Internet of Things security architecture and information security interaction method thereof
An Internet of Things and security technology, applied in the field of network security, can solve the problems of security constraints, the inability to build a unified security architecture for the Internet of Things, and affect the security of the Internet of Things, and achieve the effect of enhancing security, improving security performance, and avoiding network crashes.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The following descriptions of various embodiments refer to the accompanying drawings to illustrate specific embodiments in which the present invention can be implemented.
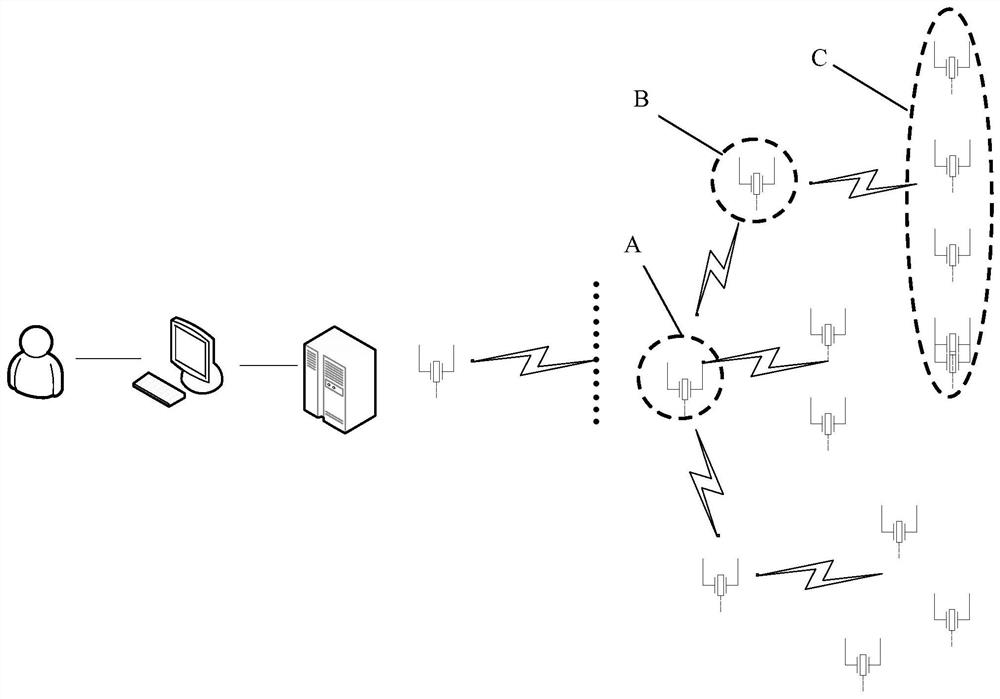
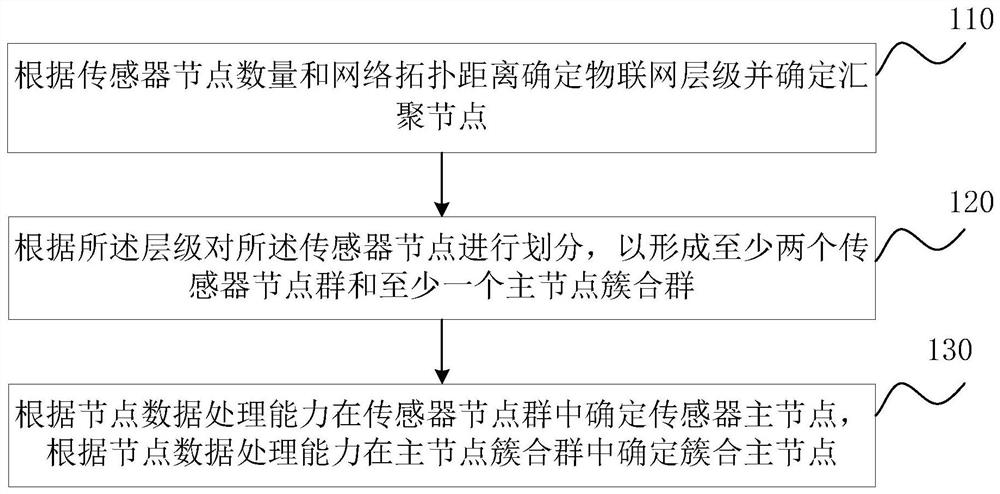
[0036] Please refer to figure 1 As shown, Embodiment 1 of the present invention provides an Internet of Things security architecture, including:
[0037] A sensor node group, the sensor node group includes a sensor master node (each sensor node group includes a master node, there are multiple sensor node groups) and several sensor member nodes, between the sensor master node and the sensor member nodes Communication by way of identity verification; master node clusters, including: a cluster master node B and several sensor master nodes A, the cluster master node B and sensor master nodes A communicate through identity verification; the aggregation node A , the aggregation node A is used to aggregate the information of all the clustering master nodes B; the sensor node group and the master node clust...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com