SM9 key generation method, device and system and readable storage medium
A key generation and private key technology, applied in encryption devices with shift registers/memory, transmission systems, digital transmission systems, etc., can solve problems such as high security risks and private key leakage, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 3
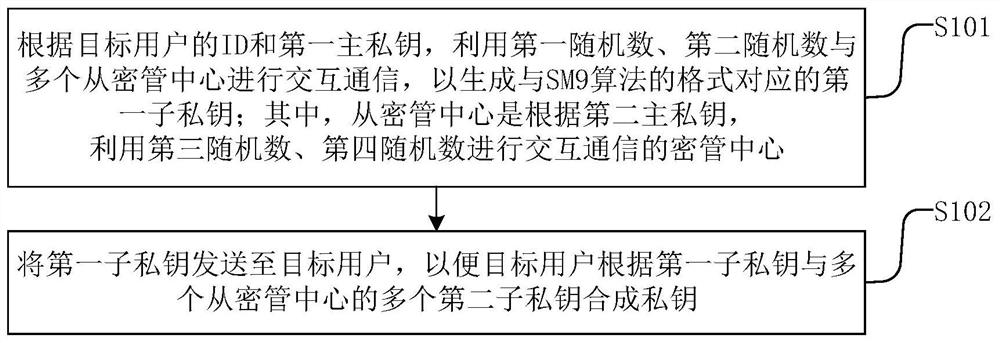
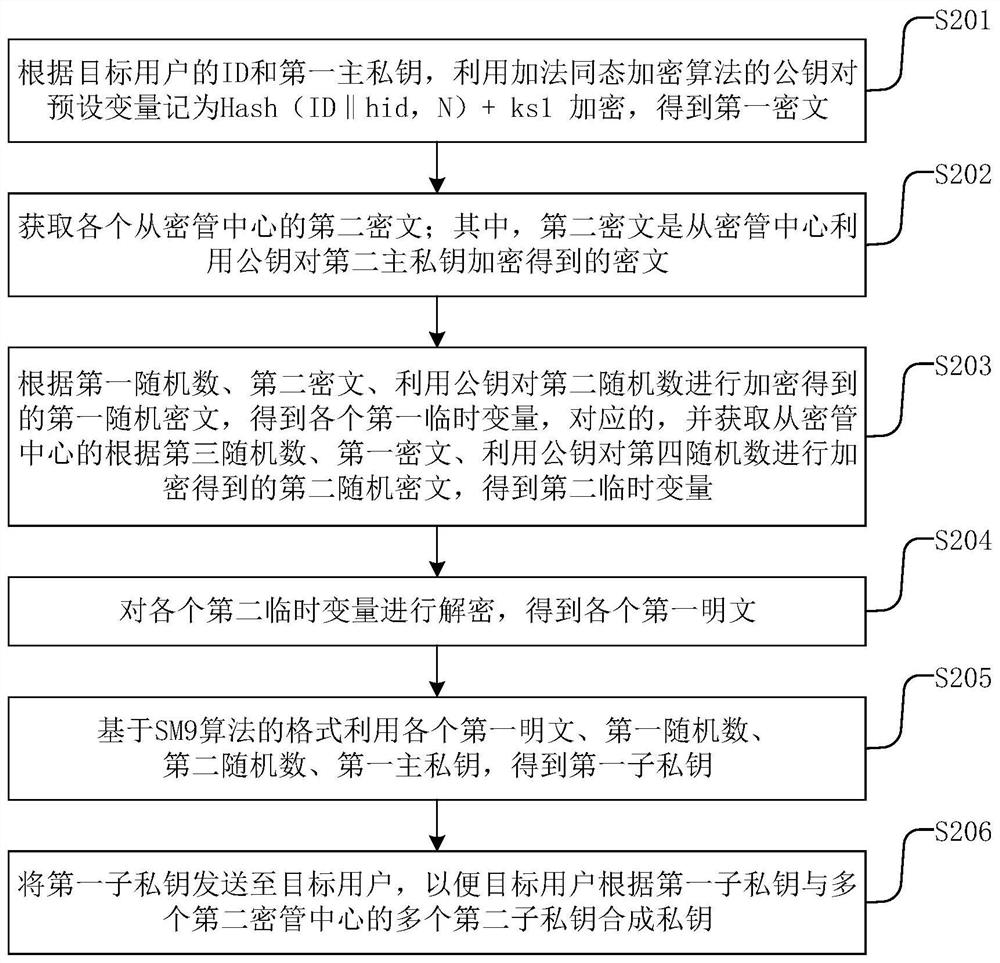
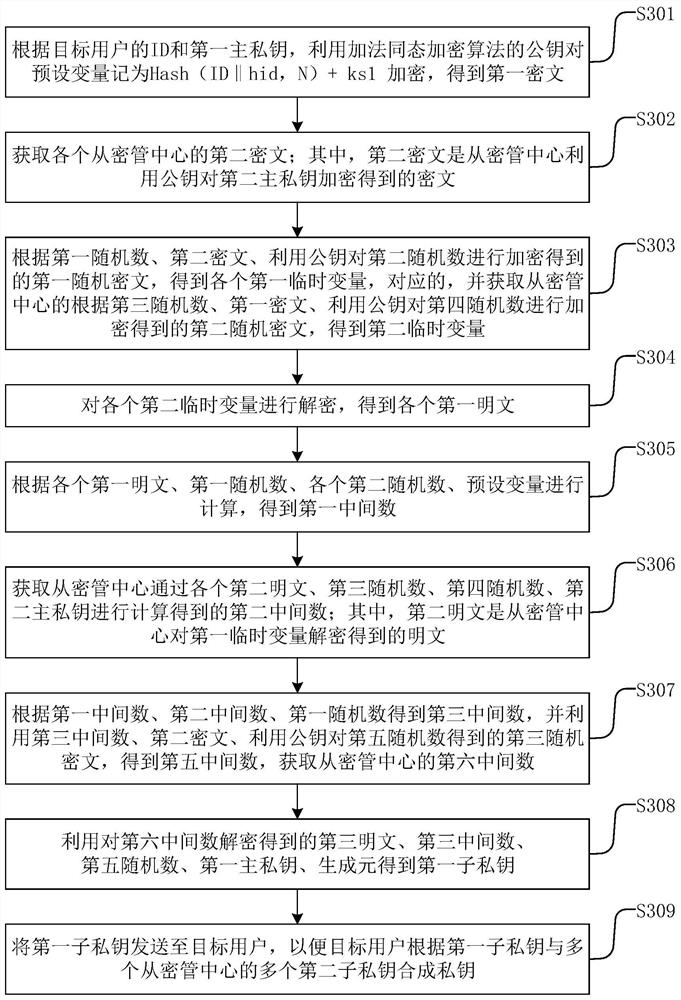
[0110] Based on Embodiment 3, this disclosure provides a specific SM9 key generation method. When the slave key management center is a key management center, please refer to Figure 4 , Figure 4 A schematic diagram of key generation provided by an embodiment of the present disclosure, specifically including:
[0111] E() is the public key algorithm of the additive homomorphic encryption algorithm, P1 is the generator, [KS 1 ]P 1 +[KS 2 ]P 1 Denote the private key as ds, F N is a finite field containing N elements, and N is a cyclic group G 1 , G 2 , G T order, hid represents the identifier of the signature private key generation function, P 1 is the group G 1 generator; user A is the target user.
[0112] KGC 1 Main control center, α 1 is the first random number, β 1 is the second random number, ks 1 is the first sub-private key, Hash(ID||hid,N)+ks 1 As a preset variable, E(Hash(ID||hid,N)+ks 1 ) is the first ciphertext, E(β 1 ) is the first random ciphertext...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com