Method and system for improving alarm quality
A quality and alarm message technology, applied in the Internet field, can solve problems such as inability to fully understand and many alarm messages, and achieve the effects of improving alarm quality, efficiency, and pertinence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
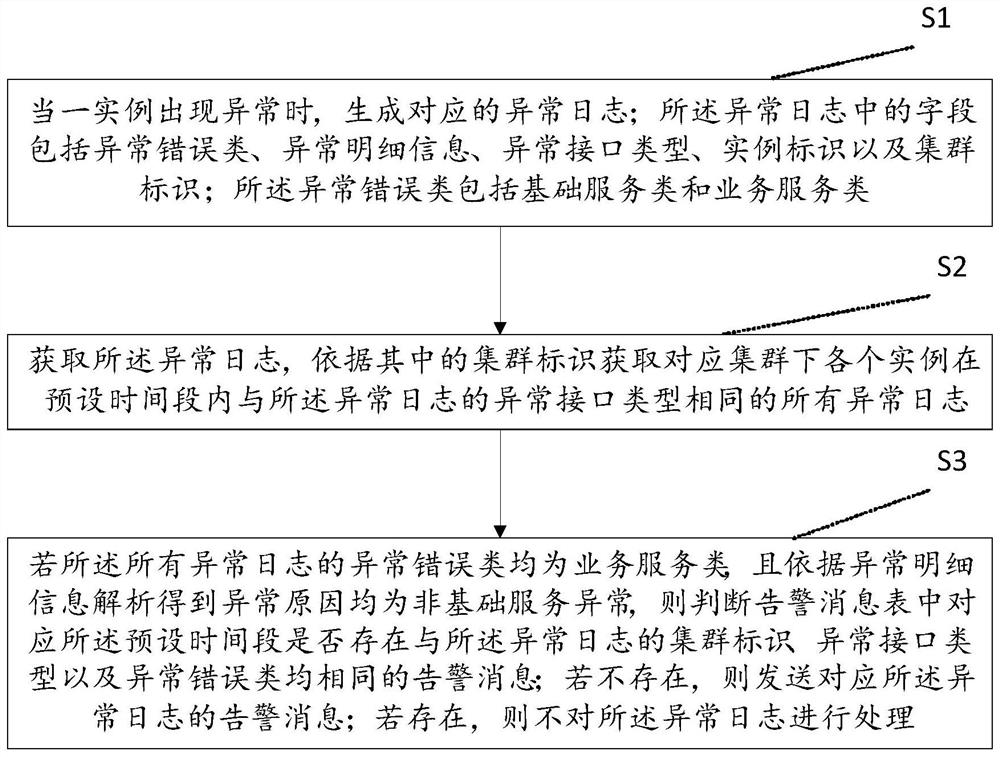
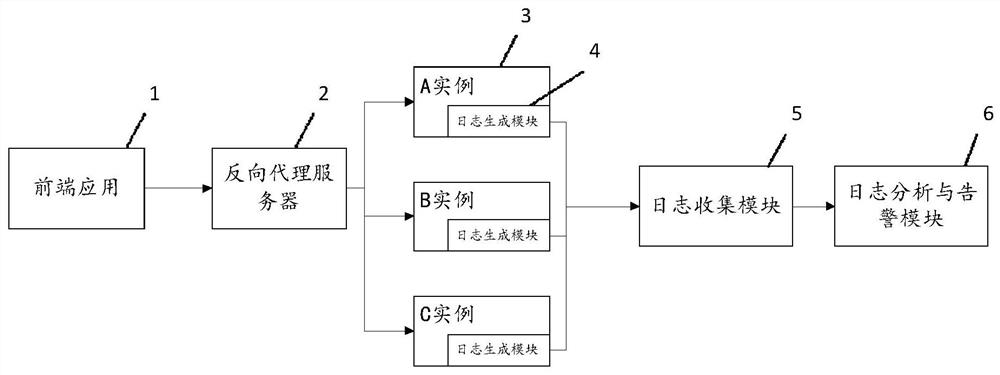
[0068] Please refer to figure 2 , the present embodiment provides a method for improving the quality of an alarm, which is applied to an existing interactive system between a server and a client. The system includes a sequentially connected front-end application 1 (client, etc.), a reverse proxy server 2 (nginx or SLB, etc.) and back-end applications (one or more WEB service application instances).
