Efficient method and device for judging reuse vulnerabilities after software program release
A technology of software program and determination method, which is applied in the field of network security to achieve the effect of improving determination efficiency, improving detection and protection capabilities, and improving performance problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
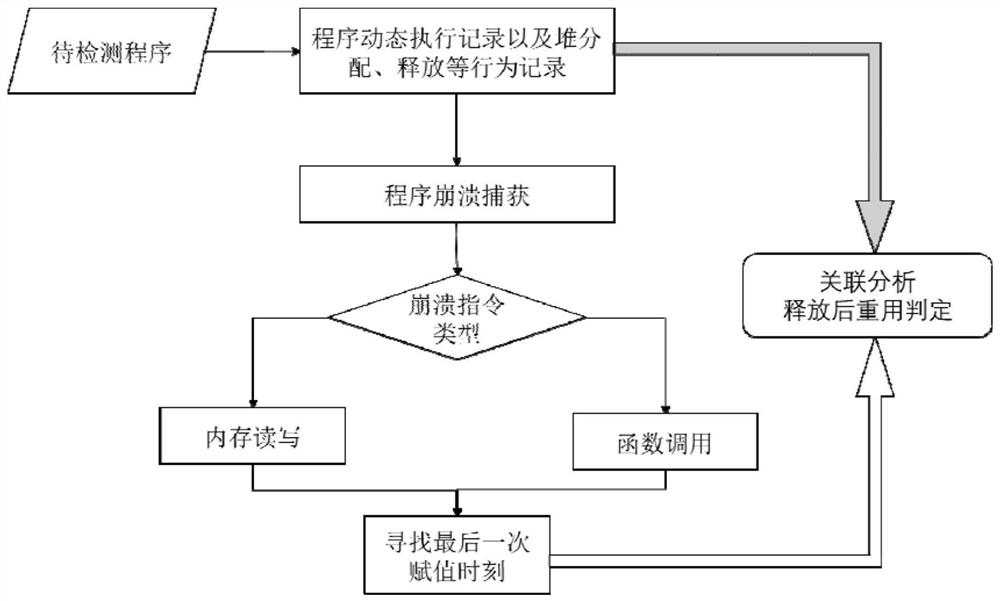
[0031] The technical scheme of the present invention is described in detail below in conjunction with accompanying drawing:
[0032] This embodiment provides an efficient binary program reuse determination method, including the following steps:
[0033] 1. Monitor every instruction in the process of program crash and the instruction at the time of crash
[0034] Through the program dynamic monitoring technology, the instruction execution record set InsnTrace={(TraecID, Instruction, OperandAddress, OperandValue, ThreadID)} and the program crash information CrashInfo=(TraecID, Instruction, OperandAddress, OperandValue, ThreadID) are obtained. Among them, TraceID indicates the record ID corresponding to the instruction, Instruction indicates the specific assembly form of the instruction, OperandAddress indicates the memory address of the instruction operand, if it is a register, it needs to be mapped to a specific memory, OperandValue indicates the value of the instruction operan...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com