HTTP request exception detection method and system
An anomaly detection and anomaly technology, applied in the security field, can solve problems such as high false alarm rate, difficulty in labeling data, and difficulty in covering attack types
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
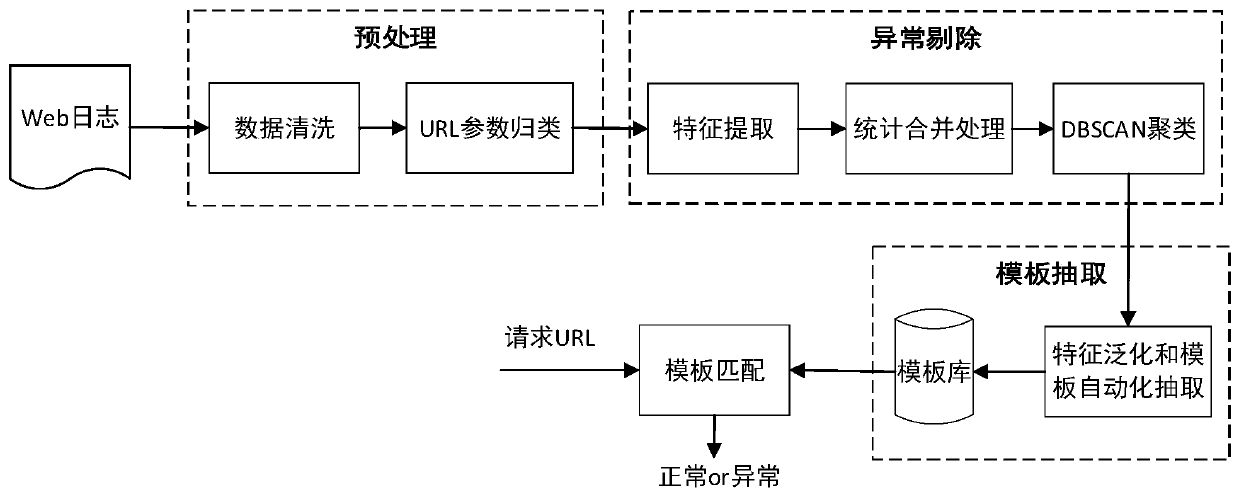
[0062] This embodiment discloses a method for detecting an abnormal HTTP request, comprising the following steps:
[0063] Step 1: Preprocessing the web access logs, including data cleaning and URL parameter classification;
[0064] Step 1.1: Perform data cleaning on web access logs. The purpose of data cleaning is to delete irrelevant records or obviously abnormal records in the log. Since the present invention mainly detects abnormal parameters, it cleans irrelevant data records in the Web access log. Data cleaning specifically includes:
[0065] (1) Filter out the records of response errors in the Web access log. For web logs, it can be judged by the response status code field. The response status code 4XX indicates a client error, and 5XX indicates a server error. Therefore, records with a status code exceeding 400 (including 400) in the log are filtered out.
[0066] (2) Filter out the records in the web access log that the request method is not GET or POST. User acc...
Embodiment 2
[0100] like figure 1 As shown, on the basis of Embodiment 1, this embodiment further provides a method that can be used to detect abnormalities in real-time or newly added HTTP requests to be tested in the Web access log, and the specific steps are:
[0101] First, based on the abnormal point identification results in step 2, the abnormal points in all parameter values under each URL parameter category are removed;
[0102] Then, perform the following steps:
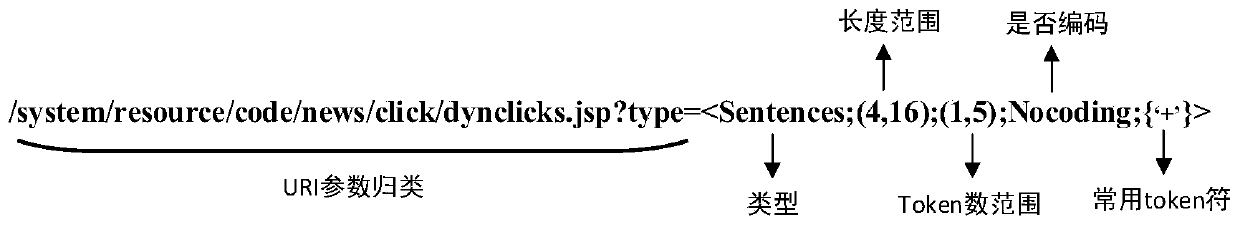
[0103] Step 3: For each URL parameter category, perform feature generalization and automatic generation (extraction) of parameter value templates (normal parameter value templates) based on the parameter values after removing outliers, and store them in the parameter value template library. figure 2 is a parameter value template format diagram according to an embodiment of the present invention.
