FP-tree optimized XSS attack automatic detection method
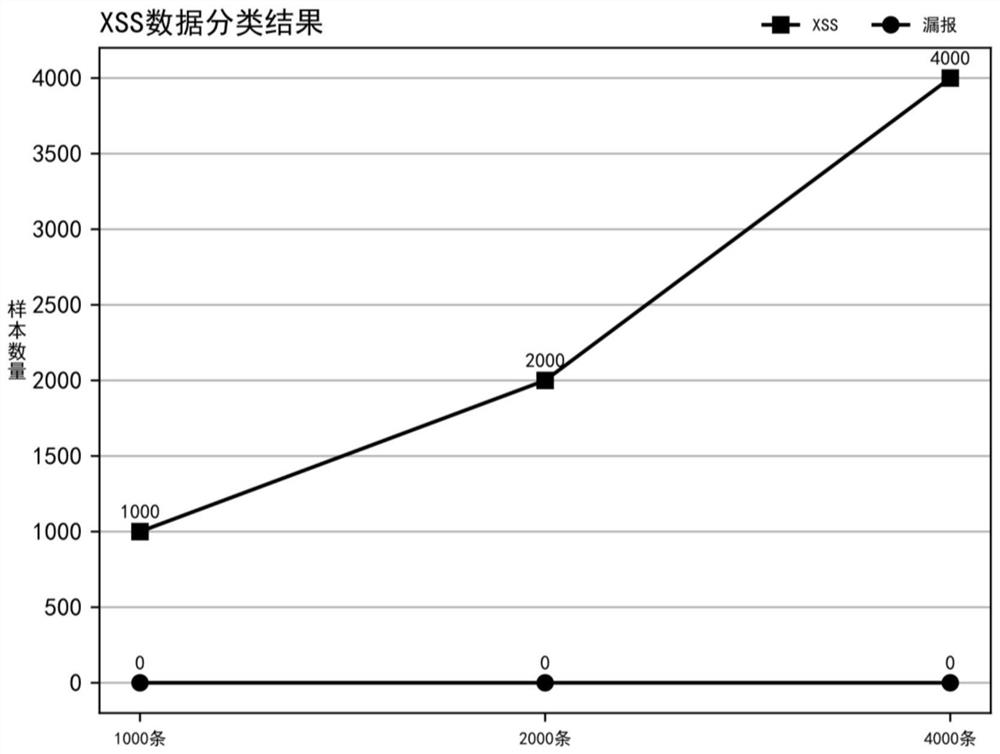
An automatic detection and algorithm technology, applied in the field of network security, can solve problems such as being easily bypassed by hackers and low accuracy of model recognition, so as to reduce the false negative rate, improve the recognition rate, and reduce the effect of manual intervention
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
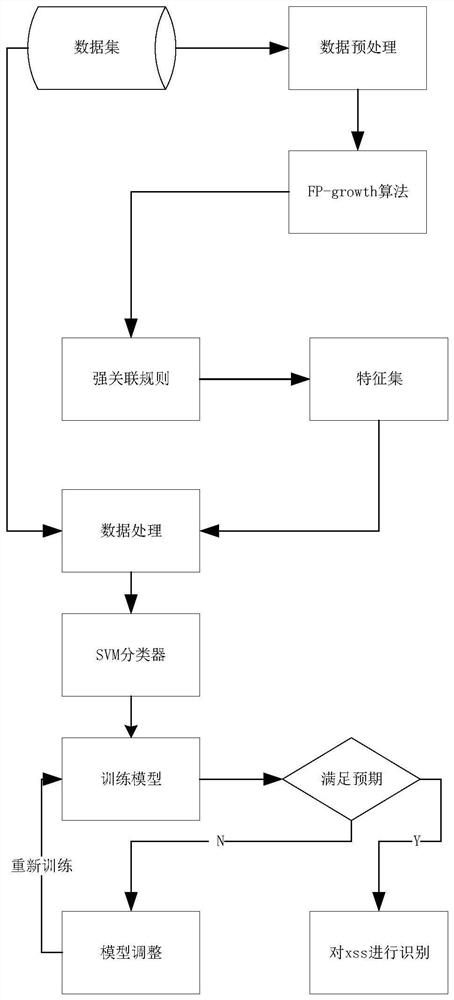
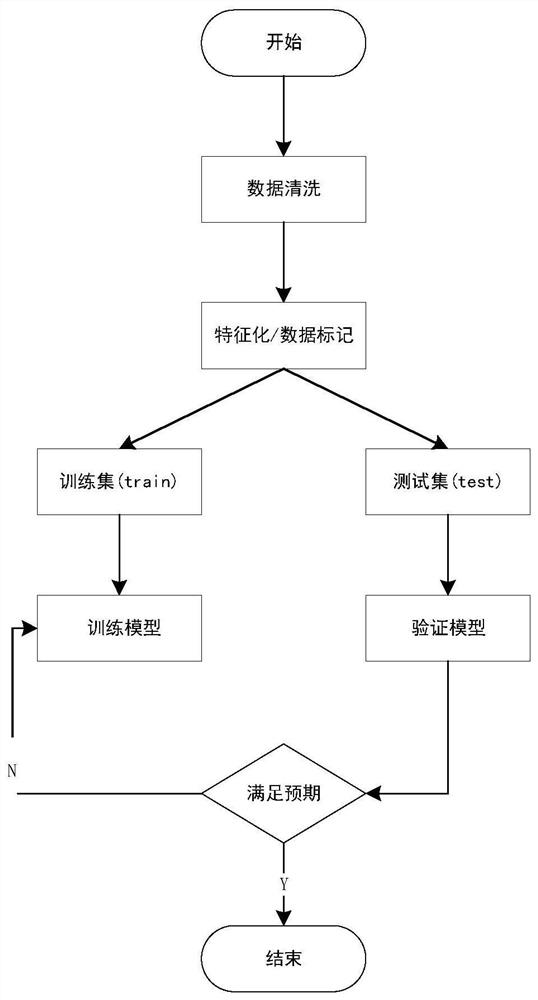
[0040] according to figure 1 Shown, a kind of FP-tree optimized XSS attack automatic detection method of the present invention, its step comprises:
[0041] Step 1: Use the FP-growth algorithm to extract XSS-related features:
[0042] Step 1.1: read the data set for the first time, generate an item header table, read the data set for the second time, and process the data set, specifically: read the data set for the first time, and generate the items that appear in the data set Count the frequencies to get the final frequent item set; remove the frequent item sets that do not meet the minimum support in the frequent item set, and sort the obtained frequent item sets in descending order of support to obtain the item header table; the secon...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com