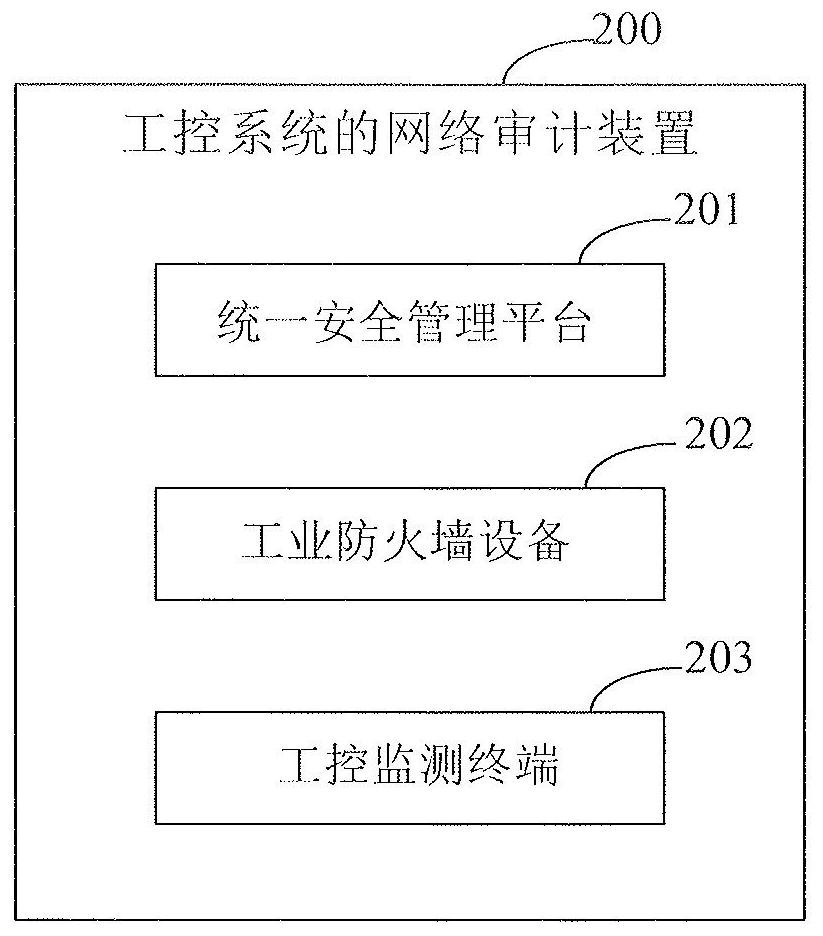
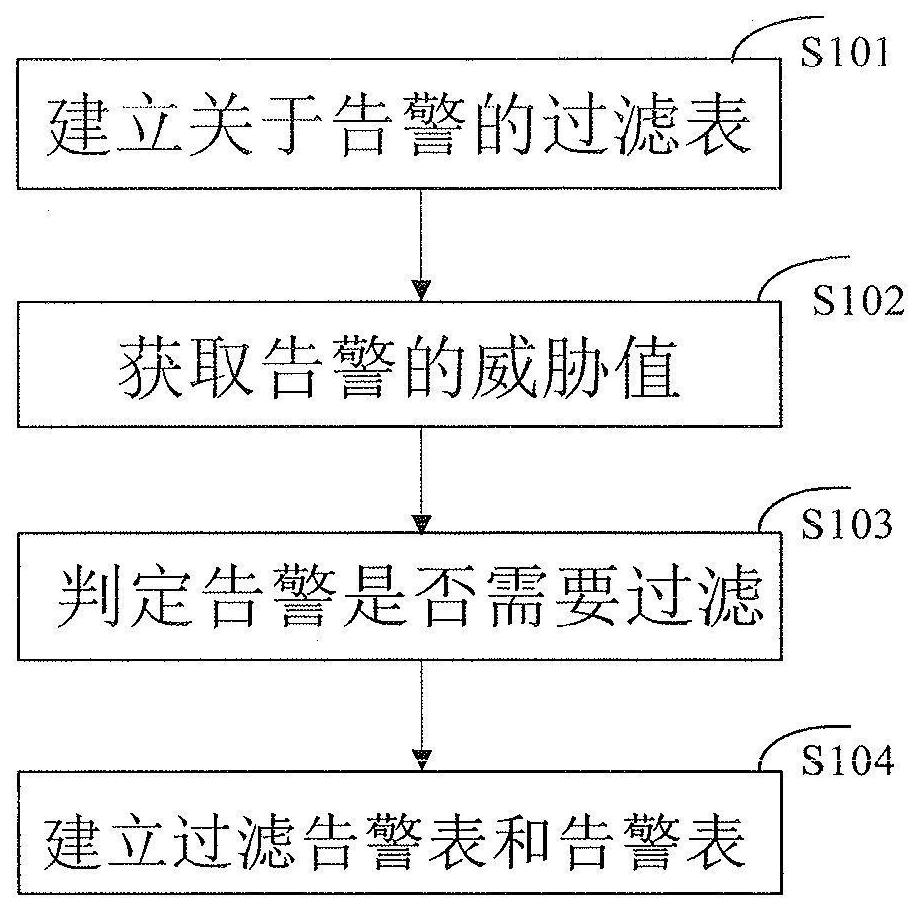
Network auditing method and device of industrial control system
An industrial control system and network technology, applied in transmission systems, electrical components, etc., can solve the problems of low risk level of read operations, no consideration of on-site asset conditions, and high-risk alarms divided by risk levels, so as to reduce the number of alarms and improve work efficiency. , the effect of reducing maintenance costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
[0104] In the following, specific illustrative examples will be described for ease of understanding.