[0104] First, define parameter value templates from five characteristics, such as figure 2 shown.
[0105] The para...
Embodiment 3
[0124] The present embodiment provides a HTTP request abnormal detection system, including the following modules:
[0125] The preprocessing module is used to preprocess the Web access log, including data cleaning and URL parameter classification; where the URL parameter classification refers to the URL of each HTTP request in the Web access log, and the access path (request The file path) is combined with each parameter, and the combination of each access path and parameter name formed is respectively used as a URL parameter category;
[0126] The abnormal point identification module is used for clustering and identifying abnormal points for all parameter values under each URL parameter category;
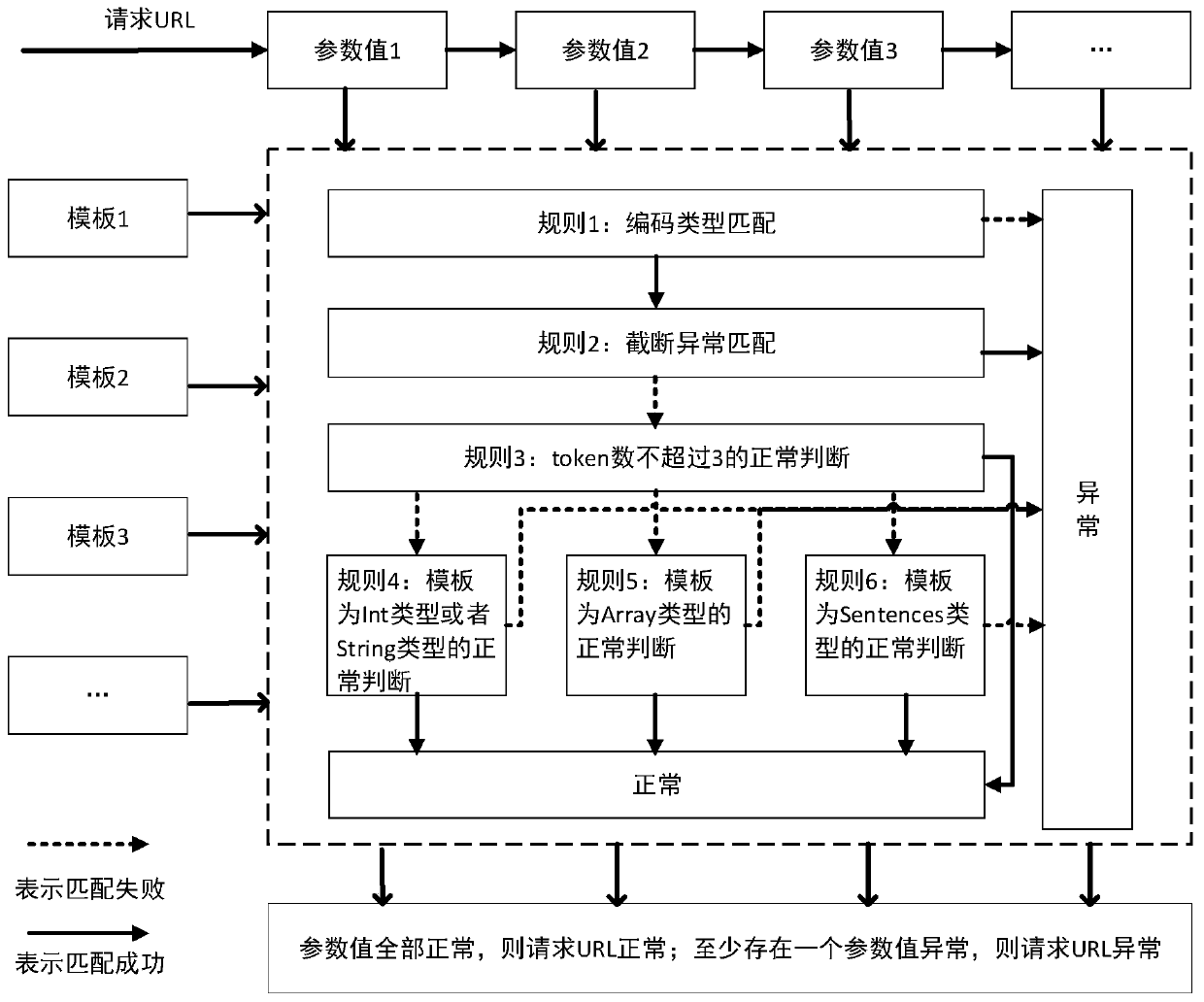
[0127] The abnormality detection module is used for abnormality detection of the HTTP request to be tested; for the HTTP request to be tested in the web access log, if there is a parameter value in the URL that is an abnormal point, it is determined that the HTTP request to be te...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com