Log reading method based on log analysis synchronization and synchronization system
A log and readable technology, applied in the direction of file system, file system function, structured data retrieval, etc., can solve problems such as data synchronization errors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
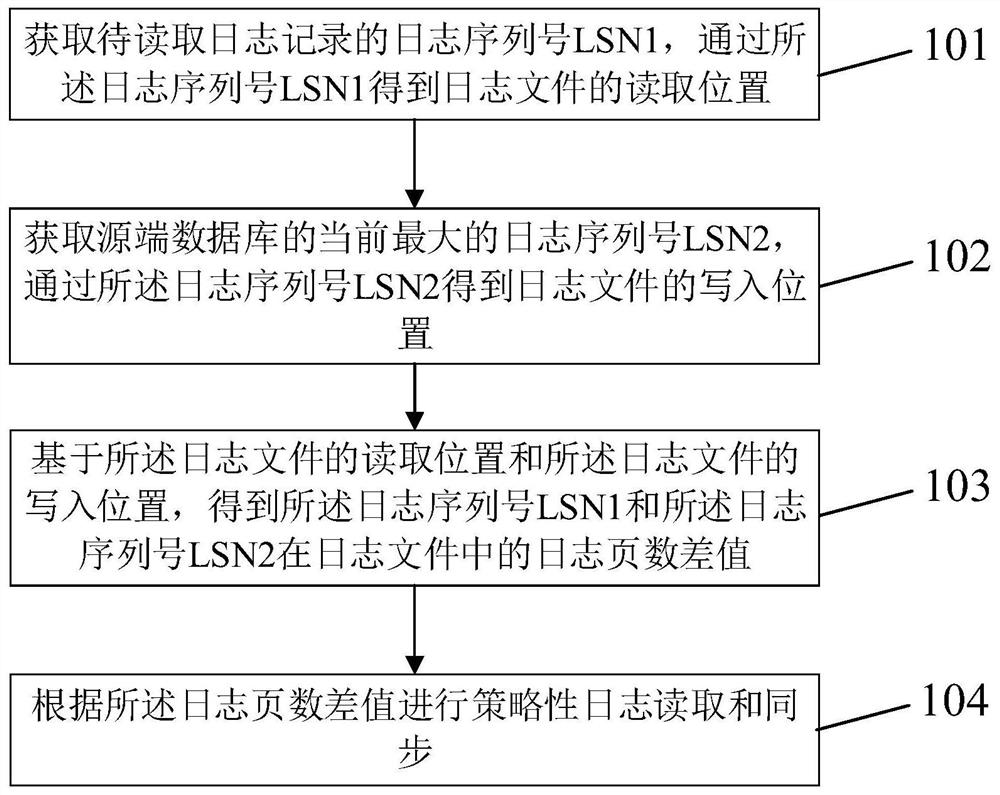
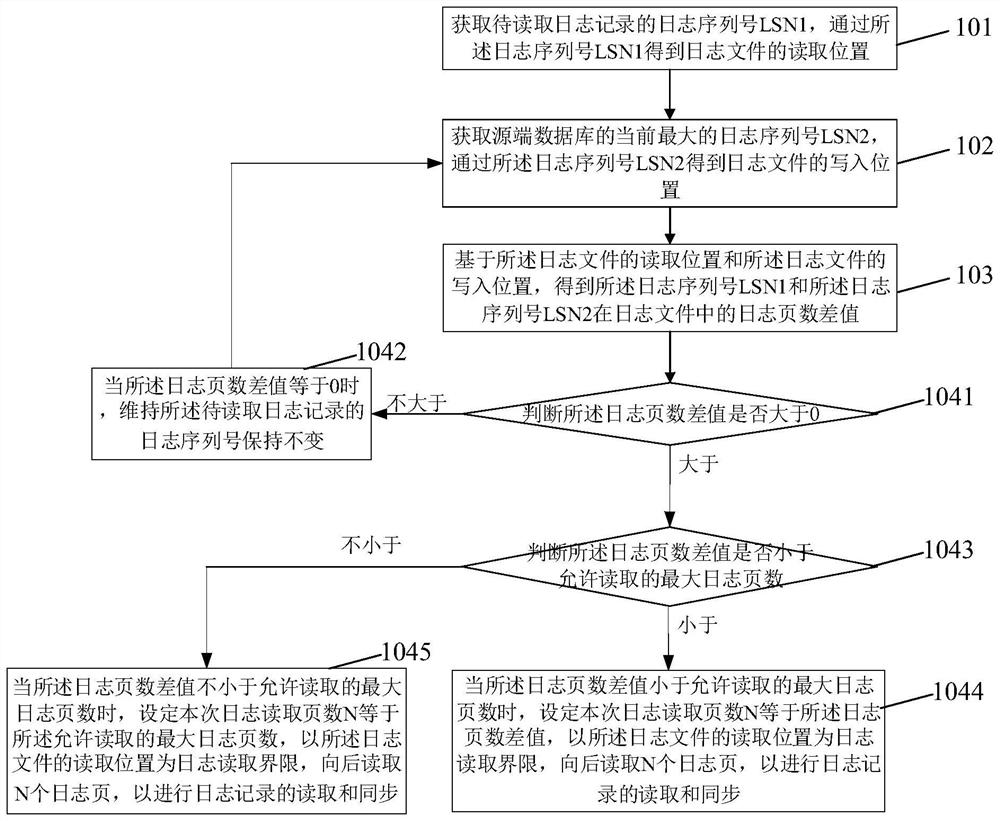
[0052] At present, although the data lock technology can only allow one process to access a certain file, the data lock is applicable to the same type of database or the database of the same manufacturer. The write operations on one side and the read operations on the destination database side originate from databases of two different manufacturers, so the above data lock cannot be used, and the method in this embodiment is applicable to databases of different sources or types.
