Trusted IPSec module and VPN tunnel construction method
A tunnel and module technology, applied in the field of network security, can solve problems such as attacking VPN tunnels, stealing important information and sensitive resources, etc., and achieve the effects of reducing system load, improving communication efficiency, and ensuring communication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0052] Please refer to figure 1 , Embodiment 1 of the present application provides a trusted IPSec module applied to a terminal device, including:
[0053] REE function group 11, running in REE drive environment, including IPSec protocol encapsulation analysis module 111 and TCP / IP protocol stack 112;
[0054] TEE function group 12, running in TEE driver environment, including IPSec core module 121;
[0055] A storage module 13, the storage module is respectively connected with the IPSec protocol encapsulation analysis module and the IPSec core module.
[0056] The TEE-driven environment is a trusted execution environment, which can guarantee computing that is not interfered by the conventional operating system, so it is called "trusted". In a nutshell, TEE is an independent execution environment running in parallel with Rich OS, providing security services for the Rich OS environment. The TEE driver environment is implemented based on ARM TrustZone, which can access hardwa...
Embodiment 2
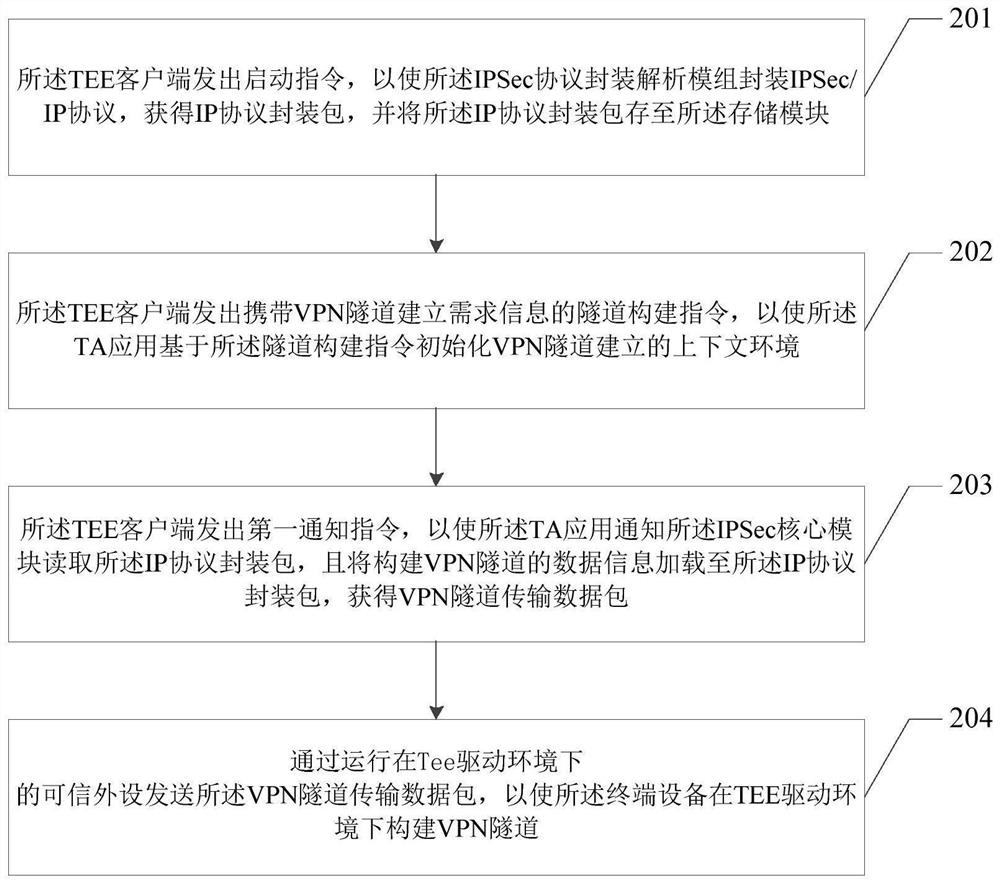
[0073] Please refer to figure 2 Embodiment 2 of the present application provides a method for constructing a VPN tunnel, which is applied to the IPSec module described in Embodiment 1, and the method includes:
[0074] Step 201: The TEE client issues a startup command, so that the IPSec protocol encapsulation analysis module encapsulates the IPSec / IP protocol, obtains an IP protocol encapsulation package, and stores the IP protocol encapsulation package in the storage module;
[0075] It should be pointed out that when the method in Embodiment 2 of the present application is implemented, a TEE client and a TA application need to be installed in the terminal device, the TEE client runs in the REE driver environment; the TA application runs in the TEE driver environment ; and the TEE client is interconnected with the TA application.
[0076] During the execution of this step, the user can first send an instruction to the TEE client to establish a VPN tunnel through direct or i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com