Secure multi-party computing protocol algorithm fusing Pedeersen commitment and Schnorr protocol
A technology for secure multi-party computation and protocol, applied in the field of cryptography, it can solve the problems of single signed message by transaction participants, high computational overhead for multi-party transactions, and attacks, so as to avoid computational overhead and reduce signature verification time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
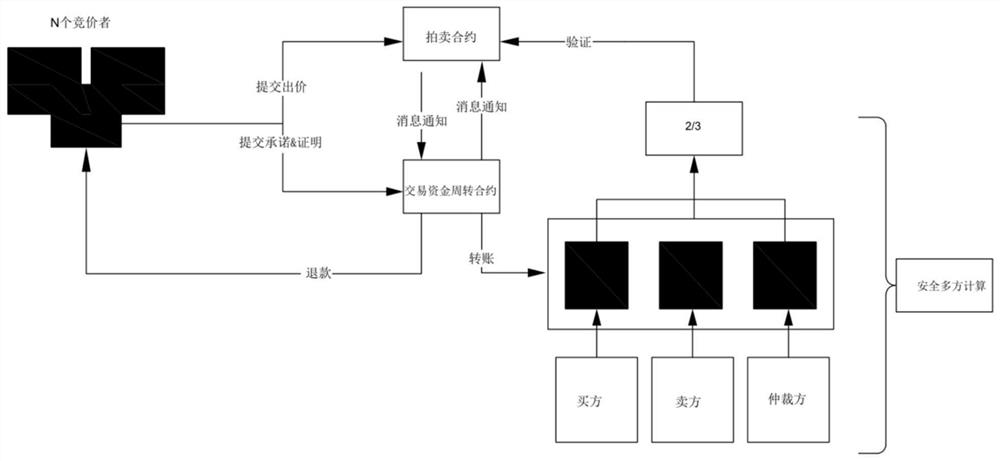
[0029] see figure 1 , a secure multi-party computing protocol algorithm that integrates the Pedersen commitment and the Schnorr protocol. On the basis of the existing Schnorr signature, it is improved by integrating the Pedersen commitment, so that the submitted signature message is different and not public, and it can also be effective. Privacy protection, and build a sealed auction scene, including the following steps:
[0030] S1. Each anonymous bidder bids for the products on the shelves, and submits his transaction margin, quotation ciphertext, quotation commitment and proof of quotation commitment to the relevant contract;
[0031] S2. After the bidding ends, each bidder submits the ciphertext and the real bid to reveal the price within the specified time. After the input is correct, the contract will verify the correctness of the commitment certificate and the quotation;
[0032] S3. After the price reveal is over, the contract will only announce the transaction price ...
Embodiment 2
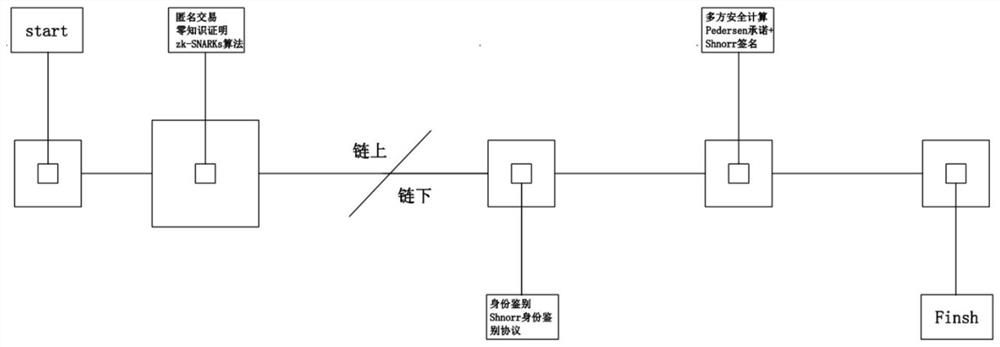
[0054] see figure 2 , a secure multi-party computing protocol algorithm that integrates Pedersen commitment and Schnorr protocol. In the sealed auction scenario, it is necessary to use privacy technology, that is, use zero-knowledge proof zk-SNARKs algorithm on the chain to conduct anonymous transactions. Next, use the identity authentication protocol to determine the identity of each transaction arbitration participant, and then use the newly proposed Pedersen commitment combined with the Schnorr signature scheme to perform secure multi-party computation.
Embodiment 3
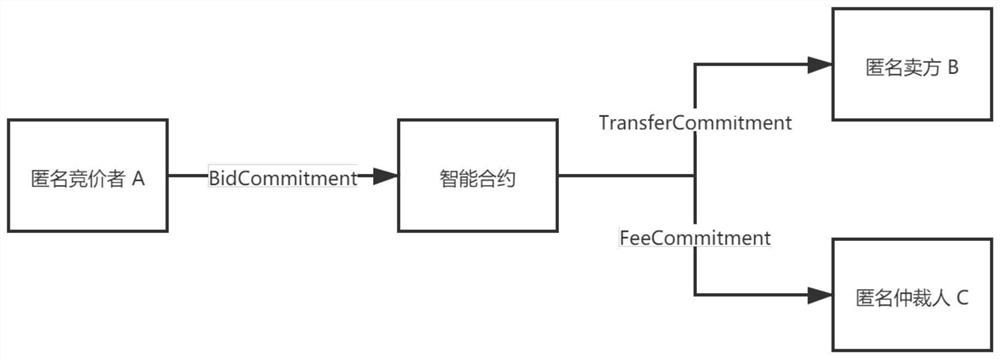
[0056] see image 3 , a secure multi-party computing protocol algorithm that integrates Pedersen Commitment and Schnorr Protocol, requires transfer of assets stored by bid winner A to seller B after a transaction conflict occurs. A's bidding commitment BidCommitment is split into two new asset commitments through smart contracts, one is the asset commitment TransferCommitment to the seller B, and the other is the arbitration service fee FeeCommitment transferred to the arbitrator C. At this time, other people will only know that the funds of an auction are transferred out of the contract, but they do not know who the specific sender and receiver are, that is, the transfer of funds between two anonymous addresses is completed.
[0057] The beneficial effects of the present invention are: a secure multi-party computing protocol algorithm integrating Pedersen commitment and Schnorr protocol, by using the characteristic of Pedersen additive homomorphism, under the condition of not...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com