Method and device for constructing network security knowledge graph
A network security and knowledge graph technology, applied in neural learning methods, biological neural network models, neural architectures, etc., can solve the problems of reducing the efficiency and low accuracy of network security knowledge graph construction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
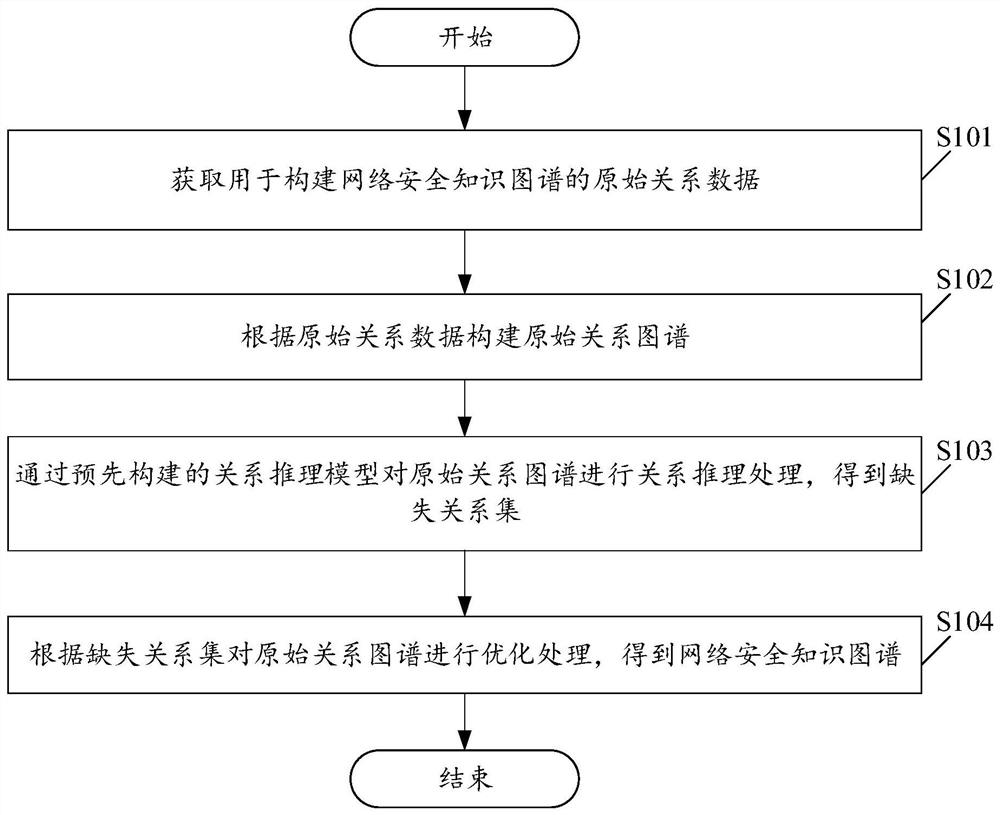
[0063] Please see figure 1 , figure 1 A schematic flowchart of a method for constructing a network security knowledge graph is provided for the embodiment of the present application. Among them, the construction method of the network security knowledge graph includes:
[0064] S101. Obtain original relational data used to construct a network security knowledge graph.
[0065] In the embodiment of the present application, when obtaining the original relational data, the security event data may be obtained first, and then the relational extraction processing is performed on the security event data to obtain the original relational data.
[0066] In the embodiment of the present application, the security event data includes various security event data such as phishing event data, remote control Trojan horse data, malware data, exploit data, website backdoor data, DDOS attack data, flow data, domain name data, and URL log data , external threat intelligence data, whois domain n...