[0053] In order to avoid read-write conflicts between the data synchronization process and the database process, it is necessary to prevent these two processes from simultaneously accessing data at the same offset in the same file at the same time. In order to achieve this goal, it is necessary for the data synchronization process to mutually exclude it and the database by judging whether the current log to be read and the log to be written to the database are in the same position of the same log file ...
Embodiment 2
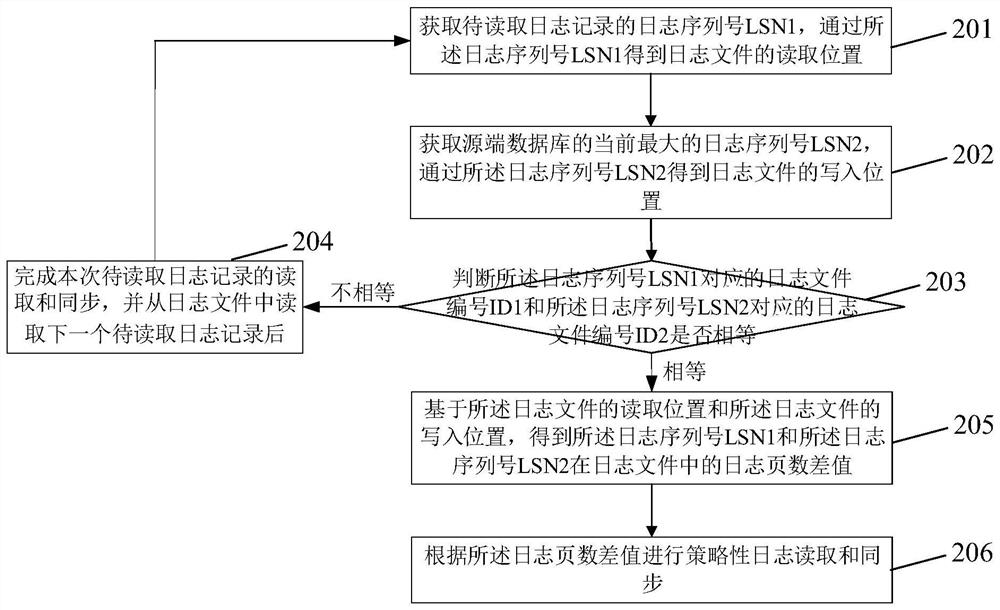
[0088] In combination with embodiment 1, this embodiment provides another log reading method, combining figure 2 , the log reading method includes the following steps:
[0089] Step 201: Obtain the log sequence number LSN1 of the log record to be read, and obtain the reading position of the log file through the log sequence number LSN1.
[0090] Step 202: Obtain the current largest log sequence number LSN2 of the source database, and obtain the write location of the log file through the log sequence number LSN2.
[0091] Wherein, the specific implementation process of step 201 and step 202 is the same as the foregoing embodiment 1, see embodiment 1 for details, and will not be repeated here.
[0092] Step 203: Determine whether the log file number ID1 corresponding to the log sequence number LSN1 is equal to the log file number ID2 corresponding to the log sequence number LSN2.
[0093] Although in actual application scenarios, in order to reduce the synchronization delay, ...
Embodiment 3
[0101] Based on the foregoing embodiment 1, here, taking DM6 as an example, the implementation process of the foregoing embodiment 1 is illustrated:
[0102] Build a data synchronization system on database A and database B, and set the maximum number of pages allowed to be read by the data synchronization process to Z pages; set the time interval for polling the database log LSN to 1 second, and synchronize the source data The system creates an auxiliary table T (C INT) on database A to push logs.
[0103] The database interaction process of the source log synchronization system is as follows:
[0104] (1) The database interaction thread obtains the largest log LSN of the current database from the source database every 1 second, and the obtained SQL is select get_last_lsn() from dual; the log sequence number LSN2 is obtained.
[0105] (2) The database interaction thread then executes the statement: BEGIN UPDATE T SET C=1; COMMIT; END; to ensure that the log operations whose l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com