Novel network attack processing method and device
A network attack and processing method technology, which is applied in the field of DDOS and CC attack protection products, new network attack processing methods and devices, can solve problems such as rough tactics, accidental damage, and inaccurate identification of CC attack defense, so as to achieve a good Internet experience and improve The effect of stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
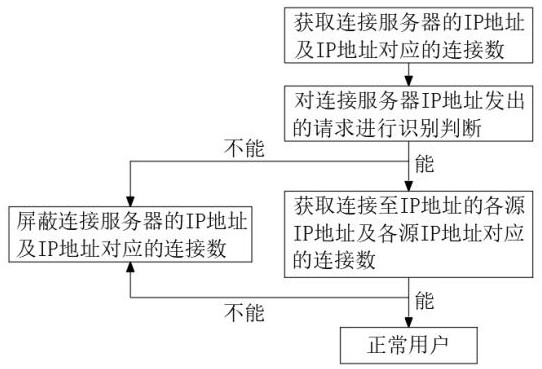
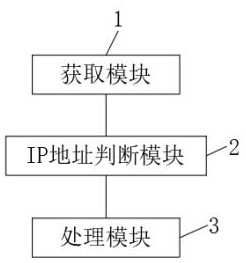
[0022] Embodiment 2: the acquisition module 1 first acquires the IP address of the connection server and the number of connections corresponding to the IP address, and then the IP address judgment module 2 adopts JS identification technology to identify the request sent by the acquisition module 1 to obtain the IP address, and judge the request verification If yes, the JS code cannot be interpreted, and it is judged as an attack. If not, it is a normal user. At the same time, the IP address judging module 2 divides the IP address into a whitelist and a blacklist, and the processing module 3 directly divides the blacklist The IP access is denied, and the URL that does not need to be filtered is defined in the URL whitelist, and the request that cannot explain the JS code is blocked and the response is rejected.
Embodiment 3
[0023] Embodiment 3: the acquisition module 1 can be matched multiple times, and obtains the IP address of the connection server and the corresponding connection number of the IP address, and then the IP address judging module 2 is identified according to the request that the acquisition module 1 obtains the IP address. With a fixed attack signature, the post-processing module 3 directly blocks the request with the attack signature by writing the corresponding strategy through the Shell script. At the same time, the same second, the same IP, and different UA requests can be blocked through the Shell script, and the same proxy IP, different requests to access the real IP are blocked.
[0024] A new type of network attack processing device, the processing device includes an acquisition module 1, an IP address judgment module 2 and a processing module 3, the acquisition module 1 is mainly to obtain the IP address of the connection server and the number of connections corresponding...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com