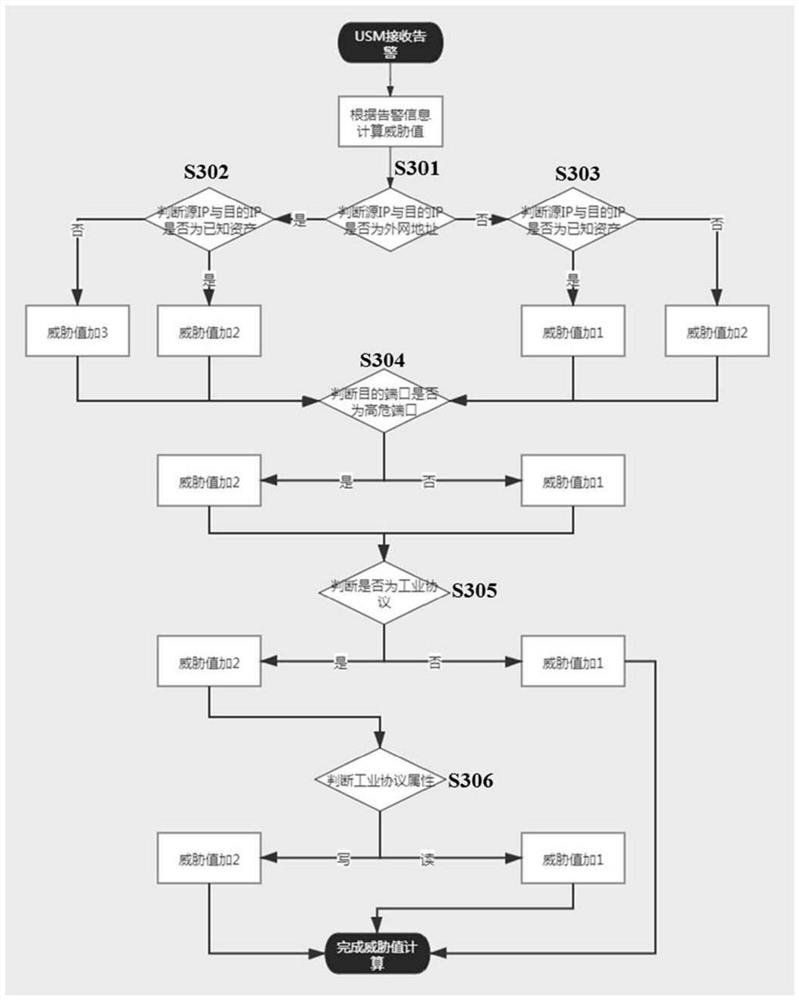
[0105] Five alarms A1 , A2 , A3 , A4 and A5 are received through the unified security management platform 102 . At this time, the five-tuple data including source IP, destination IP, destination port, industrial protocol, and industrial protocol function code of the five alarms A1, A2, A3, A4, and A5 are extracted, as shown in Table 2 below.
[0106] [Table 2]
[0107]
[0108] By extracting the quintuple data of each alarm A1-A5, and by querying the alarm threat table, it is known that it has the same data as the alarm A1, A4, and A5. Therefore, the total threat value in the alarm threat table is directly assigned to the alarm A1, A4 and A5, that is, the total threat value of alarm A1 is 9, the total threat value of alarm A4 is 4, and the total threat value of alarm A5 is 7.
[0109] For the alarms A2 and A3 that are not found in the alarm threat table, calculate the to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com