Key management system
A key management system and key management technology, which is applied in the field of data encryption, can solve problems such as key theft, no key classification, user privacy data leakage, etc., to achieve stable and reliable equipment, ensure cryptographic operations, and secure storage of keys Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
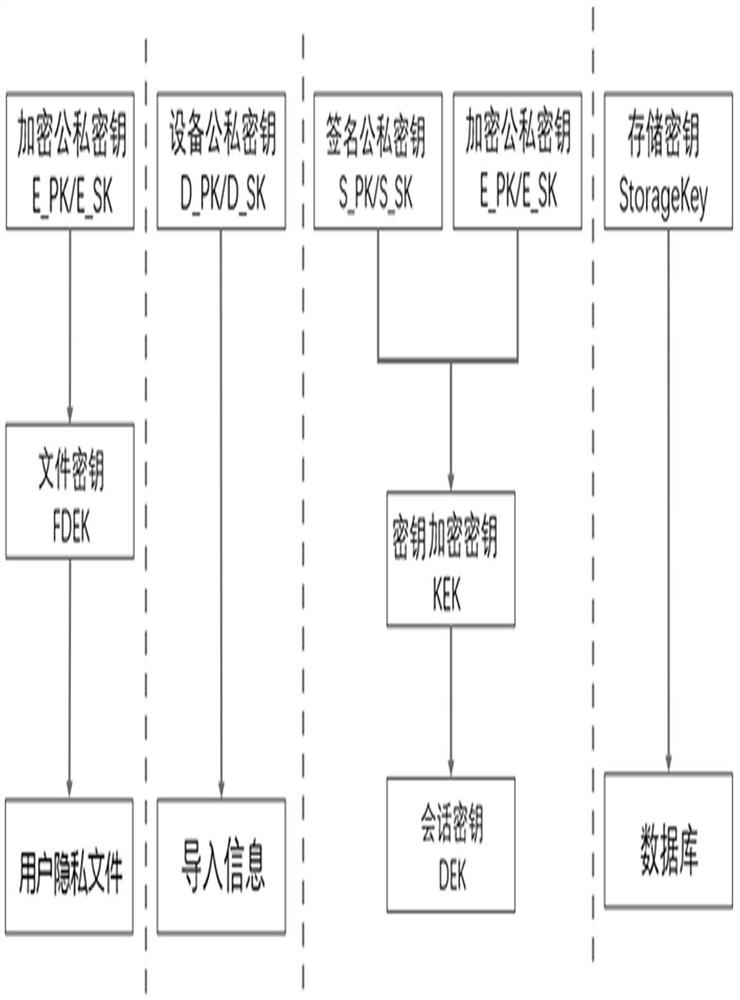
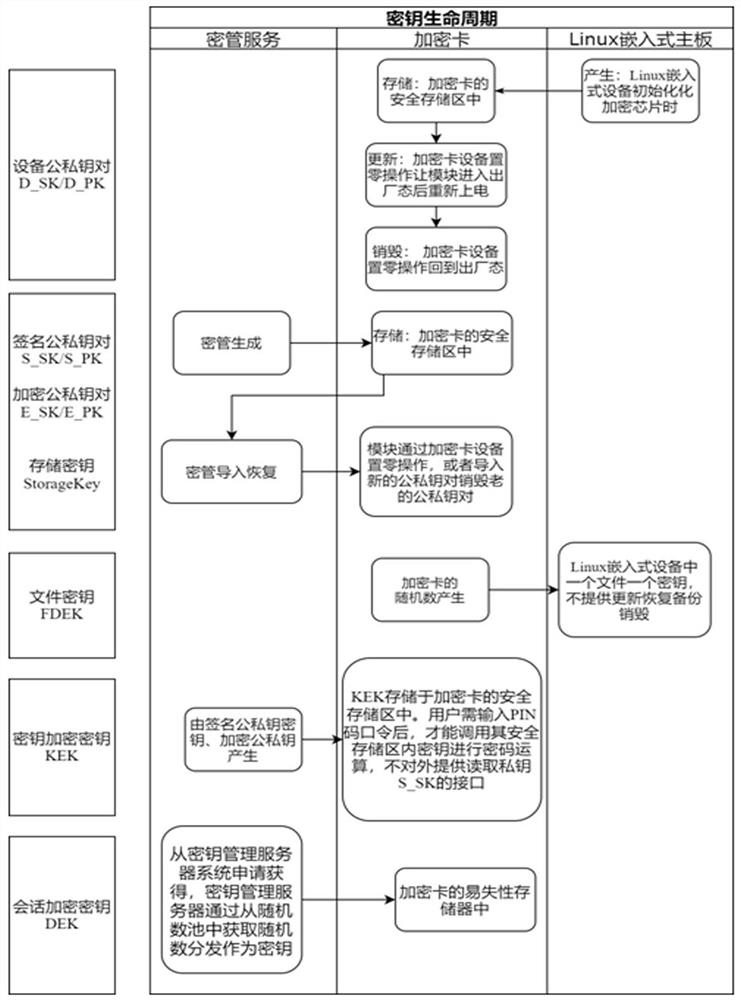
[0061] First, the present invention divides keys into multiple types, and different encryption methods are used for different keys; different algorithms are used to generate and store each type of key, and different strategies are used to update, backup, restore, and destroy the key , so as to reduce the risk of key leakage and ensure that the key information is not illegally obtained; even if the attacker uses brute force cracking methods and spends a lot of time and money to crack a key, it can only be a certain user at a certain point in time. Type of key, it is impossible to obtain other time points, other users, and other types of sensitive data by changing the key.
[0062] The technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings.
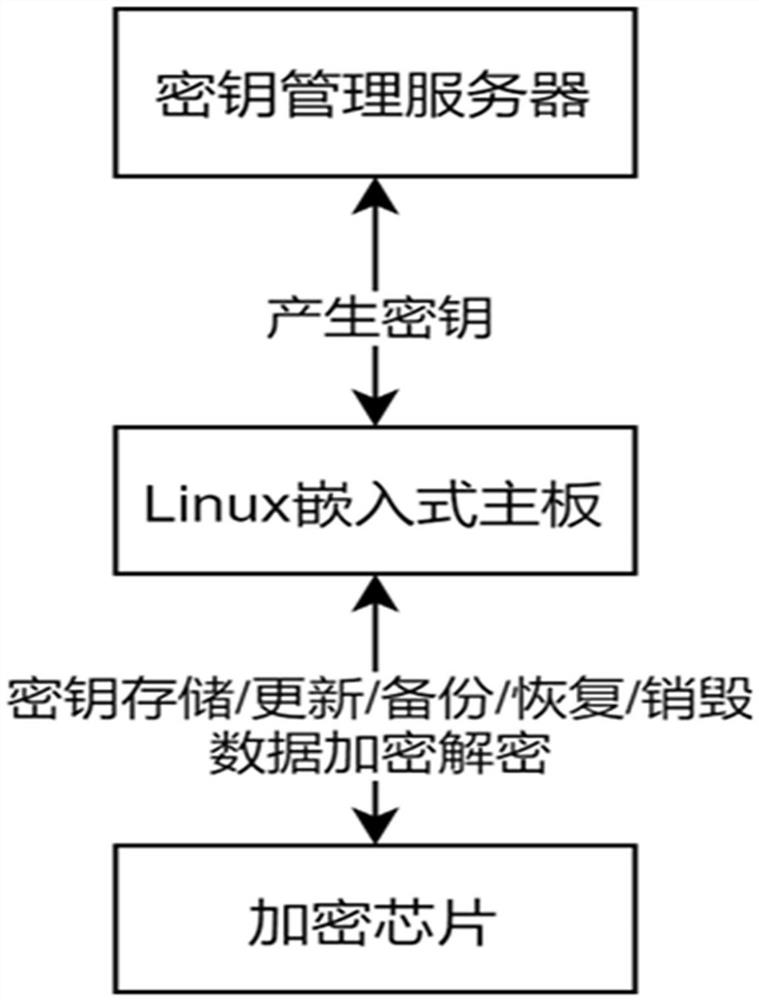
[0063] Such as figure 1 As shown, the present invention proposes a key management system. The system includes: a key management server, a Linux embedded business process...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com