[0069] The method of this embodiment may include the following steps:
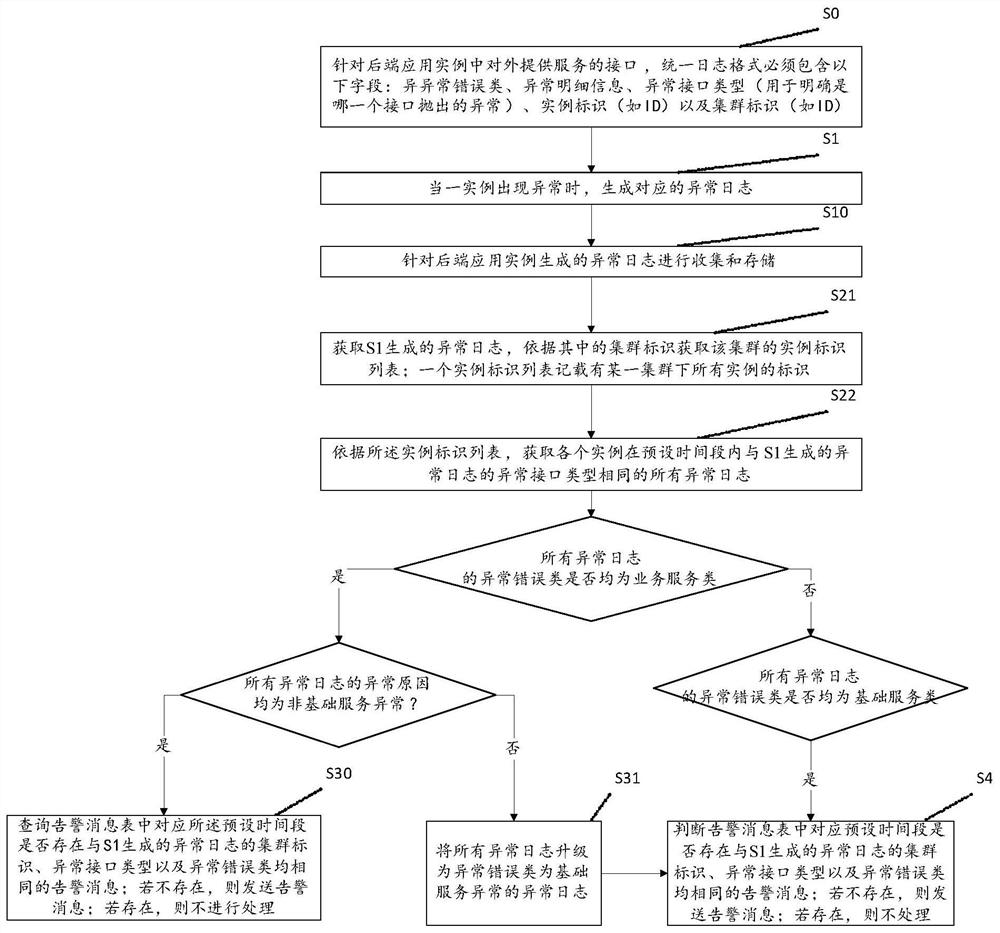
[0070] S0: Unify the standardization of the log format for the interface that provides external services in the back-end application instance (hereinafter referred to as the instance). Specifically, the logs that may have been in various formats were uniformly modified to include the following fields: exception error class, exception details, exception interface type (used to clarify which interface threw the exception), instance identifier (such as ID) And cluster identification (such as ID); wherein, the ...
Embodiment 2
[0098] This embodiment provides a specific application scenario corresponding to Embodiment 1:
[0099] There is a cluster in the account system of a certain company, which is called UC business cluster here, and there are three tomcat application instances under this cluster, which are instance A, instance B, and instance C. The function of the application instance mainly provides an interface for obtaining user information, which obtains user information from the mysql database and returns it to the caller (ie, the front end).
[0100] Assume that within 1 minute, there are five exception logs indicating that the interface for obtaining user information failed in instance A. (Assuming that the interface in the prior art has 3 abnormalities within 1 minute, an alarm prompt is required.
corresponding Embodiment 1
[0101] And corresponding to the method of embodiment one, then will carry out and comprise:
[0102] 1. If the contents of the five exception logs recorded in instance A are:
[0103] GetInfoClass (abnormal error class), own business error (abnormal detail information), GetInfo interface (interface type), instance A (instance id) and UC business cluster (cluster id).
[0104] 2. Obtain the instance ID list under the cluster according to the cluster ID in the exception log. At this time, the obtained instance ID list includes A instance, B instance, and C instance.
[0105] 3. According to the instance ID list in step 2, query the exception log of each instance ID related to the GetInfo interface within the time period. Assume that instance A occurs 5 times, instance B occurs 2 times, and instance C occurs 1 time. At this time, the following 3 scenarios may exist in the 8 exception logs:
[0106] 3.1 Scenario: These 8 exception logs are all business exceptions caused by the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com