Embodiment 2
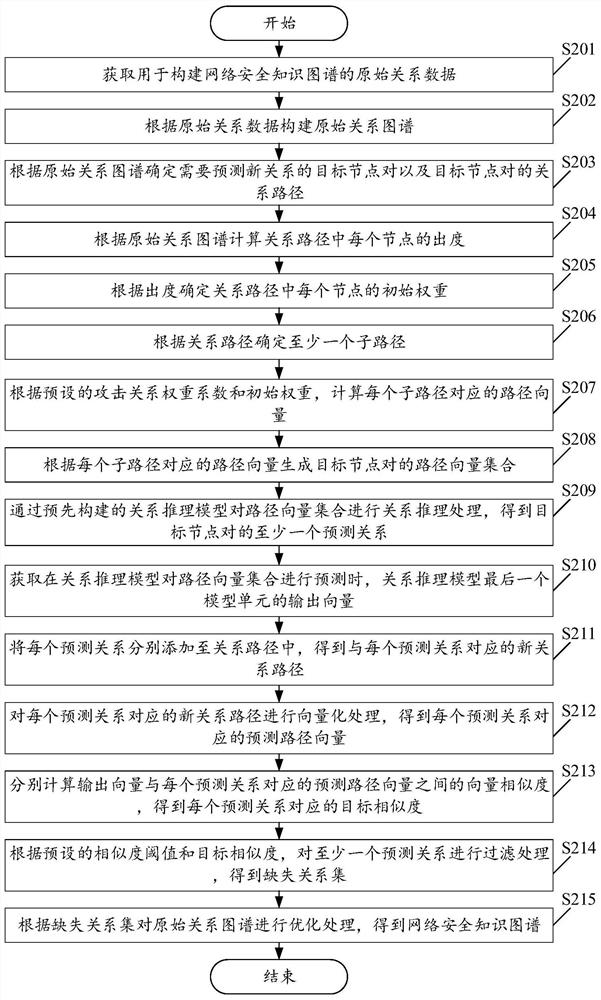
[0085] Please see figure 2 , figure 2 It is a schematic flow chart of a method for constructing a network security knowledge graph provided in the embodiment of the present application. Such as figure 2 As shown, wherein, the construction method of the network security knowledge graph includes:
[0086] S201. Obtain original relational data used to construct a network security knowledge graph.
[0087] As an optional implementation manner, obtaining the original relational data used to construct the network security knowledge map may include the following steps:
[0088] Obtain network security event data for building a network security knowledge graph;
[0089] The entity relationship extraction process is performed on the network security event data to obtain the original relationship data.
[0090] In the above embodiments, the original relational data includes various security event data such as phishing event data, remote control Trojan horse data, malware data, e...
Embodiment 3
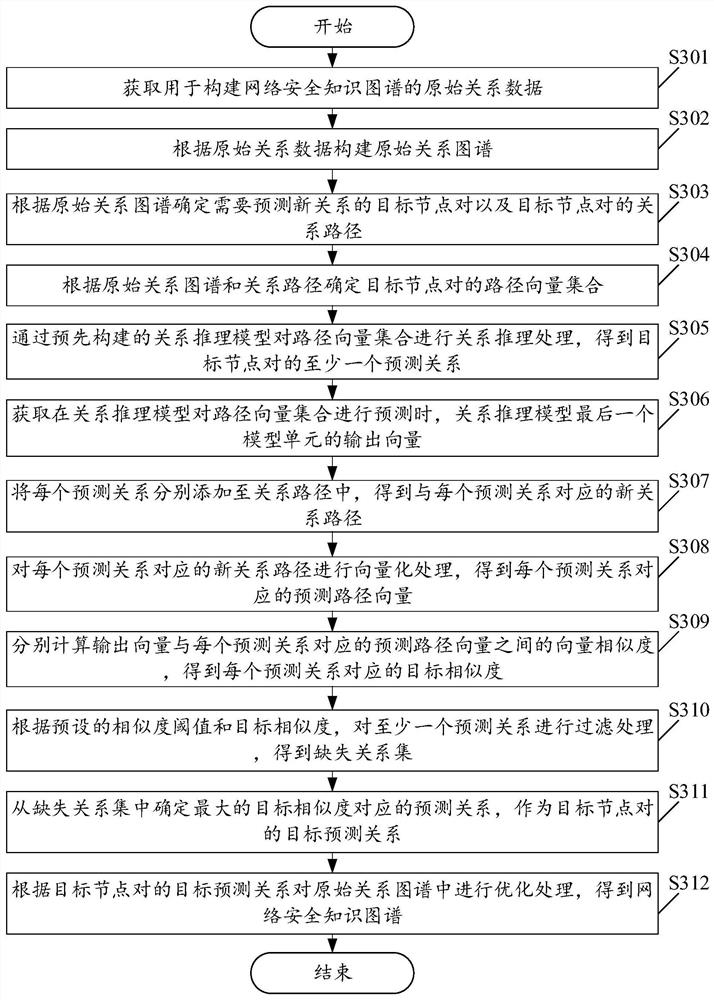
[0149] Please see image 3 , image 3 It is a schematic flow chart of a method for constructing a network security knowledge graph provided in the embodiment of the present application. Such as image 3 As shown, wherein, the construction method of the network security knowledge graph includes:
[0150] S301. Obtain original relational data used to construct a network security knowledge graph.
[0151]S302. Construct an original relationship graph according to the original relationship data.
[0152] S303. Determine target node pairs for which new relationships need to be predicted and relationship paths of the target node pairs according to the original relationship graph.
[0153] After step S303, the following steps are also included:
[0154] S304. Determine the path vector set of the target node pair according to the original relationship graph and the relationship path.
[0155] S305. Perform relational reasoning processing on the set of path vectors through a pre-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com