Power system communication message double encryption method, decryption method and message interaction system
A communication message and power system technology, applied in the field of power information system communication security, can solve problems such as crowding out system computing resources, affecting system communication capacity and response speed, communication task resource conflicts, etc., to ensure encryption efficiency and improve communication efficiency Stable, efficient and fast encryption effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
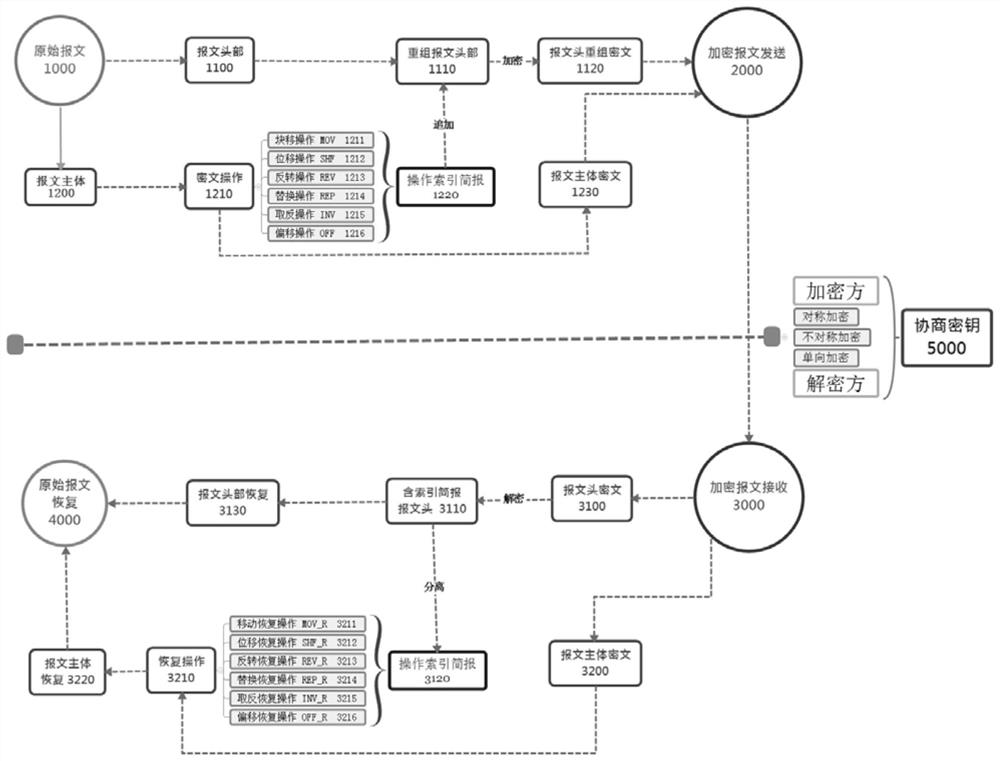
[0064] This embodiment introduces a double encryption method for power system communication messages, including:
[0065] Obtain the original communication message;
[0066] Carry out message separation on the original communication message to obtain the separated message header and message body;
[0067] According to the preset encryption operation rules, the data segment in the message body is encrypted, and the ciphertext of the message body and the operation index information corresponding to the encryption operation process are obtained;
[0068] Add the operation index information to the separated message header to obtain the reorganized message header;
[0069] Use the agreed key to encrypt the reassembled message header twice to obtain the reassembled ciphertext of the message header;
[0070] Recombine the ciphertext of the message body and the reorganized ciphertext of the message header to obtain the reassembled encrypted message for sending.
Embodiment 1-1
[0072] On the basis of Embodiment 1, this embodiment specifically introduces the message encryption process, mainly involving the following contents.
[0073] 1.1 Message Separation
[0074] The original communication message applicable to the present invention can be a message conforming to the IEC60870 / IEC61850 / IEC61970 / IEC61968 communication protocol, or a message with a message header.
[0075] For a message without a message header, when the message is separated, the message fragment with a set byte length can be intercepted from the message header in sequence, as the separated message header, and the rest as the message body.
[0076] 1.2 Message body encryption operation and operation index information generation
[0077] The encryption operation rules for encrypting the message body in the present invention can be: according to a randomly selected or preset operation type, a random or preset operation sequence, a random or preset operation start position, length, and ...
Embodiment 2
[0092] Based on the same inventive concept as Embodiment 1, this embodiment introduces a message decryption method capable of decrypting the communication message obtained by using the encryption method of Embodiment 1, including:
[0093] Obtain the reassembled encrypted message;
[0094] Separate the reassembled encrypted message to obtain the message header ciphertext and message body ciphertext;
[0095] Use the agreed key to decrypt the ciphertext of the message header to obtain the plaintext of the message header containing the operation index information;
[0096] Segment the header plaintext to obtain the original header plaintext and operation index information;
[0097] According to the encryption operation process recorded in the operation index information, according to the reverse order of the encryption operation sequence, the reverse recovery operation of the corresponding encryption operation is performed on the ciphertext of the message body in turn, and the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com