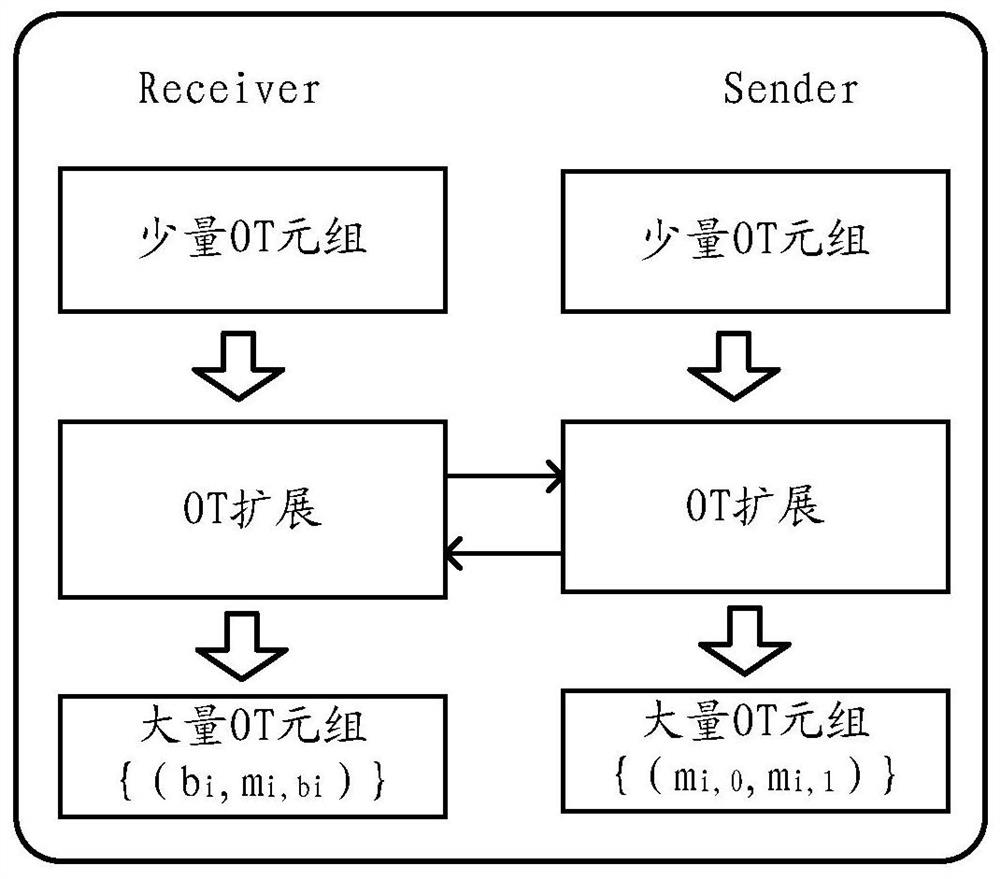
Data processing method and device for oblivious transfer (OT) extension protocol
A technology for extending protocols and data processing, applied in the computer field, which can solve problems such as increasing the amount of calculation and communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
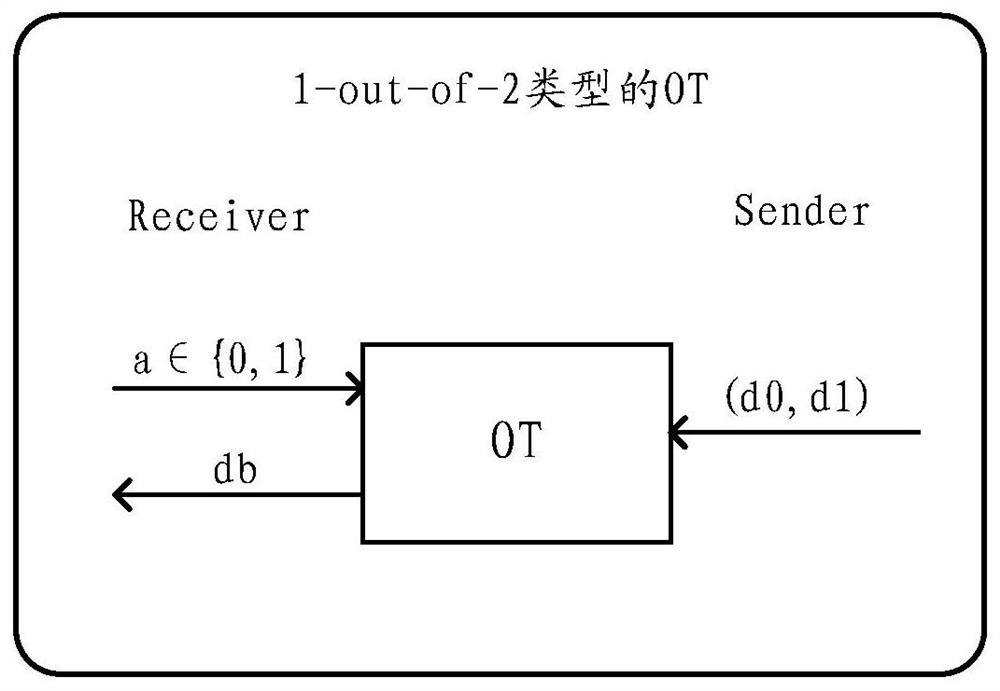
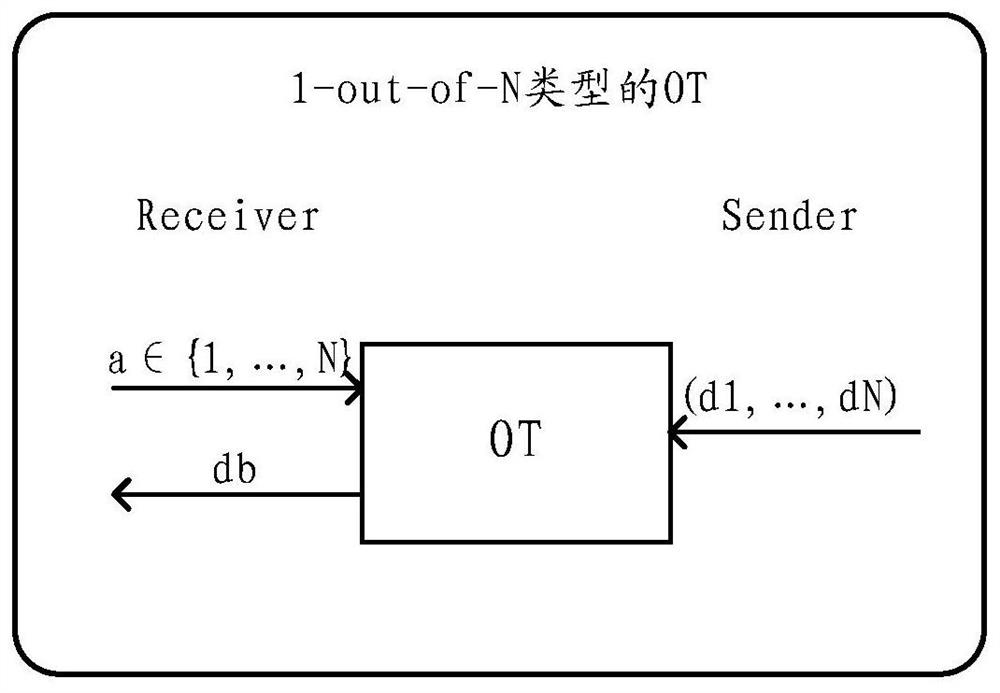
[0026] The aforementioned OT protocol can be divided into the following two types according to functions: 1-out-of-2 type and 1-out-of-N type. Figure 1a shows 1-out-of-2 type OT protocol, Figure 1b A 1-out-of-N type OT protocol is shown.
[0027] Figure 1a Among them, the input of the Receiver is the selection bit a∈{0,1}, and the input of the Sender is a pair of messages (d 0 , d 1 ), where d 0 、d 1 is the plaintext message to be sent (for example, a 128-bit bit string). Through the OT protocol, Receiver can finally obtain d a .
[0028] Obviously, through the OT protocol, the following two aspects of security can be satisfied: (1) Receiver selects the confidentiality of bit a, that is, through the OT protocol, the Sender cannot know which message the Receiver selects. (2) Sender is not selected message d 1-a confidentiality, that is, through...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com