on secret sharing and multiple mobile devices
A mobile device and secret sharing technology, applied in the field of identity authentication, can solve the problems of user account rights damage, increase the amount of digital signature calculation, and low user privacy security, and achieve the effect of protecting all rights and interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0073] First, briefly introduce the principle and process of secret sharing.
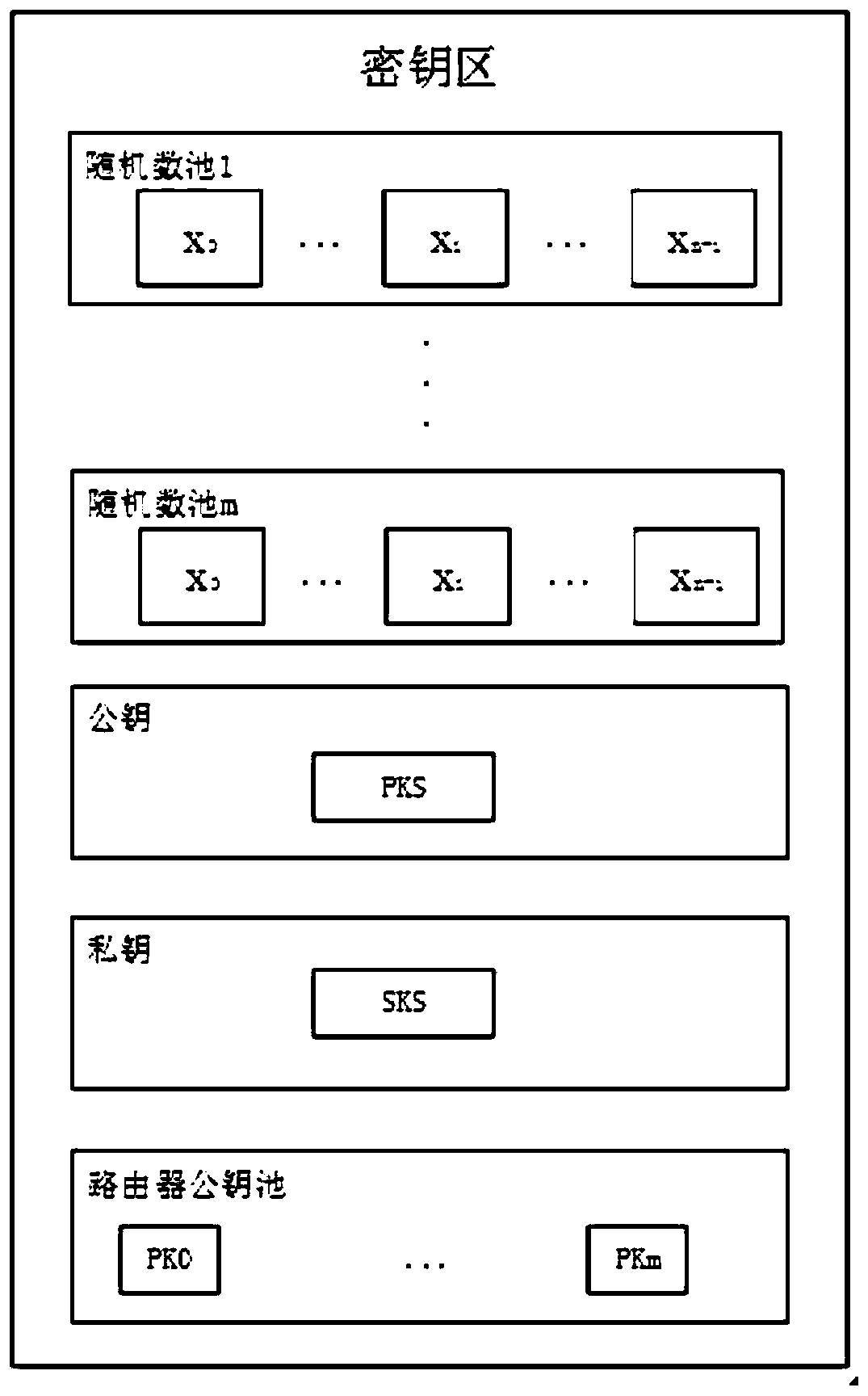
[0074] Randomly select n different non-zero elements X0, X1, X2, ..., Xn-1 from the finite field GF(q) of prime order q, and distribute them to participants Pi (i=0, 1, 2, . . . , n-1). The secret information is SK, select t elements a0, a1, a2, ..., a(t-1) from GF(q), and construct a polynomial Then there is SKi=f(Xi) (0≤i≤n-1).
[0075] Obtaining any t shadow secrets from n participants can restore SK, the specific steps are as follows: According to the formula The t Lagrangian parameters λi can be obtained, so SK can be obtained according to the formula SK=f(0)=∑λi*SKi.
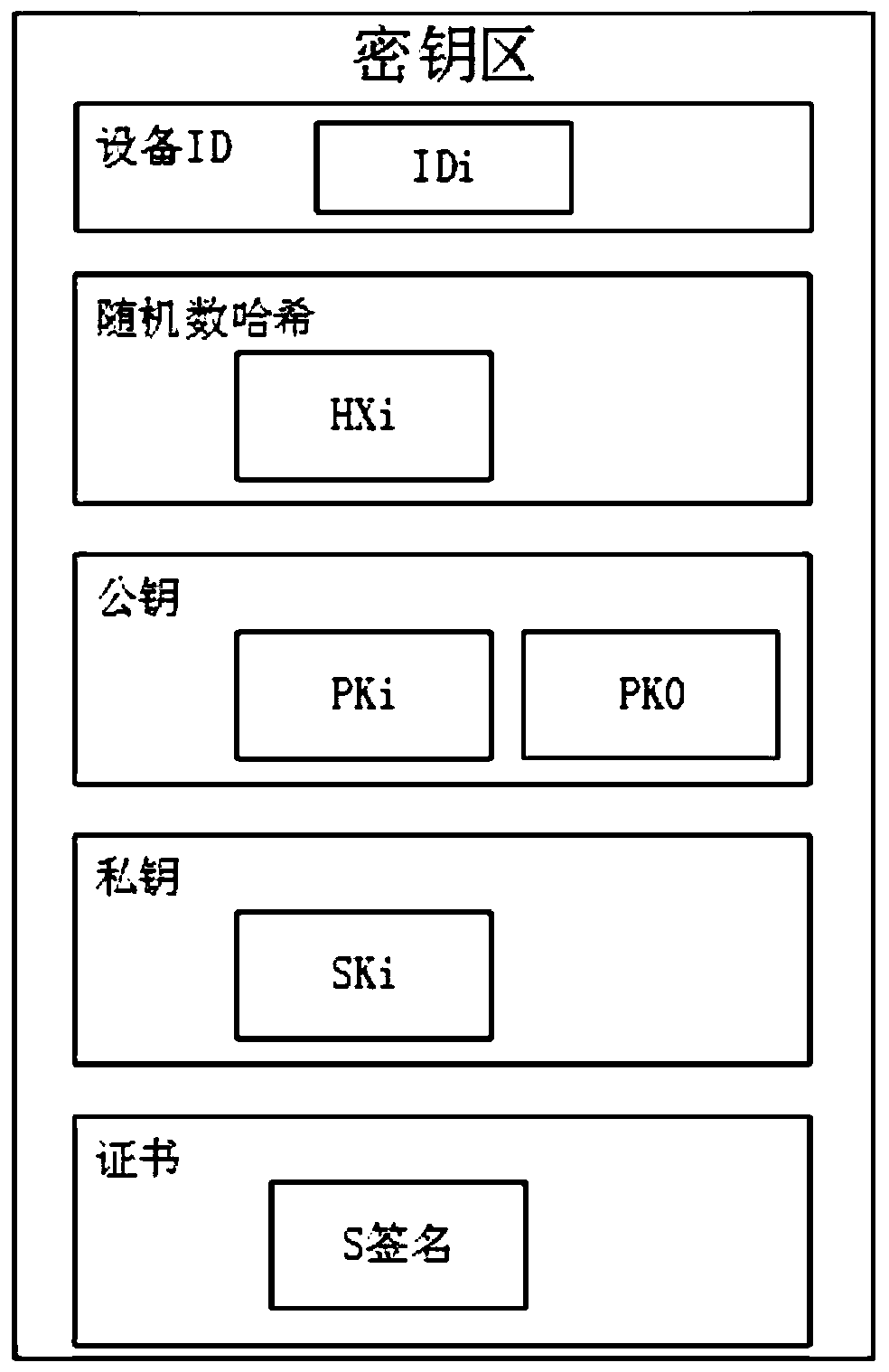
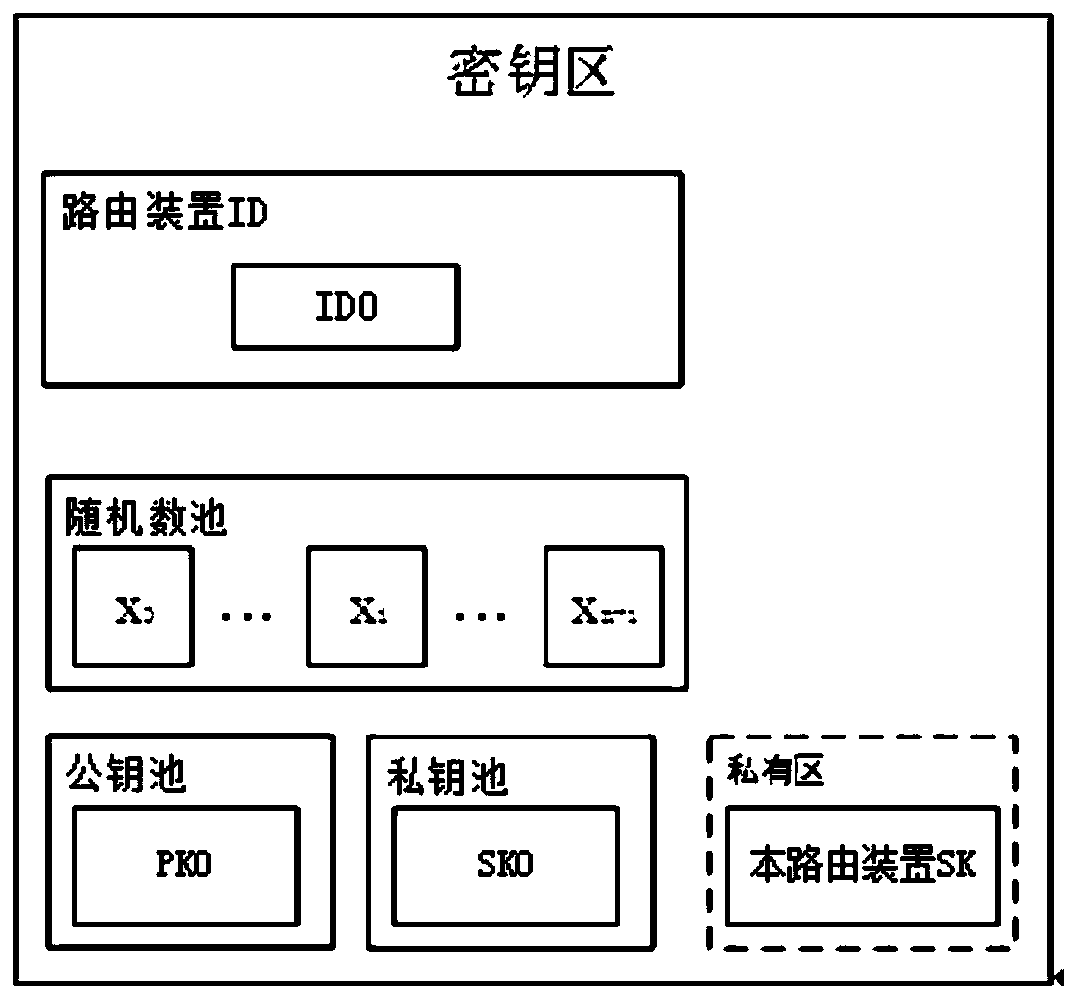
[0076] In the present invention, a user holds multiple mobile devices, and the user can only obtain the authentication of the server through multiple mobile devices and routing devices. User IDs are shared in (t, n) secrets, with each shadow secret being (Xi, IDi). As long as the t group of secrets is collected, the user ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com